2017-04-25 09:24:51 +02:00
// Copyright 2017 The Gitea Authors. All rights reserved.
2022-11-27 19:20:29 +01:00
// SPDX-License-Identifier: MIT
2017-04-25 09:24:51 +02:00
2021-06-09 01:33:54 +02:00
package web
2017-04-25 09:24:51 +02:00
import (
2022-02-05 19:26:12 +01:00
gocontext "context"
2021-01-26 16:36:53 +01:00
"net/http"
2023-09-12 08:15:16 +02:00
"strings"
2017-04-25 09:24:51 +02:00
2023-09-18 01:32:56 +02:00
auth_model "code.gitea.io/gitea/models/auth"
2023-10-11 06:24:07 +02:00
"code.gitea.io/gitea/models/db"
2022-03-30 10:42:47 +02:00
"code.gitea.io/gitea/models/perm"
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
quota_model "code.gitea.io/gitea/models/quota"
2021-11-09 20:57:58 +01:00
"code.gitea.io/gitea/models/unit"
2017-04-25 09:24:51 +02:00
"code.gitea.io/gitea/modules/log"
2021-01-26 16:36:53 +01:00
"code.gitea.io/gitea/modules/metrics"
"code.gitea.io/gitea/modules/public"
2017-04-25 09:24:51 +02:00
"code.gitea.io/gitea/modules/setting"
2021-01-26 16:36:53 +01:00
"code.gitea.io/gitea/modules/storage"
2022-04-07 20:59:56 +02:00
"code.gitea.io/gitea/modules/structs"
2022-08-28 11:43:25 +02:00
"code.gitea.io/gitea/modules/templates"
2017-04-25 09:24:51 +02:00
"code.gitea.io/gitea/modules/validation"
2021-01-26 16:36:53 +01:00
"code.gitea.io/gitea/modules/web"
2023-09-12 08:15:16 +02:00
"code.gitea.io/gitea/modules/web/middleware"
2022-01-20 12:41:25 +01:00
"code.gitea.io/gitea/modules/web/routing"
2023-04-27 08:06:45 +02:00
"code.gitea.io/gitea/routers/common"
2021-06-09 01:33:54 +02:00
"code.gitea.io/gitea/routers/web/admin"
2022-01-02 14:12:35 +01:00
"code.gitea.io/gitea/routers/web/auth"
2023-04-03 12:06:57 +02:00
"code.gitea.io/gitea/routers/web/devtest"
2021-06-09 01:33:54 +02:00
"code.gitea.io/gitea/routers/web/events"
"code.gitea.io/gitea/routers/web/explore"
2022-03-26 10:04:22 +01:00
"code.gitea.io/gitea/routers/web/feed"
2022-05-04 13:56:20 +02:00
"code.gitea.io/gitea/routers/web/healthcheck"
2022-04-08 06:22:10 +02:00
"code.gitea.io/gitea/routers/web/misc"
2021-06-09 01:33:54 +02:00
"code.gitea.io/gitea/routers/web/org"
2023-04-28 02:08:47 +02:00
org_setting "code.gitea.io/gitea/routers/web/org/setting"
2021-06-09 01:33:54 +02:00
"code.gitea.io/gitea/routers/web/repo"
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
"code.gitea.io/gitea/routers/web/repo/actions"
[GITEA] Add support for shields.io-based badges
Adds a new `/{username}/{repo}/badges` family of routes, which redirect
to various shields.io badges. The goal is to not reimplement badge
generation, and delegate it to shields.io (or a similar service), which
are already used by many. This way, we get all the goodies that come
with it: different styles, colors, logos, you name it.
So these routes are just thin wrappers around shields.io that make it
easier to display the information we want. The URL is configurable via
`app.ini`, and is templatable, allowing to use alternative badge
generator services with slightly different URL patterns.
Additionally, for compatibility with GitHub, there's an
`/{username}/{repo}/actions/workflows/{workflow_file}/badge.svg` route
that works much the same way as on GitHub. Change the hostname in the
URL, and done.
Fixes gitea#5633, gitea#23688, and also fixes #126.
Work sponsored by Codeberg e.V.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit fcd0f61212d8febd4bdfc27e61a4e13cbdd16d49)
(cherry picked from commit 20d14f784490a880c51ca0f0a6a5988a01887635)
(cherry picked from commit 4359741431bb39de4cf24de8b0cfb513f5233f55)
(cherry picked from commit 35cff45eb86177e750cd22e82a201880a5efe045)
(cherry picked from commit 2fc0d0b8a302d24177a00ab48b42ce083b52e506)
2024-01-01 13:38:49 +01:00
"code.gitea.io/gitea/routers/web/repo/badges"
[FEAT] Repository flags
This implements "repository flags", a way for instance administrators to
assign custom flags to repositories. The idea is that custom templates
can look at these flags, and display banners based on them, Forgejo does
not provide anything built on top of it, just the foundation. The
feature is optional, and disabled by default. To enable it, set
`[repository].ENABLE_FLAGS = true`.
On the UI side, instance administrators will see a new "Manage flags"
tab on repositories, and a list of enabled tags (if any) on the
repository home page. The "Manage flags" page allows them to remove
existing flags, or add any new ones that are listed in
`[repository].SETTABLE_FLAGS`.
The model does not enforce that only the `SETTABLE_FLAGS` are present.
If the setting is changed, old flags may remain present in the database,
and anything that uses them, will still work. The repository flag
management page will allow an instance administrator to remove them, but
not set them, once removed.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit ba735ce2228f8dd7ca105e94b9baa1be058ebe37)
(cherry picked from commit f09f6e029b4fb2714b86cd32dc19255078ecc0ee)
(cherry picked from commit 2f8b0414892f6099f519bda63a9e0fbc8ba6cfc7)
(cherry picked from commit d3186ee5f41fac896c7d2341402fcd39dd250bf1)
2024-01-04 14:28:19 +01:00
repo_flags "code.gitea.io/gitea/routers/web/repo/flags"
2023-04-28 02:08:47 +02:00
repo_setting "code.gitea.io/gitea/routers/web/repo/setting"
2024-05-08 15:44:57 +02:00
"code.gitea.io/gitea/routers/web/shared/project"
2021-06-09 01:33:54 +02:00
"code.gitea.io/gitea/routers/web/user"
2022-01-02 14:12:35 +01:00
user_setting "code.gitea.io/gitea/routers/web/user/setting"
"code.gitea.io/gitea/routers/web/user/setting/security"
auth_service "code.gitea.io/gitea/services/auth"
2024-02-27 08:12:22 +01:00
"code.gitea.io/gitea/services/context"
2021-04-06 21:44:05 +02:00
"code.gitea.io/gitea/services/forms"
2021-04-09 00:25:57 +02:00
"code.gitea.io/gitea/services/lfs"
2017-04-25 09:24:51 +02:00
2021-11-17 13:34:35 +01:00
_ "code.gitea.io/gitea/modules/session" // to registers all internal adapters
2019-07-17 03:04:37 +02:00
2024-08-27 01:47:10 +02:00
"code.forgejo.org/go-chi/captcha"
2023-09-12 08:15:16 +02:00
chi_middleware "github.com/go-chi/chi/v5/middleware"
2021-03-04 02:25:30 +01:00
"github.com/go-chi/cors"
2023-10-01 00:09:25 +02:00
"github.com/klauspost/compress/gzhttp"
2021-01-26 16:36:53 +01:00
"github.com/prometheus/client_golang/prometheus"
2017-04-25 09:24:51 +02:00
)
2024-05-25 23:49:20 +02:00
var GzipMinSize = gzhttp . DefaultMinSize
2023-12-25 13:13:18 +01:00
// optionsCorsHandler return a http handler which sets CORS options if enabled by config, it blocks non-CORS OPTIONS requests.
func optionsCorsHandler ( ) func ( next http . Handler ) http . Handler {
var corsHandler func ( next http . Handler ) http . Handler
2021-05-30 12:25:11 +02:00
if setting . CORSConfig . Enabled {
2023-12-25 13:13:18 +01:00
corsHandler = cors . Handler ( cors . Options {
AllowedOrigins : setting . CORSConfig . AllowDomain ,
2021-05-30 12:25:11 +02:00
AllowedMethods : setting . CORSConfig . Methods ,
AllowCredentials : setting . CORSConfig . AllowCredentials ,
2022-11-11 07:39:27 +01:00
AllowedHeaders : setting . CORSConfig . Headers ,
2021-05-30 12:25:11 +02:00
MaxAge : int ( setting . CORSConfig . MaxAge . Seconds ( ) ) ,
} )
}
2021-06-09 01:33:54 +02:00
return func ( next http . Handler ) http . Handler {
2023-12-25 13:13:18 +01:00
return http . HandlerFunc ( func ( w http . ResponseWriter , r * http . Request ) {
if r . Method == http . MethodOptions {
if corsHandler != nil && r . Header . Get ( "Access-Control-Request-Method" ) != "" {
corsHandler ( next ) . ServeHTTP ( w , r )
} else {
// it should explicitly deny OPTIONS requests if CORS handler is not executed, to avoid the next GET/POST handler being incorrectly called by the OPTIONS request
w . WriteHeader ( http . StatusMethodNotAllowed )
}
return
}
// for non-OPTIONS requests, call the CORS handler to add some related headers like "Vary"
if corsHandler != nil {
corsHandler ( next ) . ServeHTTP ( w , r )
} else {
next . ServeHTTP ( w , r )
}
} )
2021-06-09 01:33:54 +02:00
}
2021-01-26 16:36:53 +01:00
}
2017-04-25 09:24:51 +02:00
2022-03-28 06:46:28 +02:00
// The OAuth2 plugin is expected to be executed first, as it must ignore the user id stored
// in the session (if there is a user id stored in session other plugins might return the user
// object for that id).
//
// The Session plugin is expected to be executed second, in order to skip authentication
// for users that have already signed in.
func buildAuthGroup ( ) * auth_service . Group {
2024-05-11 16:55:49 +02:00
group := auth_service . NewGroup ( )
group . Add ( & auth_service . OAuth2 { } ) // FIXME: this should be removed and only applied in download and oauth related routers
group . Add ( & auth_service . Basic { } ) // FIXME: this should be removed and only applied in download and git/lfs routers
2022-03-28 06:46:28 +02:00
if setting . Service . EnableReverseProxyAuth {
2024-05-11 16:55:49 +02:00
group . Add ( & auth_service . ReverseProxy { } ) // reverseproxy should before Session, otherwise the header will be ignored if user has login
2022-03-28 06:46:28 +02:00
}
2024-05-11 16:55:49 +02:00
group . Add ( & auth_service . Session { } )
2023-09-18 01:32:56 +02:00
2023-10-11 06:24:07 +02:00
if setting . IsWindows && auth_model . IsSSPIEnabled ( db . DefaultContext ) {
2023-09-18 01:32:56 +02:00
group . Add ( & auth_service . SSPI { } ) // it MUST be the last, see the comment of SSPI
}
2022-03-28 06:46:28 +02:00
return group
}
2023-09-12 08:15:16 +02:00
func webAuth ( authMethod auth_service . Method ) func ( * context . Context ) {
return func ( ctx * context . Context ) {
ar , err := common . AuthShared ( ctx . Base , ctx . Session , authMethod )
if err != nil {
log . Error ( "Failed to verify user: %v" , err )
2024-10-07 18:11:07 +02:00
ctx . Error ( http . StatusUnauthorized , ctx . Locale . TrString ( "auth.unauthorized_credentials" , "https://codeberg.org/forgejo/forgejo/issues/2809" ) )
2023-09-12 08:15:16 +02:00
return
}
ctx . Doer = ar . Doer
ctx . IsSigned = ar . Doer != nil
ctx . IsBasicAuth = ar . IsBasicAuth
if ctx . Doer == nil {
// ensure the session uid is deleted
_ = ctx . Session . Delete ( "uid" )
}
2024-09-18 09:17:25 +02:00
ctx . Csrf . PrepareForSessionUser ( ctx )
2023-09-12 08:15:16 +02:00
}
}
// verifyAuthWithOptions checks authentication according to options
func verifyAuthWithOptions ( options * common . VerifyOptions ) func ( ctx * context . Context ) {
return func ( ctx * context . Context ) {
// Check prohibit login users.
if ctx . IsSigned {
if ! ctx . Doer . IsActive && setting . Service . RegisterEmailConfirm {
ctx . Data [ "Title" ] = ctx . Tr ( "auth.active_your_account" )
ctx . HTML ( http . StatusOK , "user/auth/activate" )
return
}
if ! ctx . Doer . IsActive || ctx . Doer . ProhibitLogin {
log . Info ( "Failed authentication attempt for %s from %s" , ctx . Doer . Name , ctx . RemoteAddr ( ) )
ctx . Data [ "Title" ] = ctx . Tr ( "auth.prohibit_login" )
ctx . HTML ( http . StatusOK , "user/auth/prohibit_login" )
return
}
if ctx . Doer . MustChangePassword {
if ctx . Req . URL . Path != "/user/settings/change_password" {
if strings . HasPrefix ( ctx . Req . UserAgent ( ) , "git" ) {
2024-02-14 22:48:45 +01:00
ctx . Error ( http . StatusUnauthorized , ctx . Locale . TrString ( "auth.must_change_password" ) )
2023-09-12 08:15:16 +02:00
return
}
ctx . Data [ "Title" ] = ctx . Tr ( "auth.must_change_password" )
ctx . Data [ "ChangePasscodeLink" ] = setting . AppSubURL + "/user/change_password"
if ctx . Req . URL . Path != "/user/events" {
middleware . SetRedirectToCookie ( ctx . Resp , setting . AppSubURL + ctx . Req . URL . RequestURI ( ) )
}
ctx . Redirect ( setting . AppSubURL + "/user/settings/change_password" )
return
}
} else if ctx . Req . URL . Path == "/user/settings/change_password" {
// make sure that the form cannot be accessed by users who don't need this
ctx . Redirect ( setting . AppSubURL + "/" )
return
}
}
// Redirect to dashboard (or alternate location) if user tries to visit any non-login page.
if options . SignOutRequired && ctx . IsSigned && ctx . Req . URL . RequestURI ( ) != "/" {
ctx . RedirectToFirst ( ctx . FormString ( "redirect_to" ) )
return
}
if ! options . SignOutRequired && ! options . DisableCSRF && ctx . Req . Method == "POST" {
ctx . Csrf . Validate ( ctx )
if ctx . Written ( ) {
return
}
}
if options . SignInRequired {
if ! ctx . IsSigned {
if ctx . Req . URL . Path != "/user/events" {
middleware . SetRedirectToCookie ( ctx . Resp , setting . AppSubURL + ctx . Req . URL . RequestURI ( ) )
}
ctx . Redirect ( setting . AppSubURL + "/user/login" )
return
} else if ! ctx . Doer . IsActive && setting . Service . RegisterEmailConfirm {
ctx . Data [ "Title" ] = ctx . Tr ( "auth.active_your_account" )
ctx . HTML ( http . StatusOK , "user/auth/activate" )
return
}
}
// Redirect to log in page if auto-signin info is provided and has not signed in.
if ! options . SignOutRequired && ! ctx . IsSigned &&
2023-10-14 02:56:41 +02:00
ctx . GetSiteCookie ( setting . CookieRememberName ) != "" {
2023-09-12 08:15:16 +02:00
if ctx . Req . URL . Path != "/user/events" {
middleware . SetRedirectToCookie ( ctx . Resp , setting . AppSubURL + ctx . Req . URL . RequestURI ( ) )
}
ctx . Redirect ( setting . AppSubURL + "/user/login" )
return
}
if options . AdminRequired {
if ! ctx . Doer . IsAdmin {
ctx . Error ( http . StatusForbidden )
return
}
ctx . Data [ "PageIsAdmin" ] = true
}
}
}
2023-04-28 02:08:47 +02:00
func ctxDataSet ( args ... any ) func ( ctx * context . Context ) {
return func ( ctx * context . Context ) {
for i := 0 ; i < len ( args ) ; i += 2 {
ctx . Data [ args [ i ] . ( string ) ] = args [ i + 1 ]
}
}
}
2021-06-09 01:33:54 +02:00
// Routes returns all web routes
2023-06-18 09:59:09 +02:00
func Routes ( ) * web . Route {
2021-05-04 23:48:31 +02:00
routes := web . NewRoute ( )
2017-04-25 09:24:51 +02:00
2023-04-27 08:06:45 +02:00
routes . Head ( "/" , misc . DummyOK ) // for health check - doesn't need to be passed through gzip handler
2023-12-25 13:13:18 +01:00
routes . Methods ( "GET, HEAD, OPTIONS" , "/assets/*" , optionsCorsHandler ( ) , public . FileHandlerFunc ( ) )
2023-07-21 00:43:49 +02:00
routes . Methods ( "GET, HEAD" , "/avatars/*" , storageHandler ( setting . Avatar . Storage , "avatars" , storage . Avatars ) )
routes . Methods ( "GET, HEAD" , "/repo-avatars/*" , storageHandler ( setting . RepoAvatar . Storage , "repo-avatars" , storage . RepoAvatars ) )
routes . Methods ( "GET, HEAD" , "/apple-touch-icon.png" , misc . StaticRedirect ( "/assets/img/apple-touch-icon.png" ) )
routes . Methods ( "GET, HEAD" , "/apple-touch-icon-precomposed.png" , misc . StaticRedirect ( "/assets/img/apple-touch-icon.png" ) )
routes . Methods ( "GET, HEAD" , "/favicon.ico" , misc . StaticRedirect ( "/assets/img/favicon.png" ) )
2021-05-04 23:48:31 +02:00
2023-04-30 14:22:23 +02:00
_ = templates . HTMLRenderer ( )
2023-05-04 08:36:34 +02:00
var mid [ ] any
2021-05-04 23:48:31 +02:00
2021-01-26 16:36:53 +01:00
if setting . EnableGzip {
2024-05-25 23:49:20 +02:00
wrapper , err := gzhttp . NewWrapper ( gzhttp . RandomJitter ( 32 , 0 , false ) , gzhttp . MinSize ( GzipMinSize ) )
2021-01-26 16:36:53 +01:00
if err != nil {
2023-10-01 00:09:25 +02:00
log . Fatal ( "gzhttp.NewWrapper failed: %v" , err )
2021-01-26 16:36:53 +01:00
}
2023-10-01 00:09:25 +02:00
mid = append ( mid , wrapper )
2021-01-26 16:36:53 +01:00
}
2021-01-27 15:56:54 +01:00
if setting . Service . EnableCaptcha {
2021-05-04 23:48:31 +02:00
// The captcha http.Handler should only fire on /captcha/* so we can just mount this on that url
2024-08-27 01:47:10 +02:00
routes . Methods ( "GET,HEAD" , "/captcha/*" , append ( mid , captcha . Server ( captcha . StdWidth , captcha . StdHeight ) . ServeHTTP ) ... )
2021-01-27 18:46:35 +01:00
}
2021-01-26 16:36:53 +01:00
if setting . Metrics . Enabled {
2023-04-27 08:06:45 +02:00
prometheus . MustRegister ( metrics . NewCollector ( ) )
2023-05-04 08:36:34 +02:00
routes . Get ( "/metrics" , append ( mid , Metrics ) ... )
2021-01-26 16:36:53 +01:00
}
2024-04-19 15:43:56 +02:00
routes . Methods ( "GET,HEAD" , "/robots.txt" , append ( mid , misc . RobotsTxt ) ... )
2023-04-27 08:06:45 +02:00
routes . Get ( "/ssh_info" , misc . SSHInfo )
2022-05-04 13:56:20 +02:00
routes . Get ( "/api/healthz" , healthcheck . Check )
2023-05-04 08:36:34 +02:00
mid = append ( mid , common . Sessioner ( ) , context . Contexter ( ) )
2021-05-04 23:48:31 +02:00
2021-06-09 19:53:16 +02:00
// Get user from session if logged in.
2023-09-12 08:15:16 +02:00
mid = append ( mid , webAuth ( buildAuthGroup ( ) ) )
2021-06-09 19:53:16 +02:00
2021-05-04 23:48:31 +02:00
// GetHead allows a HEAD request redirect to GET if HEAD method is not defined for that route
2023-09-12 08:15:16 +02:00
mid = append ( mid , chi_middleware . GetHead )
2021-05-04 23:48:31 +02:00
2021-01-26 16:36:53 +01:00
if setting . API . EnableSwagger {
2023-04-27 08:06:45 +02:00
// Note: The route is here but no in API routes because it renders a web page
2023-05-04 08:36:34 +02:00
routes . Get ( "/api/swagger" , append ( mid , misc . Swagger ) ... ) // Render V1 by default
2023-02-07 11:23:49 +01:00
routes . Get ( "/api/forgejo/swagger" , append ( mid , misc . SwaggerForgejo ) ... )
2021-01-26 16:36:53 +01:00
}
2021-05-04 23:48:31 +02:00
// TODO: These really seem like things that could be folded into Contexter or as helper functions
2023-05-04 08:36:34 +02:00
mid = append ( mid , user . GetNotificationCount )
mid = append ( mid , repo . GetActiveStopwatch )
mid = append ( mid , goGet )
2021-01-26 16:36:53 +01:00
2021-05-04 23:48:31 +02:00
others := web . NewRoute ( )
2023-05-04 08:36:34 +02:00
others . Use ( mid ... )
2023-04-27 08:06:45 +02:00
registerRoutes ( others )
2021-05-04 23:48:31 +02:00
routes . Mount ( "" , others )
return routes
2020-10-19 23:03:08 +02:00
}
2023-11-02 15:14:33 +01:00
var ignSignInAndCsrf = verifyAuthWithOptions ( & common . VerifyOptions { DisableCSRF : true } )
2023-04-27 08:06:45 +02:00
// registerRoutes register routes
func registerRoutes ( m * web . Route ) {
2023-09-12 08:15:16 +02:00
reqSignIn := verifyAuthWithOptions ( & common . VerifyOptions { SignInRequired : true } )
reqSignOut := verifyAuthWithOptions ( & common . VerifyOptions { SignOutRequired : true } )
2023-05-04 14:07:15 +02:00
// TODO: rename them to "optSignIn", which means that the "sign-in" could be optional, depends on the VerifyOptions (RequireSignInView)
2023-09-12 08:15:16 +02:00
ignSignIn := verifyAuthWithOptions ( & common . VerifyOptions { SignInRequired : setting . Service . RequireSignInView } )
ignExploreSignIn := verifyAuthWithOptions ( & common . VerifyOptions { SignInRequired : setting . Service . RequireSignInView || setting . Service . Explore . RequireSigninView } )
2023-11-02 15:14:33 +01:00
2017-04-25 09:24:51 +02:00
validation . AddBindingRules ( )
2022-02-09 21:33:36 +01:00
linkAccountEnabled := func ( ctx * context . Context ) {
2024-01-28 13:36:44 +01:00
if ! setting . Service . EnableOpenIDSignIn && ! setting . Service . EnableOpenIDSignUp && ! setting . OAuth2 . Enabled {
2022-02-09 21:33:36 +01:00
ctx . Error ( http . StatusForbidden )
return
}
}
2017-08-19 17:34:49 +02:00
openIDSignInEnabled := func ( ctx * context . Context ) {
if ! setting . Service . EnableOpenIDSignIn {
2021-04-05 17:30:52 +02:00
ctx . Error ( http . StatusForbidden )
2017-08-19 17:34:49 +02:00
return
}
}
openIDSignUpEnabled := func ( ctx * context . Context ) {
if ! setting . Service . EnableOpenIDSignUp {
2021-04-05 17:30:52 +02:00
ctx . Error ( http . StatusForbidden )
2017-08-19 17:34:49 +02:00
return
}
}
2024-11-12 22:33:35 +01:00
oauth2Enabled := func ( ctx * context . Context ) {
if ! setting . OAuth2 . Enabled {
ctx . Error ( http . StatusForbidden )
return
}
}
2019-12-15 15:20:08 +01:00
reqMilestonesDashboardPageEnabled := func ( ctx * context . Context ) {
if ! setting . Service . ShowMilestonesDashboardPage {
2021-04-05 17:30:52 +02:00
ctx . Error ( http . StatusForbidden )
2019-12-15 15:20:08 +01:00
return
}
}
2021-02-11 18:34:34 +01:00
// webhooksEnabled requires webhooks to be enabled by admin.
webhooksEnabled := func ( ctx * context . Context ) {
if setting . DisableWebhooks {
2021-04-05 17:30:52 +02:00
ctx . Error ( http . StatusForbidden )
2021-02-11 18:34:34 +01:00
return
}
}
2021-06-06 01:59:27 +02:00
lfsServerEnabled := func ( ctx * context . Context ) {
if ! setting . LFS . StartServer {
ctx . Error ( http . StatusNotFound )
return
}
}
2022-05-09 20:20:21 +02:00
federationEnabled := func ( ctx * context . Context ) {
if ! setting . Federation . Enabled {
ctx . Error ( http . StatusNotFound )
return
}
}
2022-07-31 18:57:02 +02:00
dlSourceEnabled := func ( ctx * context . Context ) {
if setting . Repository . DisableDownloadSourceArchives {
ctx . Error ( http . StatusNotFound )
return
}
}
2022-10-28 17:17:38 +02:00
sitemapEnabled := func ( ctx * context . Context ) {
2023-04-23 01:38:25 +02:00
if ! setting . Other . EnableSitemap {
2022-10-28 17:17:38 +02:00
ctx . Error ( http . StatusNotFound )
return
}
}
2022-11-20 15:08:38 +01:00
packagesEnabled := func ( ctx * context . Context ) {
if ! setting . Packages . Enabled {
ctx . Error ( http . StatusForbidden )
return
}
}
2022-11-21 06:14:58 +01:00
feedEnabled := func ( ctx * context . Context ) {
2023-04-23 01:38:25 +02:00
if ! setting . Other . EnableFeed {
2022-11-21 06:14:58 +01:00
ctx . Error ( http . StatusNotFound )
return
}
}
2023-07-29 16:13:24 +02:00
reqUnitAccess := func ( unitType unit . Type , accessMode perm . AccessMode , ignoreGlobal bool ) func ( ctx * context . Context ) {
2023-05-06 11:39:06 +02:00
return func ( ctx * context . Context ) {
2023-07-29 16:13:24 +02:00
// only check global disabled units when ignoreGlobal is false
if ! ignoreGlobal && unitType . UnitGlobalDisabled ( ) {
2023-05-06 11:39:06 +02:00
ctx . NotFound ( unitType . String ( ) , nil )
return
}
if ctx . ContextUser == nil {
ctx . NotFound ( unitType . String ( ) , nil )
return
}
if ctx . ContextUser . IsOrganization ( ) {
if ctx . Org . Organization . UnitPermission ( ctx , ctx . Doer , unitType ) < accessMode {
ctx . NotFound ( unitType . String ( ) , nil )
return
}
}
}
}
2023-12-25 08:28:59 +01:00
addSettingsVariablesRoutes := func ( ) {
2023-06-21 00:54:15 +02:00
m . Group ( "/variables" , func ( ) {
m . Get ( "" , repo_setting . Variables )
m . Post ( "/new" , web . Bind ( forms . EditVariableForm { } ) , repo_setting . VariableCreate )
m . Post ( "/{variable_id}/edit" , web . Bind ( forms . EditVariableForm { } ) , repo_setting . VariableUpdate )
m . Post ( "/{variable_id}/delete" , repo_setting . VariableDelete )
} )
}
2023-04-28 02:08:47 +02:00
addSettingsSecretsRoutes := func ( ) {
m . Group ( "/secrets" , func ( ) {
m . Get ( "" , repo_setting . Secrets )
m . Post ( "" , web . Bind ( forms . AddSecretForm { } ) , repo_setting . SecretsPost )
m . Post ( "/delete" , repo_setting . SecretsDelete )
} )
}
addSettingsRunnersRoutes := func ( ) {
m . Group ( "/runners" , func ( ) {
m . Get ( "" , repo_setting . Runners )
m . Combo ( "/{runnerid}" ) . Get ( repo_setting . RunnersEdit ) .
Post ( web . Bind ( forms . EditRunnerForm { } ) , repo_setting . RunnersEditPost )
m . Post ( "/{runnerid}/delete" , repo_setting . RunnerDeletePost )
m . Get ( "/reset_registration_token" , repo_setting . ResetRunnerRegistrationToken )
} )
}
2021-01-30 09:55:53 +01:00
// FIXME: not all routes need go through same middleware.
2017-04-25 09:24:51 +02:00
// Especially some AJAX requests, we can reduce middleware number to improve performance.
2023-07-21 14:14:20 +02:00
2021-06-09 01:33:54 +02:00
m . Get ( "/" , Home )
2022-10-28 17:17:38 +02:00
m . Get ( "/sitemap.xml" , sitemapEnabled , ignExploreSignIn , HomeSitemap )
2021-11-26 15:55:11 +01:00
m . Group ( "/.well-known" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Get ( "/openid-configuration" , auth . OIDCWellKnown )
2022-05-09 20:20:21 +02:00
m . Group ( "" , func ( ) {
2021-11-26 15:55:11 +01:00
m . Get ( "/nodeinfo" , NodeInfoLinks )
2022-05-09 20:20:21 +02:00
m . Get ( "/webfinger" , WebfingerQuery )
} , federationEnabled )
2023-04-27 08:06:45 +02:00
m . Get ( "/change-password" , func ( ctx * context . Context ) {
ctx . Redirect ( setting . AppSubURL + "/user/settings/account" )
2021-11-26 15:55:11 +01:00
} )
2023-12-25 13:13:18 +01:00
m . Methods ( "GET, HEAD" , "/*" , public . FileHandlerFunc ( ) )
} , optionsCorsHandler ( ) )
2021-11-26 15:55:11 +01:00
2017-04-25 09:24:51 +02:00
m . Group ( "/explore" , func ( ) {
m . Get ( "" , func ( ctx * context . Context ) {
ctx . Redirect ( setting . AppSubURL + "/explore/repos" )
} )
2021-06-09 01:33:54 +02:00
m . Get ( "/repos" , explore . Repos )
2022-10-28 17:17:38 +02:00
m . Get ( "/repos/sitemap-{idx}.xml" , sitemapEnabled , explore . Repos )
2021-06-09 01:33:54 +02:00
m . Get ( "/users" , explore . Users )
2022-10-28 17:17:38 +02:00
m . Get ( "/users/sitemap-{idx}.xml" , sitemapEnabled , explore . Users )
2021-06-09 01:33:54 +02:00
m . Get ( "/organizations" , explore . Organizations )
2023-06-09 21:02:33 +02:00
m . Get ( "/code" , func ( ctx * context . Context ) {
if unit . TypeCode . UnitGlobalDisabled ( ) {
ctx . NotFound ( unit . TypeCode . String ( ) , nil )
return
}
} , explore . Code )
2022-04-07 20:59:56 +02:00
m . Get ( "/topics/search" , explore . TopicSearch )
2021-03-11 14:40:54 +01:00
} , ignExploreSignIn )
2022-04-07 20:59:56 +02:00
m . Group ( "/issues" , func ( ) {
m . Get ( "" , user . Issues )
m . Get ( "/search" , repo . SearchIssues )
} , reqSignIn )
2021-01-13 05:19:17 +01:00
m . Get ( "/pulls" , reqSignIn , user . Pulls )
2019-12-15 15:20:08 +01:00
m . Get ( "/milestones" , reqSignIn , reqMilestonesDashboardPageEnabled , user . Milestones )
2017-04-25 09:24:51 +02:00
// ***** START: User *****
2023-07-27 07:08:51 +02:00
// "user/login" doesn't need signOut, then logged-in users can still access this route for redirection purposes by "/user/login?redirec_to=..."
m . Get ( "/user/login" , auth . SignIn )
2017-04-25 09:24:51 +02:00
m . Group ( "/user" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Post ( "/login" , web . Bind ( forms . SignInForm { } ) , auth . SignInPost )
2017-08-19 17:34:49 +02:00
m . Group ( "" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Combo ( "/login/openid" ) .
2022-01-02 14:12:35 +01:00
Get ( auth . SignInOpenID ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . SignInOpenIDForm { } ) , auth . SignInOpenIDPost )
2017-08-19 17:34:49 +02:00
} , openIDSignInEnabled )
m . Group ( "/openid" , func ( ) {
m . Combo ( "/connect" ) .
2022-01-02 14:12:35 +01:00
Get ( auth . ConnectOpenID ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . ConnectOpenIDForm { } ) , auth . ConnectOpenIDPost )
2017-08-19 17:34:49 +02:00
m . Group ( "/register" , func ( ) {
m . Combo ( "" ) .
2022-01-02 14:12:35 +01:00
Get ( auth . RegisterOpenID , openIDSignUpEnabled ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . SignUpOpenIDForm { } ) , auth . RegisterOpenIDPost )
2017-08-19 17:34:49 +02:00
} , openIDSignUpEnabled )
} , openIDSignInEnabled )
2022-01-02 14:12:35 +01:00
m . Get ( "/sign_up" , auth . SignUp )
2022-12-12 09:09:26 +01:00
m . Post ( "/sign_up" , web . Bind ( forms . RegisterForm { } ) , auth . SignUpPost )
2022-02-09 21:33:36 +01:00
m . Get ( "/link_account" , linkAccountEnabled , auth . LinkAccount )
2022-12-12 09:09:26 +01:00
m . Post ( "/link_account_signin" , linkAccountEnabled , web . Bind ( forms . SignInForm { } ) , auth . LinkAccountPostSignIn )
m . Post ( "/link_account_signup" , linkAccountEnabled , web . Bind ( forms . RegisterForm { } ) , auth . LinkAccountPostRegister )
2017-04-25 09:24:51 +02:00
m . Group ( "/two_factor" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Get ( "" , auth . TwoFactor )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . TwoFactorAuthForm { } ) , auth . TwoFactorPost )
2022-01-02 14:12:35 +01:00
m . Get ( "/scratch" , auth . TwoFactorScratch )
2022-12-12 09:09:26 +01:00
m . Post ( "/scratch" , web . Bind ( forms . TwoFactorScratchAuthForm { } ) , auth . TwoFactorScratchPost )
2017-04-25 09:24:51 +02:00
} )
2022-01-14 16:03:31 +01:00
m . Group ( "/webauthn" , func ( ) {
m . Get ( "" , auth . WebAuthn )
m . Get ( "/assertion" , auth . WebAuthnLoginAssertion )
m . Post ( "/assertion" , auth . WebAuthnLoginAssertionPost )
2018-05-19 16:12:37 +02:00
} )
2017-04-25 09:24:51 +02:00
} , reqSignOut )
2022-01-20 12:41:25 +01:00
m . Any ( "/user/events" , routing . MarkLongPolling , events . Events )
2020-05-07 23:49:00 +02:00
2019-03-08 17:42:50 +01:00
m . Group ( "/login/oauth" , func ( ) {
2024-11-12 22:33:35 +01:00
m . Group ( "" , func ( ) {
m . Get ( "/authorize" , web . Bind ( forms . AuthorizationForm { } ) , auth . AuthorizeOAuth )
m . Post ( "/grant" , web . Bind ( forms . GrantApplicationForm { } ) , auth . GrantApplicationOAuth )
// TODO manage redirection
m . Post ( "/authorize" , web . Bind ( forms . AuthorizationForm { } ) , auth . AuthorizeOAuth )
} , ignSignInAndCsrf , reqSignIn )
2024-11-20 15:22:48 +01:00
m . Methods ( "GET, POST, OPTIONS" , "/userinfo" , optionsCorsHandler ( ) , ignSignInAndCsrf , auth . InfoOAuth )
2024-11-12 22:33:35 +01:00
m . Methods ( "POST, OPTIONS" , "/access_token" , optionsCorsHandler ( ) , web . Bind ( forms . AccessTokenForm { } ) , ignSignInAndCsrf , auth . AccessTokenOAuth )
m . Methods ( "GET, OPTIONS" , "/keys" , optionsCorsHandler ( ) , ignSignInAndCsrf , auth . OIDCKeys )
m . Methods ( "POST, OPTIONS" , "/introspect" , optionsCorsHandler ( ) , web . Bind ( forms . IntrospectTokenForm { } ) , ignSignInAndCsrf , auth . IntrospectOAuth )
} , oauth2Enabled )
2019-03-08 17:42:50 +01:00
2017-04-25 09:24:51 +02:00
m . Group ( "/user/settings" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Get ( "" , user_setting . Profile )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . UpdateProfileForm { } ) , user_setting . ProfilePost )
2022-01-02 14:12:35 +01:00
m . Get ( "/change_password" , auth . MustChangePassword )
2022-12-12 09:09:26 +01:00
m . Post ( "/change_password" , web . Bind ( forms . MustChangePasswordForm { } ) , auth . MustChangePasswordPost )
m . Post ( "/avatar" , web . Bind ( forms . AvatarForm { } ) , user_setting . AvatarPost )
2022-01-02 14:12:35 +01:00
m . Post ( "/avatar/delete" , user_setting . DeleteAvatar )
2018-05-15 12:07:32 +02:00
m . Group ( "/account" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Combo ( "" ) . Get ( user_setting . Account ) . Post ( web . Bind ( forms . ChangePasswordForm { } ) , user_setting . AccountPost )
m . Post ( "/email" , web . Bind ( forms . AddEmailForm { } ) , user_setting . EmailPost )
2022-01-02 14:12:35 +01:00
m . Post ( "/email/delete" , user_setting . DeleteEmail )
m . Post ( "/delete" , user_setting . DeleteAccount )
2021-10-27 17:40:08 +02:00
} )
m . Group ( "/appearance" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Get ( "" , user_setting . Appearance )
2022-12-12 09:09:26 +01:00
m . Post ( "/language" , web . Bind ( forms . UpdateLanguageForm { } ) , user_setting . UpdateUserLang )
2024-03-01 13:22:40 +01:00
m . Post ( "/hints" , web . Bind ( forms . UpdateHintsForm { } ) , user_setting . UpdateUserHints )
2022-01-21 18:59:26 +01:00
m . Post ( "/hidden_comments" , user_setting . UpdateUserHiddenComments )
2022-12-12 09:09:26 +01:00
m . Post ( "/theme" , web . Bind ( forms . UpdateThemeForm { } ) , user_setting . UpdateUIThemePost )
2018-05-15 12:07:32 +02:00
} )
m . Group ( "/security" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Get ( "" , security . Security )
2018-05-15 12:07:32 +02:00
m . Group ( "/two_factor" , func ( ) {
2022-01-02 14:12:35 +01:00
m . Post ( "/regenerate_scratch" , security . RegenerateScratchTwoFactor )
m . Post ( "/disable" , security . DisableTwoFactor )
m . Get ( "/enroll" , security . EnrollTwoFactor )
2022-12-12 09:09:26 +01:00
m . Post ( "/enroll" , web . Bind ( forms . TwoFactorAuthForm { } ) , security . EnrollTwoFactorPost )
2018-05-15 12:07:32 +02:00
} )
2022-01-14 16:03:31 +01:00
m . Group ( "/webauthn" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Post ( "/request_register" , web . Bind ( forms . WebauthnRegistrationForm { } ) , security . WebAuthnRegister )
2022-01-14 16:03:31 +01:00
m . Post ( "/register" , security . WebauthnRegisterPost )
2022-12-12 09:09:26 +01:00
m . Post ( "/delete" , web . Bind ( forms . WebauthnDeleteForm { } ) , security . WebauthnDelete )
2018-05-19 16:12:37 +02:00
} )
2018-05-15 12:07:32 +02:00
m . Group ( "/openid" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . AddOpenIDForm { } ) , security . OpenIDPost )
2022-01-02 14:12:35 +01:00
m . Post ( "/delete" , security . DeleteOpenID )
m . Post ( "/toggle_visibility" , security . ToggleOpenIDVisibility )
2018-05-15 12:07:32 +02:00
} , openIDSignInEnabled )
2022-02-09 21:33:36 +01:00
m . Post ( "/account_link" , linkAccountEnabled , security . DeleteAccountLink )
2018-05-15 12:07:32 +02:00
} )
2024-11-12 22:33:35 +01:00
m . Group ( "/applications" , func ( ) {
// oauth2 applications
m . Group ( "/oauth2" , func ( ) {
m . Get ( "/{id}" , user_setting . OAuth2ApplicationShow )
m . Post ( "/{id}" , web . Bind ( forms . EditOAuth2ApplicationForm { } ) , user_setting . OAuthApplicationsEdit )
m . Post ( "/{id}/regenerate_secret" , user_setting . OAuthApplicationsRegenerateSecret )
m . Post ( "" , web . Bind ( forms . EditOAuth2ApplicationForm { } ) , user_setting . OAuthApplicationsPost )
m . Post ( "/{id}/delete" , user_setting . DeleteOAuth2Application )
m . Post ( "/{id}/revoke/{grantId}" , user_setting . RevokeOAuth2Grant )
} , oauth2Enabled )
// access token applications
m . Combo ( "" ) . Get ( user_setting . Applications ) .
Post ( web . Bind ( forms . NewAccessTokenForm { } ) , user_setting . ApplicationsPost )
m . Post ( "/delete" , user_setting . DeleteApplication )
2019-03-08 17:42:50 +01:00
} )
2024-11-12 22:33:35 +01:00
2022-01-02 14:12:35 +01:00
m . Combo ( "/keys" ) . Get ( user_setting . Keys ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . AddKeyForm { } ) , user_setting . KeysPost )
2022-01-02 14:12:35 +01:00
m . Post ( "/keys/delete" , user_setting . DeleteKey )
2022-11-20 15:08:38 +01:00
m . Group ( "/packages" , func ( ) {
m . Get ( "" , user_setting . Packages )
m . Group ( "/rules" , func ( ) {
m . Group ( "/add" , func ( ) {
m . Get ( "" , user_setting . PackagesRuleAdd )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . PackageCleanupRuleForm { } ) , user_setting . PackagesRuleAddPost )
2022-11-20 15:08:38 +01:00
} )
m . Group ( "/{id}" , func ( ) {
m . Get ( "" , user_setting . PackagesRuleEdit )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . PackageCleanupRuleForm { } ) , user_setting . PackagesRuleEditPost )
2022-11-20 15:08:38 +01:00
m . Get ( "/preview" , user_setting . PackagesRulePreview )
} )
} )
2023-02-05 11:12:31 +01:00
m . Group ( "/cargo" , func ( ) {
m . Post ( "/initialize" , user_setting . InitializeCargoIndex )
m . Post ( "/rebuild" , user_setting . RebuildCargoIndex )
} )
2023-02-06 02:49:21 +01:00
m . Post ( "/chef/regenerate_keypair" , user_setting . RegenerateChefKeyPair )
2022-11-20 15:08:38 +01:00
} , packagesEnabled )
2023-04-28 02:08:47 +02:00
m . Group ( "/actions" , func ( ) {
m . Get ( "" , user_setting . RedirectToDefaultSetting )
2023-05-31 03:39:54 +02:00
addSettingsRunnersRoutes ( )
2023-04-28 02:08:47 +02:00
addSettingsSecretsRoutes ( )
2023-12-25 08:28:59 +01:00
addSettingsVariablesRoutes ( )
2023-04-28 02:08:47 +02:00
} , actions . MustEnableActions )
2022-01-02 14:12:35 +01:00
m . Get ( "/organization" , user_setting . Organization )
m . Get ( "/repos" , user_setting . Repos )
m . Post ( "/repos/unadopted" , user_setting . AdoptOrDeleteRepository )
2023-03-10 15:28:32 +01:00
m . Group ( "/hooks" , func ( ) {
m . Get ( "" , user_setting . Webhooks )
m . Post ( "/delete" , user_setting . DeleteWebhook )
2024-03-21 14:43:43 +01:00
m . Get ( "/{type}/new" , repo_setting . WebhookNew )
2024-03-21 14:15:56 +01:00
m . Post ( "/{type}/new" , repo_setting . WebhookCreate )
2023-03-10 15:28:32 +01:00
m . Group ( "/{id}" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "" , repo_setting . WebhookEdit )
2024-03-21 14:33:59 +01:00
m . Post ( "" , repo_setting . WebhookUpdate )
2024-03-21 14:43:43 +01:00
m . Post ( "/replay/{uuid}" , repo_setting . WebhookReplay )
2023-03-10 15:28:32 +01:00
} )
2023-04-28 02:08:47 +02:00
} , webhooksEnabled )
[MODERATION] User blocking
- Add the ability to block a user via their profile page.
- This will unstar their repositories and visa versa.
- Blocked users cannot create issues or pull requests on your the doer's repositories (mind that this is not the case for organizations).
- Blocked users cannot comment on the doer's opened issues or pull requests.
- Blocked users cannot add reactions to doer's comments.
- Blocked users cannot cause a notification trough mentioning the doer.
Reviewed-on: https://codeberg.org/forgejo/forgejo/pulls/540
(cherry picked from commit 687d852480388897db4d7b0cb397cf7135ab97b1)
(cherry picked from commit 0c32a4fde531018f74e01d9db6520895fcfa10cc)
(cherry picked from commit 1791130e3cb8470b9b39742e0004d5e4c7d1e64d)
(cherry picked from commit 37858b7e8fb6ba6c6ea0ac2562285b3b144efa19)
(cherry picked from commit a3e2bfd7e9eab82cc2c17061f6bb4e386a108c46)
(cherry picked from commit 7009b9fe87696b6182fab65ae82bf5a25cd39971)
Conflicts: https://codeberg.org/forgejo/forgejo/pulls/1014
routers/web/user/profile.go
templates/user/profile.tmpl
(cherry picked from commit b2aec3479177e725cfc7cbbb9d94753226928d1c)
(cherry picked from commit e2f1b73752f6bd3f830297d8f4ac438837471226)
[MODERATION] organization blocking a user (#802)
- Resolves #476
- Follow up for: #540
- Ensure that the doer and blocked person cannot follow each other.
- Ensure that the block person cannot watch doer's repositories.
- Add unblock button to the blocked user list.
- Add blocked since information to the blocked user list.
- Add extra testing to moderation code.
- Blocked user will unwatch doer's owned repository upon blocking.
- Add flash messages to let the user know the block/unblock action was successful.
- Add "You haven't blocked any users" message.
- Add organization blocking a user.
Co-authored-by: Gusted <postmaster@gusted.xyz>
Reviewed-on: https://codeberg.org/forgejo/forgejo/pulls/802
(cherry picked from commit 0505a1042197bd9136b58bc70ec7400a23471585)
(cherry picked from commit 37b4e6ef9b85e97d651cf350c9f3ea272ee8d76a)
(cherry picked from commit c17c121f2cf1f00e2a8d6fd6847705df47d0771e)
[MODERATION] organization blocking a user (#802) (squash)
Changes to adapt to:
6bbccdd177 Improve AJAX link and modal confirm dialog (#25210)
Refs: https://codeberg.org/forgejo/forgejo/pulls/882/files#issuecomment-945962
Refs: https://codeberg.org/forgejo/forgejo/pulls/882#issue-330561
(cherry picked from commit 523635f83cb2a1a4386769b79326088c5c4bbec7)
(cherry picked from commit 4743eaa6a0be0ef47de5b17c211dfe8bad1b7af9)
(cherry picked from commit eff5b43d2e843d5d537756d4fa58a8a010b6b527)
Conflicts: https://codeberg.org/forgejo/forgejo/pulls/1014
routers/web/user/profile.go
(cherry picked from commit 9d359be5ed11237088ccf6328571939af814984e)
(cherry picked from commit b1f3069a22a03734cffbfcd503ce004ba47561b7)
[MODERATION] add user blocking API
- Follow up for: #540, #802
- Add API routes for user blocking from user and organization
perspective.
- The new routes have integration testing.
- The new model functions have unit tests.
- Actually quite boring to write and to read this pull request.
(cherry picked from commit f3afaf15c7e34038363c9ce8e1ef957ec1e22b06)
(cherry picked from commit 6d754db3e5faff93a58fab2867737f81f40f6599)
(cherry picked from commit 2a89ddc0acffa9aea0f02b721934ef9e2b496a88)
(cherry picked from commit 4a147bff7e963ab9dffcfaefa5c2c01c59b4c732)
Conflicts:
routers/api/v1/api.go
templates/swagger/v1_json.tmpl
(cherry picked from commit bb8c33918569f65f25b014f0d7fe6ac20f9036fc)
(cherry picked from commit 5a11569a011b7d0a14391e2b5c07d0af825d7b0e)
(cherry picked from commit 2373c801ee6b84c368b498b16e6ad18650b38f42)
[MODERATION] restore redirect on unblock
ctx.RedirectToFirst(ctx.FormString("redirect_to"), ctx.ContextUser.HomeLink())
was replaced by
ctx.JSONOK()
in 128d77a3a Following up fixes for "Fix inconsistent user profile layout across tabs" (#25739)
thus changing the behavior (nicely spotted by the tests). This
restores it.
(cherry picked from commit 597c243707c3c86e7256faf1e6ba727224554de3)
(cherry picked from commit cfa539e590127b4b953b010fba3dea21c82a1714)
[MODERATION] Add test case (squash)
- Add an test case, to test an property of the function.
(cherry picked from commit 70dadb1916bfef8ba8cbc4e9b042cc8740f45e28)
[MODERATION] Block adding collaborators
- Ensure that the doer and blocked user cannot add each other as
collaborators to repositories.
- The Web UI gets an detailed message of the specific situation, the API
gets an generic Forbidden code.
- Unit tests has been added.
- Integration testing for Web and API has been added.
- This commit doesn't introduce removing each other as collaborators on
the block action, due to the complexity of database calls that needs to
be figured out. That deserves its own commit and test code.
(cherry picked from commit 747be949a1b3cd06f6586512f1af4630e55d7ad4)
[MODERATION] move locale_en-US.ini strings to avoid conflicts
Conflicts:
web_src/css/org.css
web_src/css/user.css
https://codeberg.org/forgejo/forgejo/pulls/1180
(cherry picked from commit e53f955c888ebaafc863a6e463da87f70f5605da)
Conflicts:
services/issue/comments.go
https://codeberg.org/forgejo/forgejo/pulls/1212
(cherry picked from commit b4a454b576eee0c7738b2f7df1acaf5bf7810d12)
Conflicts:
models/forgejo_migrations/migrate.go
options/locale/locale_en-US.ini
services/pull/pull.go
https://codeberg.org/forgejo/forgejo/pulls/1264
[MODERATION] Remove blocked user collaborations with doer
- When the doer blocks an user, who is also an collaborator on an
repository that the doer owns, remove that collaboration.
- Added unit tests.
- Refactor the unit test to be more organized.
(cherry picked from commit ec8701617830152680d69d50d64cb43cc2054a89)
(cherry picked from commit 313e6174d832501c57724ae7a6285194b7b81aab)
[MODERATION] QoL improvements (squash)
- Ensure that organisations cannot be blocked. It currently has no
effect, as all blocked operations cannot be executed from an
organisation standpoint.
- Refactored the API route to make use of the `UserAssignmentAPI`
middleware.
- Make more use of `t.Run` so that the test code is more clear about
which block of code belongs to which test case.
- Added more integration testing (to ensure the organisations cannot be
blocked and some authorization/permission checks).
(cherry picked from commit e9d638d0756ee20b6bf1eb999c988533a5066a68)
[MODERATION] s/{{avatar/{{ctx.AvatarUtils.Avatar/
(cherry picked from commit ce8b30be1327ab98df2ba061dd7e2a278b278c5b)
(cherry picked from commit f911dc402508b04cd5d5fb2f3332c2d640e4556e)
Conflicts:
options/locale/locale_en-US.ini
https://codeberg.org/forgejo/forgejo/pulls/1354
(cherry picked from commit c1b37b7fdaf06ee60da341dff76d703990c08082)
(cherry picked from commit 856a2e09036adf56d987c6eee364c431bc37fb2e)
[MODERATION] Show graceful error on comment creation
- When someone is blocked by the repository owner or issue poster and
try to comment on that issue, they get shown a graceful error.
- Adds integration test.
(cherry picked from commit 490646302e1e3dc3c59c9d75938b4647b6873ce7)
(cherry picked from commit d3d88667cbb928a6ff80658eba8ef0c6c508c9e0)
(cherry picked from commit 6818de13a921753e082b7c3d64c23917cc884e4b)
[MODERATION] Show graceful error on comment creation (squash) typo
(cherry picked from commit 1588d4834a37a744f092f2aeea6c9ef4795d7356)
(cherry picked from commit d510ea52d091503e841d66f2f604348add8b4535)
(cherry picked from commit 8249e93a14f628bb0e89fe3be678e4966539944e)
[MODERATION] Refactor integration testing (squash)
- Motivation for this PR is that I'd noticed that a lot of repeated
calls are happening between the test functions and that certain tests
weren't using helper functions like `GetCSRF`, therefor this refactor of
the integration tests to keep it: clean, small and hopefully more
maintainable and understandable.
- There are now three integration tests: `TestBlockUser`,
`TestBlockUserFromOrganization` and `TestBlockActions` (and has been
moved in that order in the source code).
- `TestBlockUser` is for doing blocking related actions as an user and
`TestBlockUserFromOrganization` as an organisation, even though they
execute the same kind of tests they do not share any database calls or
logic and therefor it currently doesn't make sense to merge them
together (hopefully such oppurtinutiy might be presented in the future).
- `TestBlockActions` now contain all tests for actions that should be
blocked after blocking has happened, most tests now share the same doer
and blocked users and a extra fixture has been added to make this
possible for the comment test.
- Less code, more comments and more re-use between tests.
(cherry picked from commit ffb393213d2f1269aad3c019d039cf60d0fe4b10)
(cherry picked from commit 85505e0f815fede589c272d301c95204f9596985)
(cherry picked from commit 0f3cf17761f6caedb17550f69de96990c2090af1)
[MODERATION] Fix network error (squash)
- Fix network error toast messages on user actions such as follow and
unfollow. This happened because the javascript code now expects an JSON
to be returned, but this wasn't the case due to
cfa539e590127b4953b010fba3dea21c82a1714.
- The integration testing has been adjusted to instead test for the
returned flash cookie.
(cherry picked from commit 112bc25e548d317a4ee00f9efa9068794a733e3b)
(cherry picked from commit 1194fe4899eb39dcb9a2410032ad0cc67a62b92b)
(cherry picked from commit 9abb95a8441e227874fe156095349a3173cc5a81)
[MODERATION] Modernize frontend (squash)
- Unify blocked users list.
- Use the new flex list classes for blocked users list to avoid using
the CSS helper classes and thereby be consistent in the design.
- Fix the modal by using the new modal class.
- Remove the icon in the modal as looks too big in the new design.
- Fix avatar not displaying as it was passing the context where the user
should've been passed.
- Don't use italics for 'Blocked since' text.
- Use namelink template to display the user's name and homelink.
(cherry picked from commit ec935a16a319b14e819ead828d1d9875280d9259)
(cherry picked from commit 67f37c83461aa393c53a799918e9708cb9b89b30)
Conflicts:
models/user/follow.go
models/user/user_test.go
routers/api/v1/user/follower.go
routers/web/shared/user/header.go
routers/web/user/profile.go
templates/swagger/v1_json.tmpl
https://codeberg.org/forgejo/forgejo/pulls/1468
(cherry picked from commit 6a9626839c6342cd2767ea12757ee2f78eaf443b)
Conflicts:
tests/integration/api_nodeinfo_test.go
https://codeberg.org/forgejo/forgejo/pulls/1508#issuecomment-1242385
(cherry picked from commit 7378b251b481ed1e60e816caf8f649e8397ee5fc)
Conflicts:
models/fixtures/watch.yml
models/issues/reaction.go
models/issues/reaction_test.go
routers/api/v1/repo/issue_reaction.go
routers/web/repo/issue.go
services/issue/issue.go
https://codeberg.org/forgejo/forgejo/pulls/1547
(cherry picked from commit c2028930c101223820de0bbafc318e9394c347b8)
(cherry picked from commit d3f9134aeeef784586e8412e8dbba0a8fceb0cd4)
(cherry picked from commit 7afe154c5c40bcc65accdf51c9224b2f7627a684)
(cherry picked from commit 99ac7353eb1e834a77fe42aa89208791cc2364ff)
(cherry picked from commit a9cde00c5c25ea8c427967cb7ab57abb618e44cb)
Conflicts:
services/user/delete.go
https://codeberg.org/forgejo/forgejo/pulls/1736
(cherry picked from commit 008c0cc63d1a3b8eb694bffbf77a7b25c56afd57)
[DEADCODE] add exceptions
(cherry picked from commit 12ddd2b10e3309f6430b0af42855c6af832832ee)
[MODERATION] Remove deadcode (squash)
- Remove deadcode that's no longer used by Forgejo.
(cherry picked from commit 0faeab4fa9b0aa59f86760b24ecbc07815026c82)
[MODERATION] Add repo transfers to blocked functionality (squash)
- When someone gets blocked, remove all pending repository transfers
from the blocked user to the doer.
- Do not allow to start transferring repositories to the doer as blocked user.
- Added unit testing.
- Added integration testing.
(cherry picked from commit 8a3caac33013482ddbee2fa51510c6918ba54466)
(cherry picked from commit a92b4cfeb63b90eb2d90d0feb51cec62e0502d84)
(cherry picked from commit acaaaf07d999974dbe5f9c5e792621c597bfb542)
(cherry picked from commit 735818863c1793aa6f6983afedc4bd3b36026ca5)
(cherry picked from commit f50fa43b32160d0d88eca1dbdca09b5f575fb62b)
(cherry picked from commit e16683643388fb3c60ea478f1419a6af4f4aa283)
(cherry picked from commit 82a0e4a3814a66ce44be6a031bdf08484586c61b)
(cherry picked from commit ff233c19c4a5edcc2b99a6f41a2d19dbe8c08b3b)
(cherry picked from commit 8ad87d215f2b6adb978de77e53ba2bf7ea571430)
[MODERATION] Fix unblock action (squash)
- Pass the whole context instead of only giving pieces.
- This fixes CSRF not correctly being inserted into the unblock buttons.
(cherry picked from commit 2aa51922ba6a0ea2f8644277baa74fc8f34ab95a)
(cherry picked from commit 7ee8db0f018340bc97f125415503e3e5db5f5082)
(cherry picked from commit e4f8b999bcd3b68b3ef7f54f5b17c3ada0308121)
(cherry picked from commit 05aea60b1302bbd3ea574a9c6c34e1005a5d73bf)
(cherry picked from commit dc0d61b012cfaf2385f71e97cda5f220b58b9fa4)
(cherry picked from commit f53fa583de671ff60a0a1d0f3ab8c260e1ba4e1f)
(cherry picked from commit c65b89a58d11b32009c710c2f5e75f0cd3539395)
(cherry picked from commit 69e50b9969db3ab71cefaed520757876a9629a5c)
(cherry picked from commit ec127440b86cb5fcf51799d8bd76a9fd6b9cebcc)
[MODERATION] cope with shared fixtures
* There is one more issue in the fixtures and this breaks some tests
* The users in the shared fixtures were renamed for clarity and that
breaks some tests
(cherry picked from commit 707a4edbdf67d0eb168d7bb430cf85dd8cd63c52)
Conflicts:
modules/indexer/issues/indexer_test.go
https://codeberg.org/forgejo/forgejo/pulls/1508
(cherry picked from commit 82cc044366c749df80ffad44eed2988b8e64211e)
(cherry picked from commit 2776aec7e85850f1d7f01a090a72491550fb9d29)
(cherry picked from commit 1fbde36dc784b5b2cc6193f02ff0d436b0f2a629)
(cherry picked from commit 1293db3c4e5df218501f5add9f9d41101ffcb8aa)
(cherry picked from commit 6476802175bac3ef78dd8f24ff6bebc16f398a78)
(cherry picked from commit 5740f2fc830356acb7929a02fe304008b94a0ca5)
(cherry picked from commit afc12d7b6e9b773fa89718aa79cd95c0e0ce4406)
[MODERATION] Fix transfer confirmation (squash)
- Fix problem caused by the clearer confirmation for dangerous actions commit.
(cherry picked from commit 3488f4a9cb1f7f73103ae0017d644f13ca3ab798)
(cherry picked from commit ed7de91f6ace23a1459bc6552edf719d62c7c941)
(cherry picked from commit 2d97929b9b7b8d979eb12bf0994d3f169d41f7fd)
(cherry picked from commit 50d035a7b058b9c4486c38cd4be0b02a4e1bf4d9)
(cherry picked from commit 0a0c07d78a1dee3489b97ab359bb957e3f7fb94b)
(cherry picked from commit 85e55c4dbc2f513f3d5254dac20915e8c3c22886)
(cherry picked from commit d8282122ad6e8b497de35d1ed89e3093a2cd5ee2)
(cherry picked from commit 3f0b3b6cc582c3d672d371dd9fe1203a56cb88c0)
[MODERATION] Purge issues on user deletion (squash)
(cherry picked from commit 4f529d9596ffbfc4e754c28830ba028f6344dc5b)
(cherry picked from commit f0e3acadd321fcb99e8ea3e3ce1c69df25c4ca4d)
(cherry picked from commit 682c4effe69dc0d4ed304fa7ce6259d9ce573629)
(cherry picked from commit e43c2d84fd4b6fd31e2370cec1034262d12e5c34)
(cherry picked from commit 9c8e53ccc78053026e4f667889959c23c8d95934)
(cherry picked from commit a9eb7ac783b2c16ee3702a88203bf857cb4147fc)
[MODERATION] Purge issues on user deletion (squash) revert shared fixtures workarounds
(cherry picked from commit 7224653a40e32186892e89bfedd49edecf5b8f81)
(cherry picked from commit aa6e8672f9473a9100e7575051dec9eda37709a0)
(cherry picked from commit 58c7947e95648f50237ddcd46b6bd025b224a70f)
(cherry picked from commit f1aacb1851b232082febcd7870a40a56de3855a6)
(cherry picked from commit 0bf174af87f7de9a8d869304f709e2bf41f3dde9)
(cherry picked from commit f9706f4335df3b7688ed60853d917efa72fb464a)
[MODERATION] Prepare moderation for context locale changes (squash)
- Resolves https://codeberg.org/forgejo/forgejo/issues/1711
(cherry picked from commit 2e289baea943dcece88f02d110b03d344308a261)
(cherry picked from commit 97b16bc19ae680db62608d6020b00fe5ac451c60)
[MODERATION] User blocking (squash) do not use shared fixture
It conflicts with a fixtured added in the commit
Fix comment permissions (#28213) (#28216)
(cherry picked from commit ab40799dcab24e9f495d765268b791931da81684)
(cherry picked from commit 996c92cafdb5b33a6d2d05d94038e950d97eb7de)
(cherry picked from commit 259912e3a69071c5ad57871464d0b79f69a8e72c)
Conflicts:
options/locale/locale_en-US.ini
https://codeberg.org/forgejo/forgejo/pulls/1921
(cherry picked from commit 1e82abc032c18015b92c93a7617a5dd06d50bd2d)
(cherry picked from commit a176fee1607d571b25b345184f1c50d403029610)
(cherry picked from commit 0480b76dfeda968849e900da9454a3efd82590fa)
(cherry picked from commit 4bc06b7b3841c74e3d790b1ef635c2b382ca7123)
(cherry picked from commit 073094cf722a927a623408d66537c758d7d64e4c)
(cherry picked from commit ac6201c647a4d3a2cfb2b0303b851a8fe7a29444)
(cherry picked from commit 7e0812674da3fbd1e96bdda820962edad6826fbd)
(cherry picked from commit 068c741e5696957710b3d1c2e18c00be2ffaa278)
Conflicts:
models/repo_transfer.go
models/repo_transfer_test.go
routers/web/user/profile.go
https://codeberg.org/forgejo/forgejo/pulls/2298
2023-08-15 01:07:38 +02:00
m . Group ( "/blocked_users" , func ( ) {
m . Get ( "" , user_setting . BlockedUsers )
m . Post ( "/unblock" , user_setting . UnblockUser )
} )
2023-04-28 02:08:47 +02:00
} , reqSignIn , ctxDataSet ( "PageIsUserSettings" , true , "AllThemes" , setting . UI . Themes , "EnablePackages" , setting . Packages . Enabled ) )
2017-04-25 09:24:51 +02:00
m . Group ( "/user" , func ( ) {
2022-04-12 04:02:58 +02:00
m . Get ( "/activate" , auth . Activate )
m . Post ( "/activate" , auth . ActivatePost )
2022-01-02 14:12:35 +01:00
m . Any ( "/activate_email" , auth . ActivateEmail )
Avatar refactor, move avatar code from `models` to `models.avatars`, remove duplicated code (#17123)
Why this refactor
The goal is to move most files from `models` package to `models.xxx` package. Many models depend on avatar model, so just move this first.
And the existing logic is not clear, there are too many function like `AvatarLink`, `RelAvatarLink`, `SizedRelAvatarLink`, `SizedAvatarLink`, `MakeFinalAvatarURL`, `HashedAvatarLink`, etc. This refactor make everything clear:
* user.AvatarLink()
* user.AvatarLinkWithSize(size)
* avatars.GenerateEmailAvatarFastLink(email, size)
* avatars.GenerateEmailAvatarFinalLink(email, size)
And many duplicated code are deleted in route handler, the handler and the model share the same avatar logic now.
2021-10-06 01:25:46 +02:00
m . Get ( "/avatar/{username}/{size}" , user . AvatarByUserName )
2022-01-02 14:12:35 +01:00
m . Get ( "/recover_account" , auth . ResetPasswd )
m . Post ( "/recover_account" , auth . ResetPasswdPost )
m . Get ( "/forgot_password" , auth . ForgotPasswd )
m . Post ( "/forgot_password" , auth . ForgotPasswdPost )
m . Post ( "/logout" , auth . SignOut )
2022-04-12 04:02:58 +02:00
m . Get ( "/task/{task}" , reqSignIn , user . TaskStatus )
m . Get ( "/stopwatches" , reqSignIn , user . GetStopwatches )
2024-10-22 07:09:19 +02:00
m . Get ( "/search_candidates" , ignExploreSignIn , user . SearchCandidates )
2022-05-29 02:03:17 +02:00
m . Group ( "/oauth2" , func ( ) {
m . Get ( "/{provider}" , auth . SignInOAuth )
m . Get ( "/{provider}/callback" , auth . SignInOAuthCallback )
} )
2017-04-25 09:24:51 +02:00
} )
// ***** END: User *****
2021-01-26 16:36:53 +01:00
m . Get ( "/avatar/{hash}" , user . AvatarByEmailHash )
2020-03-27 13:34:39 +01:00
2023-09-12 08:15:16 +02:00
adminReq := verifyAuthWithOptions ( & common . VerifyOptions { SignInRequired : true , AdminRequired : true } )
2017-04-25 09:24:51 +02:00
// ***** START: Admin *****
m . Group ( "/admin" , func ( ) {
2023-06-03 16:03:41 +02:00
m . Get ( "" , admin . Dashboard )
2024-02-16 03:52:25 +01:00
m . Get ( "/system_status" , admin . SystemStatus )
2023-06-03 16:03:41 +02:00
m . Post ( "" , web . Bind ( forms . AdminDashboardForm { } ) , admin . DashboardPost )
2022-10-17 01:29:26 +02:00
2024-04-04 18:02:24 +02:00
if setting . Database . Type . IsMySQL ( ) {
2024-02-04 09:43:59 +01:00
m . Get ( "/self_check" , admin . SelfCheck )
}
2024-01-10 12:03:23 +01:00
2022-10-17 01:29:26 +02:00
m . Group ( "/config" , func ( ) {
m . Get ( "" , admin . Config )
m . Post ( "" , admin . ChangeConfig )
m . Post ( "/test_mail" , admin . SendTestMail )
2024-06-17 21:22:39 +02:00
m . Post ( "/test_cache" , admin . TestCache )
2024-02-24 14:12:17 +01:00
m . Get ( "/settings" , admin . ConfigSettings )
2022-10-17 01:29:26 +02:00
} )
2020-01-07 12:23:09 +01:00
m . Group ( "/monitor" , func ( ) {
2023-06-03 16:03:41 +02:00
m . Get ( "/stats" , admin . MonitorStats )
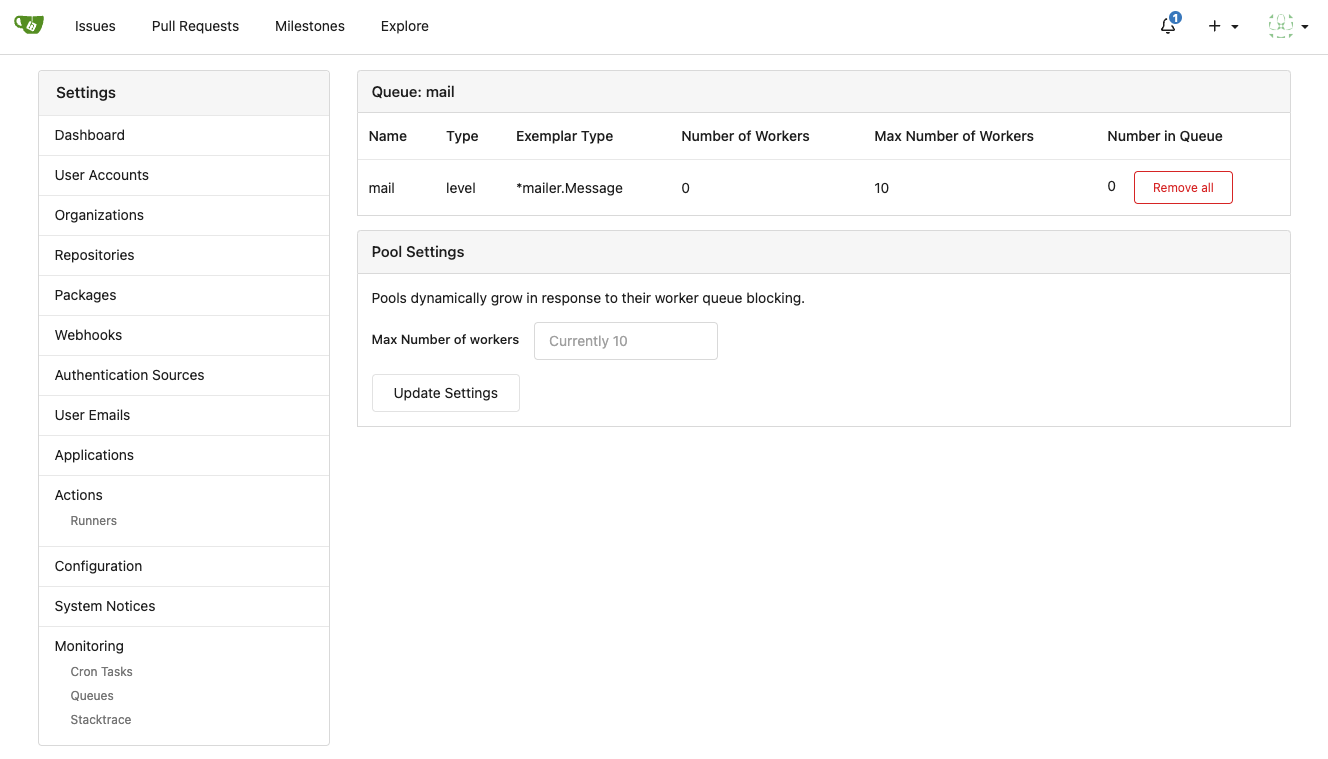
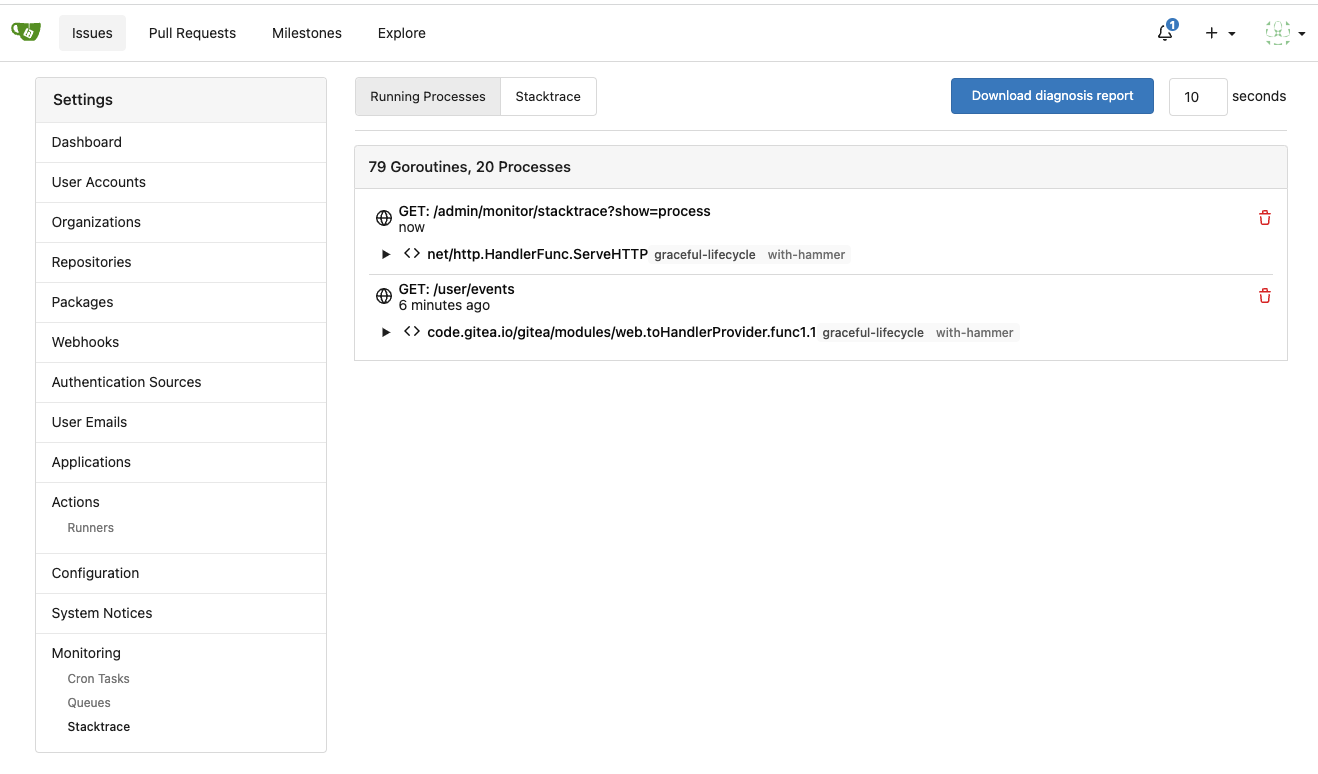
Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:

---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
m . Get ( "/cron" , admin . CronTasks )
m . Get ( "/stacktrace" , admin . Stacktrace )
m . Post ( "/stacktrace/cancel/{pid}" , admin . StacktraceCancel )
m . Get ( "/queue" , admin . Queues )
2021-01-26 16:36:53 +01:00
m . Group ( "/queue/{qid}" , func ( ) {
Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
m . Get ( "" , admin . QueueManage )
Rewrite queue (#24505)
# ⚠️ Breaking
Many deprecated queue config options are removed (actually, they should
have been removed in 1.18/1.19).
If you see the fatal message when starting Gitea: "Please update your
app.ini to remove deprecated config options", please follow the error
messages to remove these options from your app.ini.
Example:
```
2023/05/06 19:39:22 [E] Removed queue option: `[indexer].ISSUE_INDEXER_QUEUE_TYPE`. Use new options in `[queue.issue_indexer]`
2023/05/06 19:39:22 [E] Removed queue option: `[indexer].UPDATE_BUFFER_LEN`. Use new options in `[queue.issue_indexer]`
2023/05/06 19:39:22 [F] Please update your app.ini to remove deprecated config options
```
Many options in `[queue]` are are dropped, including:
`WRAP_IF_NECESSARY`, `MAX_ATTEMPTS`, `TIMEOUT`, `WORKERS`,
`BLOCK_TIMEOUT`, `BOOST_TIMEOUT`, `BOOST_WORKERS`, they can be removed
from app.ini.
# The problem
The old queue package has some legacy problems:
* complexity: I doubt few people could tell how it works.
* maintainability: Too many channels and mutex/cond are mixed together,
too many different structs/interfaces depends each other.
* stability: due to the complexity & maintainability, sometimes there
are strange bugs and difficult to debug, and some code doesn't have test
(indeed some code is difficult to test because a lot of things are mixed
together).
* general applicability: although it is called "queue", its behavior is
not a well-known queue.
* scalability: it doesn't seem easy to make it work with a cluster
without breaking its behaviors.
It came from some very old code to "avoid breaking", however, its
technical debt is too heavy now. It's a good time to introduce a better
"queue" package.
# The new queue package
It keeps using old config and concept as much as possible.
* It only contains two major kinds of concepts:
* The "base queue": channel, levelqueue, redis
* They have the same abstraction, the same interface, and they are
tested by the same testing code.
* The "WokerPoolQueue", it uses the "base queue" to provide "worker
pool" function, calls the "handler" to process the data in the base
queue.
* The new code doesn't do "PushBack"
* Think about a queue with many workers, the "PushBack" can't guarantee
the order for re-queued unhandled items, so in new code it just does
"normal push"
* The new code doesn't do "pause/resume"
* The "pause/resume" was designed to handle some handler's failure: eg:
document indexer (elasticsearch) is down
* If a queue is paused for long time, either the producers blocks or the
new items are dropped.
* The new code doesn't do such "pause/resume" trick, it's not a common
queue's behavior and it doesn't help much.
* If there are unhandled items, the "push" function just blocks for a
few seconds and then re-queue them and retry.
* The new code doesn't do "worker booster"
* Gitea's queue's handlers are light functions, the cost is only the
go-routine, so it doesn't make sense to "boost" them.
* The new code only use "max worker number" to limit the concurrent
workers.
* The new "Push" never blocks forever
* Instead of creating more and more blocking goroutines, return an error
is more friendly to the server and to the end user.
There are more details in code comments: eg: the "Flush" problem, the
strange "code.index" hanging problem, the "immediate" queue problem.
Almost ready for review.
TODO:
* [x] add some necessary comments during review
* [x] add some more tests if necessary
* [x] update documents and config options
* [x] test max worker / active worker
* [x] re-run the CI tasks to see whether any test is flaky
* [x] improve the `handleOldLengthConfiguration` to provide more
friendly messages
* [x] fine tune default config values (eg: length?)
## Code coverage:

2023-05-08 13:49:59 +02:00
m . Post ( "/set" , admin . QueueSet )
Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
m . Post ( "/remove-all-items" , admin . QueueRemoveAllItems )
2020-01-07 12:23:09 +01:00
} )
Improve queue & process & stacktrace (#24636)
Although some features are mixed together in this PR, this PR is not
that large, and these features are all related.
Actually there are more than 70 lines are for a toy "test queue", so
this PR is quite simple.
Major features:
1. Allow site admin to clear a queue (remove all items in a queue)
* Because there is no transaction, the "unique queue" could be corrupted
in rare cases, that's unfixable.
* eg: the item is in the "set" but not in the "list", so the item would
never be able to be pushed into the queue.
* Now site admin could simply clear the queue, then everything becomes
correct, the lost items could be re-pushed into queue by future
operations.
3. Split the "admin/monitor" to separate pages
4. Allow to download diagnosis report
* In history, there were many users reporting that Gitea queue gets
stuck, or Gitea's CPU is 100%
* With diagnosis report, maintainers could know what happens clearly
The diagnosis report sample:
[gitea-diagnosis-20230510-192913.zip](https://github.com/go-gitea/gitea/files/11441346/gitea-diagnosis-20230510-192913.zip)
, use "go tool pprof profile.dat" to view the report.
Screenshots:



---------
Co-authored-by: Jason Song <i@wolfogre.com>
Co-authored-by: Giteabot <teabot@gitea.io>
2023-05-11 09:45:47 +02:00
m . Get ( "/diagnosis" , admin . MonitorDiagnosis )
2020-01-07 12:23:09 +01:00
} )
2017-04-25 09:24:51 +02:00
m . Group ( "/users" , func ( ) {
m . Get ( "" , admin . Users )
2022-12-12 09:09:26 +01:00
m . Combo ( "/new" ) . Get ( admin . NewUser ) . Post ( web . Bind ( forms . AdminCreateUserForm { } ) , admin . NewUserPost )
2023-08-31 11:21:18 +02:00
m . Get ( "/{userid}" , admin . ViewUser )
m . Combo ( "/{userid}/edit" ) . Get ( admin . EditUser ) . Post ( web . Bind ( forms . AdminEditUserForm { } ) , admin . EditUserPost )
2021-01-26 16:36:53 +01:00
m . Post ( "/{userid}/delete" , admin . DeleteUser )
2022-12-12 09:09:26 +01:00
m . Post ( "/{userid}/avatar" , web . Bind ( forms . AvatarForm { } ) , admin . AvatarPost )
2021-11-16 20:13:13 +01:00
m . Post ( "/{userid}/avatar/delete" , admin . DeleteAvatar )
2017-04-25 09:24:51 +02:00
} )
2020-03-02 19:25:36 +01:00
m . Group ( "/emails" , func ( ) {
m . Get ( "" , admin . Emails )
m . Post ( "/activate" , admin . ActivateEmail )
2024-07-25 12:11:04 +02:00
m . Post ( "/delete" , admin . DeleteEmail )
2020-03-02 19:25:36 +01:00
} )
2017-04-25 09:24:51 +02:00
m . Group ( "/orgs" , func ( ) {
m . Get ( "" , admin . Organizations )
} )
m . Group ( "/repos" , func ( ) {
m . Get ( "" , admin . Repos )
2020-09-25 06:09:23 +02:00
m . Combo ( "/unadopted" ) . Get ( admin . UnadoptedRepos ) . Post ( admin . AdoptOrDeleteRepository )
2017-04-25 09:24:51 +02:00
m . Post ( "/delete" , admin . DeleteRepo )
} )
2022-11-20 15:08:38 +01:00
m . Group ( "/packages" , func ( ) {
m . Get ( "" , admin . Packages )
m . Post ( "/delete" , admin . DeletePackageVersion )
2023-08-08 02:46:10 +02:00
m . Post ( "/cleanup" , admin . CleanupExpiredData )
2022-11-20 15:08:38 +01:00
} , packagesEnabled )
2022-03-30 10:42:47 +02:00
2021-01-15 00:24:03 +01:00
m . Group ( "/hooks" , func ( ) {
2020-03-08 23:08:05 +01:00
m . Get ( "" , admin . DefaultOrSystemWebhooks )
m . Post ( "/delete" , admin . DeleteDefaultOrSystemWebhook )
2022-01-05 22:00:20 +01:00
m . Group ( "/{id}" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "" , repo_setting . WebhookEdit )
2024-03-21 14:33:59 +01:00
m . Post ( "" , repo_setting . WebhookUpdate )
2024-03-21 14:43:43 +01:00
m . Post ( "/replay/{uuid}" , repo_setting . WebhookReplay )
2022-01-05 22:00:20 +01:00
} )
2021-02-11 18:34:34 +01:00
} , webhooksEnabled )
2019-03-19 03:33:20 +01:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{configType:default-hooks|system-hooks}" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "/{type}/new" , repo_setting . WebhookNew )
2024-03-21 14:15:56 +01:00
m . Post ( "/{type}/new" , repo_setting . WebhookCreate )
2021-01-15 00:24:03 +01:00
} )
2017-04-25 09:24:51 +02:00
m . Group ( "/auths" , func ( ) {
m . Get ( "" , admin . Authentications )
2022-12-12 09:09:26 +01:00
m . Combo ( "/new" ) . Get ( admin . NewAuthSource ) . Post ( web . Bind ( forms . AuthenticationForm { } ) , admin . NewAuthSourcePost )
2021-01-26 16:36:53 +01:00
m . Combo ( "/{authid}" ) . Get ( admin . EditAuthSource ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . AuthenticationForm { } ) , admin . EditAuthSourcePost )
2021-01-26 16:36:53 +01:00
m . Post ( "/{authid}/delete" , admin . DeleteAuthSource )
2017-04-25 09:24:51 +02:00
} )
m . Group ( "/notices" , func ( ) {
m . Get ( "" , admin . Notices )
m . Post ( "/delete" , admin . DeleteNotices )
2020-02-26 17:25:54 +01:00
m . Post ( "/empty" , admin . EmptyNotices )
2017-04-25 09:24:51 +02:00
} )
2022-10-12 16:08:29 +02:00
m . Group ( "/applications" , func ( ) {
m . Get ( "" , admin . Applications )
2022-12-12 09:09:26 +01:00
m . Post ( "/oauth2" , web . Bind ( forms . EditOAuth2ApplicationForm { } ) , admin . ApplicationsPost )
2022-10-12 16:08:29 +02:00
m . Group ( "/oauth2/{id}" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Combo ( "" ) . Get ( admin . EditApplication ) . Post ( web . Bind ( forms . EditOAuth2ApplicationForm { } ) , admin . EditApplicationPost )
2022-10-12 16:08:29 +02:00
m . Post ( "/regenerate_secret" , admin . ApplicationsRegenerateSecret )
m . Post ( "/delete" , admin . DeleteApplication )
} )
2024-11-12 22:33:35 +01:00
} , oauth2Enabled )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
2023-04-28 02:08:47 +02:00
m . Group ( "/actions" , func ( ) {
m . Get ( "" , admin . RedirectToDefaultSetting )
addSettingsRunnersRoutes ( )
2023-12-25 08:28:59 +01:00
addSettingsVariablesRoutes ( )
2023-04-28 02:08:47 +02:00
} )
2024-01-28 13:36:44 +01:00
} , adminReq , ctxDataSet ( "EnableOAuth2" , setting . OAuth2 . Enabled , "EnablePackages" , setting . Packages . Enabled ) )
2017-04-25 09:24:51 +02:00
// ***** END: Admin *****
m . Group ( "" , func ( ) {
2023-04-27 08:06:45 +02:00
m . Get ( "/{username}" , user . UsernameSubRoute )
2023-12-25 13:13:18 +01:00
m . Methods ( "GET, OPTIONS" , "/attachments/{uuid}" , optionsCorsHandler ( ) , repo . GetAttachment )
2017-04-25 09:24:51 +02:00
} , ignSignIn )
2024-02-27 08:12:22 +01:00
m . Post ( "/{username}" , reqSignIn , context . UserAssignmentWeb ( ) , user . Action )
2017-04-25 09:24:51 +02:00
reqRepoAdmin := context . RequireRepoAdmin ( )
2021-11-09 20:57:58 +01:00
reqRepoCodeWriter := context . RequireRepoWriter ( unit . TypeCode )
2022-04-28 17:45:33 +02:00
canEnableEditor := context . CanEnableEditor ( )
2021-11-09 20:57:58 +01:00
reqRepoCodeReader := context . RequireRepoReader ( unit . TypeCode )
reqRepoReleaseWriter := context . RequireRepoWriter ( unit . TypeReleases )
reqRepoReleaseReader := context . RequireRepoReader ( unit . TypeReleases )
reqRepoWikiWriter := context . RequireRepoWriter ( unit . TypeWiki )
reqRepoIssueReader := context . RequireRepoReader ( unit . TypeIssues )
reqRepoPullsReader := context . RequireRepoReader ( unit . TypePullRequests )
reqRepoIssuesOrPullsWriter := context . RequireRepoWriterOr ( unit . TypeIssues , unit . TypePullRequests )
reqRepoIssuesOrPullsReader := context . RequireRepoReaderOr ( unit . TypeIssues , unit . TypePullRequests )
reqRepoProjectsReader := context . RequireRepoReader ( unit . TypeProjects )
reqRepoProjectsWriter := context . RequireRepoWriter ( unit . TypeProjects )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
reqRepoActionsReader := context . RequireRepoReader ( unit . TypeActions )
reqRepoActionsWriter := context . RequireRepoWriter ( unit . TypeActions )
2017-04-25 09:24:51 +02:00
2022-03-30 10:42:47 +02:00
reqPackageAccess := func ( accessMode perm . AccessMode ) func ( ctx * context . Context ) {
return func ( ctx * context . Context ) {
if ctx . Package . AccessMode < accessMode && ! ctx . IsUserSiteAdmin ( ) {
ctx . NotFound ( "" , nil )
}
}
}
2023-12-12 06:01:17 +01:00
individualPermsChecker := func ( ctx * context . Context ) {
// org permissions have been checked in context.OrgAssignment(), but individual permissions haven't been checked.
if ctx . ContextUser . IsIndividual ( ) {
switch {
case ctx . ContextUser . Visibility == structs . VisibleTypePrivate :
if ctx . Doer == nil || ( ctx . ContextUser . ID != ctx . Doer . ID && ! ctx . Doer . IsAdmin ) {
ctx . NotFound ( "Visit Project" , nil )
return
}
case ctx . ContextUser . Visibility == structs . VisibleTypeLimited :
if ctx . Doer == nil {
ctx . NotFound ( "Visit Project" , nil )
return
}
}
}
}
2017-04-25 09:24:51 +02:00
// ***** START: Organization *****
2022-07-15 16:21:54 +02:00
m . Group ( "/org" , func ( ) {
m . Group ( "/{org}" , func ( ) {
m . Get ( "/members" , org . Members )
} , context . OrgAssignment ( ) )
} , ignSignIn )
2017-04-25 09:24:51 +02:00
m . Group ( "/org" , func ( ) {
m . Group ( "" , func ( ) {
m . Get ( "/create" , org . Create )
2022-12-12 09:09:26 +01:00
m . Post ( "/create" , web . Bind ( forms . CreateOrgForm { } ) , org . CreatePost )
2017-04-25 09:24:51 +02:00
} )
2022-10-19 14:40:28 +02:00
m . Group ( "/invite/{token}" , func ( ) {
m . Get ( "" , org . TeamInvite )
m . Post ( "" , org . TeamInvitePost )
} )
2021-01-26 16:36:53 +01:00
m . Group ( "/{org}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Get ( "/dashboard" , user . Dashboard )
2021-01-26 16:36:53 +01:00
m . Get ( "/dashboard/{team}" , user . Dashboard )
2021-01-13 05:19:17 +01:00
m . Get ( "/issues" , user . Issues )
2021-01-26 16:36:53 +01:00
m . Get ( "/issues/{team}" , user . Issues )
2021-01-13 05:19:17 +01:00
m . Get ( "/pulls" , user . Pulls )
2021-01-26 16:36:53 +01:00
m . Get ( "/pulls/{team}" , user . Pulls )
2019-12-15 15:20:08 +01:00
m . Get ( "/milestones" , reqMilestonesDashboardPageEnabled , user . Milestones )
2021-01-26 16:36:53 +01:00
m . Get ( "/milestones/{team}" , reqMilestonesDashboardPageEnabled , user . Milestones )
m . Post ( "/members/action/{action}" , org . MembersAction )
2017-04-25 09:24:51 +02:00
m . Get ( "/teams" , org . Teams )
2020-12-27 20:58:03 +01:00
} , context . OrgAssignment ( true , false , true ) )
2017-04-25 09:24:51 +02:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{org}" , func ( ) {
m . Get ( "/teams/{team}" , org . TeamMembers )
m . Get ( "/teams/{team}/repositories" , org . TeamRepositories )
m . Post ( "/teams/{team}/action/{action}" , org . TeamsAction )
m . Post ( "/teams/{team}/action/repo/{action}" , org . TeamsRepoAction )
2017-04-25 09:24:51 +02:00
} , context . OrgAssignment ( true , false , true ) )
2024-08-29 15:26:25 +02:00
// require admin permission
m . Group ( "/{org}" , func ( ) {
m . Get ( "/teams/-/search" , org . SearchTeam )
} , context . OrgAssignment ( true , false , false , true ) )
// require owner permission
2021-01-26 16:36:53 +01:00
m . Group ( "/{org}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Get ( "/teams/new" , org . NewTeam )
2022-12-12 09:09:26 +01:00
m . Post ( "/teams/new" , web . Bind ( forms . CreateTeamForm { } ) , org . NewTeamPost )
2021-01-26 16:36:53 +01:00
m . Get ( "/teams/{team}/edit" , org . EditTeam )
2022-12-12 09:09:26 +01:00
m . Post ( "/teams/{team}/edit" , web . Bind ( forms . CreateTeamForm { } ) , org . EditTeamPost )
2021-01-26 16:36:53 +01:00
m . Post ( "/teams/{team}/delete" , org . DeleteTeam )
2017-04-25 09:24:51 +02:00
m . Group ( "/settings" , func ( ) {
m . Combo ( "" ) . Get ( org . Settings ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . UpdateOrgSettingForm { } ) , org . SettingsPost )
m . Post ( "/avatar" , web . Bind ( forms . AvatarForm { } ) , org . SettingsAvatar )
2017-04-25 09:24:51 +02:00
m . Post ( "/avatar/delete" , org . SettingsDeleteAvatar )
2022-10-09 14:07:41 +02:00
m . Group ( "/applications" , func ( ) {
m . Get ( "" , org . Applications )
2022-12-12 09:09:26 +01:00
m . Post ( "/oauth2" , web . Bind ( forms . EditOAuth2ApplicationForm { } ) , org . OAuthApplicationsPost )
2022-10-09 14:07:41 +02:00
m . Group ( "/oauth2/{id}" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Combo ( "" ) . Get ( org . OAuth2ApplicationShow ) . Post ( web . Bind ( forms . EditOAuth2ApplicationForm { } ) , org . OAuth2ApplicationEdit )
2022-10-09 14:07:41 +02:00
m . Post ( "/regenerate_secret" , org . OAuthApplicationsRegenerateSecret )
m . Post ( "/delete" , org . DeleteOAuth2Application )
} )
2024-11-12 22:33:35 +01:00
} , oauth2Enabled )
2017-04-25 09:24:51 +02:00
m . Group ( "/hooks" , func ( ) {
m . Get ( "" , org . Webhooks )
m . Post ( "/delete" , org . DeleteWebhook )
2024-03-21 14:43:43 +01:00
m . Get ( "/{type}/new" , repo_setting . WebhookNew )
2024-03-21 14:15:56 +01:00
m . Post ( "/{type}/new" , repo_setting . WebhookCreate )
2022-01-05 22:00:20 +01:00
m . Group ( "/{id}" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "" , repo_setting . WebhookEdit )
2024-03-21 14:33:59 +01:00
m . Post ( "" , repo_setting . WebhookUpdate )
2024-03-21 14:43:43 +01:00
m . Post ( "/replay/{uuid}" , repo_setting . WebhookReplay )
2022-01-05 22:00:20 +01:00
} )
2023-04-28 02:08:47 +02:00
} , webhooksEnabled )
2017-04-25 09:24:51 +02:00
Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
m . Group ( "/labels" , func ( ) {
m . Get ( "" , org . RetrieveLabels , org . Labels )
2022-12-12 09:09:26 +01:00
m . Post ( "/new" , web . Bind ( forms . CreateLabelForm { } ) , org . NewLabel )
m . Post ( "/edit" , web . Bind ( forms . CreateLabelForm { } ) , org . UpdateLabel )
Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
m . Post ( "/delete" , org . DeleteLabel )
2022-12-12 09:09:26 +01:00
m . Post ( "/initialize" , web . Bind ( forms . InitializeLabelsForm { } ) , org . InitializeLabels )
Add Organization Wide Labels (#10814)
* Add organization wide labels
Implement organization wide labels similar to organization wide
webhooks. This lets you create individual labels for organizations that can be used
for all repos under that organization (so being able to reuse the same
label across multiple repos).
This makes it possible for small organizations with many repos to use
labels effectively.
Fixes #7406
* Add migration
* remove comments
* fix tests
* Update options/locale/locale_en-US.ini
Removed unused translation string
* show org labels in issue search label filter
* Use more clear var name
* rename migration after merge from master
* comment typo
* update migration again after rebase with master
* check for orgID <=0 per guillep2k review
* fmt
* Apply suggestions from code review
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* remove unused code
* Make sure RepoID is 0 when searching orgID per code review
* more changes/code review requests
* More descriptive translation var per code review
* func description/delete comment when issue label deleted instead of hiding it
* remove comment
* only use issues in that repo when calculating number of open issues for org label on repo label page
* Add integration test for IssuesSearch API with labels
* remove unused function
* Update models/issue_label.go
Co-Authored-By: guillep2k <18600385+guillep2k@users.noreply.github.com>
* Use subquery in GetLabelIDsInReposByNames
* Fix tests to use correct orgID
* fix more tests
* IssuesSearch api now uses new BuildLabelNamesIssueIDsCondition. Add a few more tests as well
* update comment for clarity
* Revert previous code change now that we can use the new BuildLabelNamesIssueIDsCondition
* Don't sort repos by date in IssuesSearch API
After much debugging I've found a strange issue where in some cases MySQL will return a different result than other enigines if a query is sorted by a null collumn. For example with our integration test data where we don't set updated_unix in repository fixtures:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 45
Returns different results for MySQL than other engines. However, the similar query:
SELECT `id`, `owner_id`, `owner_name`, `lower_name`, `name`, `description`, `website`, `original_service_type`, `original_url`, `default_branch`, `num_watches`, `num_stars`, `num_forks`, `num_issues`, `num_closed_issues`, `num_pulls`, `num_closed_pulls`, `num_milestones`, `num_closed_milestones`, `is_private`, `is_empty`, `is_archived`, `is_mirror`, `status`, `is_fork`, `fork_id`, `is_template`, `template_id`, `size`, `is_fsck_enabled`, `close_issues_via_commit_in_any_branch`, `topics`, `avatar`, `created_unix`, `updated_unix` FROM `repository` ORDER BY updated_unix DESC LIMIT 15 OFFSET 30
Returns the same results.
This causes integration tests to fail on MySQL in certain cases but would never show up in a real installation. Since this API call always returns issues based on the optionally provided repo_priority_id or the issueID itself, there is no change to results by changing the repo sorting method used to get ids earlier in the function.
* linter is back!
* code review
* remove now unused option
* Fix newline at end of files
* more unused code
* update to master
* check for matching ids before query
* Update models/issue_label.go
Co-Authored-By: 6543 <6543@obermui.de>
* Update models/issue_label.go
* update comments
* Update routers/org/setting.go
Co-authored-by: Lauris BH <lauris@nix.lv>
Co-authored-by: guillep2k <18600385+guillep2k@users.noreply.github.com>
Co-authored-by: 6543 <6543@obermui.de>
2020-04-01 06:14:46 +02:00
} )
2023-04-28 02:08:47 +02:00
m . Group ( "/actions" , func ( ) {
m . Get ( "" , org_setting . RedirectToDefaultSetting )
addSettingsRunnersRoutes ( )
addSettingsSecretsRoutes ( )
2023-12-25 08:28:59 +01:00
addSettingsVariablesRoutes ( )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
} , actions . MustEnableActions )
2023-07-21 00:43:49 +02:00
m . Methods ( "GET,POST" , "/delete" , org . SettingsDelete )
2022-11-20 15:08:38 +01:00
[MODERATION] User blocking
- Add the ability to block a user via their profile page.
- This will unstar their repositories and visa versa.
- Blocked users cannot create issues or pull requests on your the doer's repositories (mind that this is not the case for organizations).
- Blocked users cannot comment on the doer's opened issues or pull requests.
- Blocked users cannot add reactions to doer's comments.
- Blocked users cannot cause a notification trough mentioning the doer.
Reviewed-on: https://codeberg.org/forgejo/forgejo/pulls/540
(cherry picked from commit 687d852480388897db4d7b0cb397cf7135ab97b1)
(cherry picked from commit 0c32a4fde531018f74e01d9db6520895fcfa10cc)
(cherry picked from commit 1791130e3cb8470b9b39742e0004d5e4c7d1e64d)
(cherry picked from commit 37858b7e8fb6ba6c6ea0ac2562285b3b144efa19)
(cherry picked from commit a3e2bfd7e9eab82cc2c17061f6bb4e386a108c46)
(cherry picked from commit 7009b9fe87696b6182fab65ae82bf5a25cd39971)
Conflicts: https://codeberg.org/forgejo/forgejo/pulls/1014
routers/web/user/profile.go
templates/user/profile.tmpl
(cherry picked from commit b2aec3479177e725cfc7cbbb9d94753226928d1c)
(cherry picked from commit e2f1b73752f6bd3f830297d8f4ac438837471226)
[MODERATION] organization blocking a user (#802)
- Resolves #476
- Follow up for: #540
- Ensure that the doer and blocked person cannot follow each other.
- Ensure that the block person cannot watch doer's repositories.
- Add unblock button to the blocked user list.
- Add blocked since information to the blocked user list.
- Add extra testing to moderation code.
- Blocked user will unwatch doer's owned repository upon blocking.
- Add flash messages to let the user know the block/unblock action was successful.
- Add "You haven't blocked any users" message.
- Add organization blocking a user.
Co-authored-by: Gusted <postmaster@gusted.xyz>
Reviewed-on: https://codeberg.org/forgejo/forgejo/pulls/802
(cherry picked from commit 0505a1042197bd9136b58bc70ec7400a23471585)
(cherry picked from commit 37b4e6ef9b85e97d651cf350c9f3ea272ee8d76a)
(cherry picked from commit c17c121f2cf1f00e2a8d6fd6847705df47d0771e)
[MODERATION] organization blocking a user (#802) (squash)
Changes to adapt to:
6bbccdd177 Improve AJAX link and modal confirm dialog (#25210)
Refs: https://codeberg.org/forgejo/forgejo/pulls/882/files#issuecomment-945962
Refs: https://codeberg.org/forgejo/forgejo/pulls/882#issue-330561
(cherry picked from commit 523635f83cb2a1a4386769b79326088c5c4bbec7)
(cherry picked from commit 4743eaa6a0be0ef47de5b17c211dfe8bad1b7af9)
(cherry picked from commit eff5b43d2e843d5d537756d4fa58a8a010b6b527)
Conflicts: https://codeberg.org/forgejo/forgejo/pulls/1014
routers/web/user/profile.go
(cherry picked from commit 9d359be5ed11237088ccf6328571939af814984e)
(cherry picked from commit b1f3069a22a03734cffbfcd503ce004ba47561b7)
[MODERATION] add user blocking API
- Follow up for: #540, #802
- Add API routes for user blocking from user and organization
perspective.
- The new routes have integration testing.
- The new model functions have unit tests.
- Actually quite boring to write and to read this pull request.
(cherry picked from commit f3afaf15c7e34038363c9ce8e1ef957ec1e22b06)
(cherry picked from commit 6d754db3e5faff93a58fab2867737f81f40f6599)
(cherry picked from commit 2a89ddc0acffa9aea0f02b721934ef9e2b496a88)
(cherry picked from commit 4a147bff7e963ab9dffcfaefa5c2c01c59b4c732)
Conflicts:
routers/api/v1/api.go
templates/swagger/v1_json.tmpl
(cherry picked from commit bb8c33918569f65f25b014f0d7fe6ac20f9036fc)
(cherry picked from commit 5a11569a011b7d0a14391e2b5c07d0af825d7b0e)
(cherry picked from commit 2373c801ee6b84c368b498b16e6ad18650b38f42)
[MODERATION] restore redirect on unblock
ctx.RedirectToFirst(ctx.FormString("redirect_to"), ctx.ContextUser.HomeLink())
was replaced by
ctx.JSONOK()
in 128d77a3a Following up fixes for "Fix inconsistent user profile layout across tabs" (#25739)
thus changing the behavior (nicely spotted by the tests). This
restores it.
(cherry picked from commit 597c243707c3c86e7256faf1e6ba727224554de3)
(cherry picked from commit cfa539e590127b4b953b010fba3dea21c82a1714)
[MODERATION] Add test case (squash)
- Add an test case, to test an property of the function.
(cherry picked from commit 70dadb1916bfef8ba8cbc4e9b042cc8740f45e28)
[MODERATION] Block adding collaborators
- Ensure that the doer and blocked user cannot add each other as
collaborators to repositories.
- The Web UI gets an detailed message of the specific situation, the API
gets an generic Forbidden code.
- Unit tests has been added.
- Integration testing for Web and API has been added.
- This commit doesn't introduce removing each other as collaborators on
the block action, due to the complexity of database calls that needs to
be figured out. That deserves its own commit and test code.
(cherry picked from commit 747be949a1b3cd06f6586512f1af4630e55d7ad4)
[MODERATION] move locale_en-US.ini strings to avoid conflicts
Conflicts:
web_src/css/org.css
web_src/css/user.css
https://codeberg.org/forgejo/forgejo/pulls/1180
(cherry picked from commit e53f955c888ebaafc863a6e463da87f70f5605da)
Conflicts:
services/issue/comments.go
https://codeberg.org/forgejo/forgejo/pulls/1212
(cherry picked from commit b4a454b576eee0c7738b2f7df1acaf5bf7810d12)
Conflicts:
models/forgejo_migrations/migrate.go
options/locale/locale_en-US.ini
services/pull/pull.go
https://codeberg.org/forgejo/forgejo/pulls/1264
[MODERATION] Remove blocked user collaborations with doer
- When the doer blocks an user, who is also an collaborator on an
repository that the doer owns, remove that collaboration.
- Added unit tests.
- Refactor the unit test to be more organized.
(cherry picked from commit ec8701617830152680d69d50d64cb43cc2054a89)
(cherry picked from commit 313e6174d832501c57724ae7a6285194b7b81aab)
[MODERATION] QoL improvements (squash)
- Ensure that organisations cannot be blocked. It currently has no
effect, as all blocked operations cannot be executed from an
organisation standpoint.
- Refactored the API route to make use of the `UserAssignmentAPI`
middleware.
- Make more use of `t.Run` so that the test code is more clear about
which block of code belongs to which test case.
- Added more integration testing (to ensure the organisations cannot be
blocked and some authorization/permission checks).
(cherry picked from commit e9d638d0756ee20b6bf1eb999c988533a5066a68)
[MODERATION] s/{{avatar/{{ctx.AvatarUtils.Avatar/
(cherry picked from commit ce8b30be1327ab98df2ba061dd7e2a278b278c5b)
(cherry picked from commit f911dc402508b04cd5d5fb2f3332c2d640e4556e)
Conflicts:
options/locale/locale_en-US.ini
https://codeberg.org/forgejo/forgejo/pulls/1354
(cherry picked from commit c1b37b7fdaf06ee60da341dff76d703990c08082)
(cherry picked from commit 856a2e09036adf56d987c6eee364c431bc37fb2e)
[MODERATION] Show graceful error on comment creation
- When someone is blocked by the repository owner or issue poster and
try to comment on that issue, they get shown a graceful error.
- Adds integration test.
(cherry picked from commit 490646302e1e3dc3c59c9d75938b4647b6873ce7)
(cherry picked from commit d3d88667cbb928a6ff80658eba8ef0c6c508c9e0)
(cherry picked from commit 6818de13a921753e082b7c3d64c23917cc884e4b)
[MODERATION] Show graceful error on comment creation (squash) typo
(cherry picked from commit 1588d4834a37a744f092f2aeea6c9ef4795d7356)
(cherry picked from commit d510ea52d091503e841d66f2f604348add8b4535)
(cherry picked from commit 8249e93a14f628bb0e89fe3be678e4966539944e)
[MODERATION] Refactor integration testing (squash)
- Motivation for this PR is that I'd noticed that a lot of repeated
calls are happening between the test functions and that certain tests
weren't using helper functions like `GetCSRF`, therefor this refactor of
the integration tests to keep it: clean, small and hopefully more
maintainable and understandable.
- There are now three integration tests: `TestBlockUser`,
`TestBlockUserFromOrganization` and `TestBlockActions` (and has been
moved in that order in the source code).
- `TestBlockUser` is for doing blocking related actions as an user and
`TestBlockUserFromOrganization` as an organisation, even though they
execute the same kind of tests they do not share any database calls or
logic and therefor it currently doesn't make sense to merge them
together (hopefully such oppurtinutiy might be presented in the future).
- `TestBlockActions` now contain all tests for actions that should be
blocked after blocking has happened, most tests now share the same doer
and blocked users and a extra fixture has been added to make this
possible for the comment test.
- Less code, more comments and more re-use between tests.
(cherry picked from commit ffb393213d2f1269aad3c019d039cf60d0fe4b10)
(cherry picked from commit 85505e0f815fede589c272d301c95204f9596985)
(cherry picked from commit 0f3cf17761f6caedb17550f69de96990c2090af1)
[MODERATION] Fix network error (squash)
- Fix network error toast messages on user actions such as follow and
unfollow. This happened because the javascript code now expects an JSON
to be returned, but this wasn't the case due to
cfa539e590127b4953b010fba3dea21c82a1714.
- The integration testing has been adjusted to instead test for the
returned flash cookie.
(cherry picked from commit 112bc25e548d317a4ee00f9efa9068794a733e3b)
(cherry picked from commit 1194fe4899eb39dcb9a2410032ad0cc67a62b92b)
(cherry picked from commit 9abb95a8441e227874fe156095349a3173cc5a81)
[MODERATION] Modernize frontend (squash)
- Unify blocked users list.
- Use the new flex list classes for blocked users list to avoid using
the CSS helper classes and thereby be consistent in the design.
- Fix the modal by using the new modal class.
- Remove the icon in the modal as looks too big in the new design.
- Fix avatar not displaying as it was passing the context where the user
should've been passed.
- Don't use italics for 'Blocked since' text.
- Use namelink template to display the user's name and homelink.
(cherry picked from commit ec935a16a319b14e819ead828d1d9875280d9259)
(cherry picked from commit 67f37c83461aa393c53a799918e9708cb9b89b30)
Conflicts:
models/user/follow.go
models/user/user_test.go
routers/api/v1/user/follower.go
routers/web/shared/user/header.go
routers/web/user/profile.go
templates/swagger/v1_json.tmpl
https://codeberg.org/forgejo/forgejo/pulls/1468
(cherry picked from commit 6a9626839c6342cd2767ea12757ee2f78eaf443b)
Conflicts:
tests/integration/api_nodeinfo_test.go
https://codeberg.org/forgejo/forgejo/pulls/1508#issuecomment-1242385
(cherry picked from commit 7378b251b481ed1e60e816caf8f649e8397ee5fc)
Conflicts:
models/fixtures/watch.yml
models/issues/reaction.go
models/issues/reaction_test.go
routers/api/v1/repo/issue_reaction.go
routers/web/repo/issue.go
services/issue/issue.go
https://codeberg.org/forgejo/forgejo/pulls/1547
(cherry picked from commit c2028930c101223820de0bbafc318e9394c347b8)
(cherry picked from commit d3f9134aeeef784586e8412e8dbba0a8fceb0cd4)
(cherry picked from commit 7afe154c5c40bcc65accdf51c9224b2f7627a684)
(cherry picked from commit 99ac7353eb1e834a77fe42aa89208791cc2364ff)
(cherry picked from commit a9cde00c5c25ea8c427967cb7ab57abb618e44cb)
Conflicts:
services/user/delete.go
https://codeberg.org/forgejo/forgejo/pulls/1736
(cherry picked from commit 008c0cc63d1a3b8eb694bffbf77a7b25c56afd57)
[DEADCODE] add exceptions
(cherry picked from commit 12ddd2b10e3309f6430b0af42855c6af832832ee)
[MODERATION] Remove deadcode (squash)
- Remove deadcode that's no longer used by Forgejo.
(cherry picked from commit 0faeab4fa9b0aa59f86760b24ecbc07815026c82)
[MODERATION] Add repo transfers to blocked functionality (squash)
- When someone gets blocked, remove all pending repository transfers
from the blocked user to the doer.
- Do not allow to start transferring repositories to the doer as blocked user.
- Added unit testing.
- Added integration testing.
(cherry picked from commit 8a3caac33013482ddbee2fa51510c6918ba54466)
(cherry picked from commit a92b4cfeb63b90eb2d90d0feb51cec62e0502d84)
(cherry picked from commit acaaaf07d999974dbe5f9c5e792621c597bfb542)
(cherry picked from commit 735818863c1793aa6f6983afedc4bd3b36026ca5)
(cherry picked from commit f50fa43b32160d0d88eca1dbdca09b5f575fb62b)
(cherry picked from commit e16683643388fb3c60ea478f1419a6af4f4aa283)
(cherry picked from commit 82a0e4a3814a66ce44be6a031bdf08484586c61b)
(cherry picked from commit ff233c19c4a5edcc2b99a6f41a2d19dbe8c08b3b)
(cherry picked from commit 8ad87d215f2b6adb978de77e53ba2bf7ea571430)
[MODERATION] Fix unblock action (squash)
- Pass the whole context instead of only giving pieces.
- This fixes CSRF not correctly being inserted into the unblock buttons.
(cherry picked from commit 2aa51922ba6a0ea2f8644277baa74fc8f34ab95a)
(cherry picked from commit 7ee8db0f018340bc97f125415503e3e5db5f5082)
(cherry picked from commit e4f8b999bcd3b68b3ef7f54f5b17c3ada0308121)
(cherry picked from commit 05aea60b1302bbd3ea574a9c6c34e1005a5d73bf)
(cherry picked from commit dc0d61b012cfaf2385f71e97cda5f220b58b9fa4)
(cherry picked from commit f53fa583de671ff60a0a1d0f3ab8c260e1ba4e1f)
(cherry picked from commit c65b89a58d11b32009c710c2f5e75f0cd3539395)
(cherry picked from commit 69e50b9969db3ab71cefaed520757876a9629a5c)
(cherry picked from commit ec127440b86cb5fcf51799d8bd76a9fd6b9cebcc)
[MODERATION] cope with shared fixtures
* There is one more issue in the fixtures and this breaks some tests
* The users in the shared fixtures were renamed for clarity and that
breaks some tests
(cherry picked from commit 707a4edbdf67d0eb168d7bb430cf85dd8cd63c52)
Conflicts:
modules/indexer/issues/indexer_test.go
https://codeberg.org/forgejo/forgejo/pulls/1508
(cherry picked from commit 82cc044366c749df80ffad44eed2988b8e64211e)
(cherry picked from commit 2776aec7e85850f1d7f01a090a72491550fb9d29)
(cherry picked from commit 1fbde36dc784b5b2cc6193f02ff0d436b0f2a629)
(cherry picked from commit 1293db3c4e5df218501f5add9f9d41101ffcb8aa)
(cherry picked from commit 6476802175bac3ef78dd8f24ff6bebc16f398a78)
(cherry picked from commit 5740f2fc830356acb7929a02fe304008b94a0ca5)
(cherry picked from commit afc12d7b6e9b773fa89718aa79cd95c0e0ce4406)
[MODERATION] Fix transfer confirmation (squash)
- Fix problem caused by the clearer confirmation for dangerous actions commit.
(cherry picked from commit 3488f4a9cb1f7f73103ae0017d644f13ca3ab798)
(cherry picked from commit ed7de91f6ace23a1459bc6552edf719d62c7c941)
(cherry picked from commit 2d97929b9b7b8d979eb12bf0994d3f169d41f7fd)
(cherry picked from commit 50d035a7b058b9c4486c38cd4be0b02a4e1bf4d9)
(cherry picked from commit 0a0c07d78a1dee3489b97ab359bb957e3f7fb94b)
(cherry picked from commit 85e55c4dbc2f513f3d5254dac20915e8c3c22886)
(cherry picked from commit d8282122ad6e8b497de35d1ed89e3093a2cd5ee2)
(cherry picked from commit 3f0b3b6cc582c3d672d371dd9fe1203a56cb88c0)
[MODERATION] Purge issues on user deletion (squash)
(cherry picked from commit 4f529d9596ffbfc4e754c28830ba028f6344dc5b)
(cherry picked from commit f0e3acadd321fcb99e8ea3e3ce1c69df25c4ca4d)
(cherry picked from commit 682c4effe69dc0d4ed304fa7ce6259d9ce573629)
(cherry picked from commit e43c2d84fd4b6fd31e2370cec1034262d12e5c34)
(cherry picked from commit 9c8e53ccc78053026e4f667889959c23c8d95934)
(cherry picked from commit a9eb7ac783b2c16ee3702a88203bf857cb4147fc)
[MODERATION] Purge issues on user deletion (squash) revert shared fixtures workarounds
(cherry picked from commit 7224653a40e32186892e89bfedd49edecf5b8f81)
(cherry picked from commit aa6e8672f9473a9100e7575051dec9eda37709a0)
(cherry picked from commit 58c7947e95648f50237ddcd46b6bd025b224a70f)
(cherry picked from commit f1aacb1851b232082febcd7870a40a56de3855a6)
(cherry picked from commit 0bf174af87f7de9a8d869304f709e2bf41f3dde9)
(cherry picked from commit f9706f4335df3b7688ed60853d917efa72fb464a)
[MODERATION] Prepare moderation for context locale changes (squash)
- Resolves https://codeberg.org/forgejo/forgejo/issues/1711
(cherry picked from commit 2e289baea943dcece88f02d110b03d344308a261)
(cherry picked from commit 97b16bc19ae680db62608d6020b00fe5ac451c60)
[MODERATION] User blocking (squash) do not use shared fixture
It conflicts with a fixtured added in the commit
Fix comment permissions (#28213) (#28216)
(cherry picked from commit ab40799dcab24e9f495d765268b791931da81684)
(cherry picked from commit 996c92cafdb5b33a6d2d05d94038e950d97eb7de)
(cherry picked from commit 259912e3a69071c5ad57871464d0b79f69a8e72c)
Conflicts:
options/locale/locale_en-US.ini
https://codeberg.org/forgejo/forgejo/pulls/1921
(cherry picked from commit 1e82abc032c18015b92c93a7617a5dd06d50bd2d)
(cherry picked from commit a176fee1607d571b25b345184f1c50d403029610)
(cherry picked from commit 0480b76dfeda968849e900da9454a3efd82590fa)
(cherry picked from commit 4bc06b7b3841c74e3d790b1ef635c2b382ca7123)
(cherry picked from commit 073094cf722a927a623408d66537c758d7d64e4c)
(cherry picked from commit ac6201c647a4d3a2cfb2b0303b851a8fe7a29444)
(cherry picked from commit 7e0812674da3fbd1e96bdda820962edad6826fbd)
(cherry picked from commit 068c741e5696957710b3d1c2e18c00be2ffaa278)
Conflicts:
models/repo_transfer.go
models/repo_transfer_test.go
routers/web/user/profile.go
https://codeberg.org/forgejo/forgejo/pulls/2298
2023-08-15 01:07:38 +02:00
m . Group ( "/blocked_users" , func ( ) {
m . Get ( "" , org_setting . BlockedUsers )
m . Post ( "/block" , org_setting . BlockedUsersBlock )
m . Post ( "/unblock" , org_setting . BlockedUsersUnblock )
} )
2022-11-20 15:08:38 +01:00
m . Group ( "/packages" , func ( ) {
m . Get ( "" , org . Packages )
m . Group ( "/rules" , func ( ) {
m . Group ( "/add" , func ( ) {
m . Get ( "" , org . PackagesRuleAdd )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . PackageCleanupRuleForm { } ) , org . PackagesRuleAddPost )
2022-11-20 15:08:38 +01:00
} )
m . Group ( "/{id}" , func ( ) {
m . Get ( "" , org . PackagesRuleEdit )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . PackageCleanupRuleForm { } ) , org . PackagesRuleEditPost )
2022-11-20 15:08:38 +01:00
m . Get ( "/preview" , org . PackagesRulePreview )
} )
} )
2023-02-05 11:12:31 +01:00
m . Group ( "/cargo" , func ( ) {
m . Post ( "/initialize" , org . InitializeCargoIndex )
m . Post ( "/rebuild" , org . RebuildCargoIndex )
} )
2022-11-20 15:08:38 +01:00
} , packagesEnabled )
2024-01-28 13:36:44 +01:00
} , ctxDataSet ( "EnableOAuth2" , setting . OAuth2 . Enabled , "EnablePackages" , setting . Packages . Enabled , "PageIsOrgSettings" , true ) )
2017-04-25 09:24:51 +02:00
} , context . OrgAssignment ( true , true ) )
} , reqSignIn )
// ***** END: Organization *****
// ***** START: Repository *****
m . Group ( "/repo" , func ( ) {
m . Get ( "/create" , repo . Create )
2022-12-12 09:09:26 +01:00
m . Post ( "/create" , web . Bind ( forms . CreateRepoForm { } ) , repo . CreatePost )
2017-04-25 09:24:51 +02:00
m . Get ( "/migrate" , repo . Migrate )
2022-12-12 09:09:26 +01:00
m . Post ( "/migrate" , web . Bind ( forms . MigrateRepoForm { } ) , repo . MigratePost )
2024-02-25 11:58:23 +01:00
if ! setting . Repository . DisableForks {
m . Get ( "/fork/{repoid}" , context . RepoIDAssignment ( ) , context . UnitTypes ( ) , reqRepoCodeReader , repo . ForkByID )
}
2022-04-07 20:59:56 +02:00
m . Get ( "/search" , repo . SearchRepo )
2017-04-25 09:24:51 +02:00
} , reqSignIn )
2022-03-30 10:42:47 +02:00
m . Group ( "/{username}/-" , func ( ) {
2022-03-31 19:31:53 +02:00
if setting . Packages . Enabled {
m . Group ( "/packages" , func ( ) {
m . Get ( "" , user . ListPackages )
m . Group ( "/{type}/{name}" , func ( ) {
m . Get ( "" , user . RedirectToLastVersion )
m . Get ( "/versions" , user . ListPackageVersions )
m . Group ( "/{version}" , func ( ) {
m . Get ( "" , user . ViewPackageVersion )
m . Get ( "/files/{fileid}" , user . DownloadPackageFile )
m . Group ( "/settings" , func ( ) {
m . Get ( "" , user . PackageSettings )
2022-12-12 09:09:26 +01:00
m . Post ( "" , web . Bind ( forms . PackageSettingForm { } ) , user . PackageSettingsPost )
2022-03-31 19:31:53 +02:00
} , reqPackageAccess ( perm . AccessModeWrite ) )
} )
2022-03-30 10:42:47 +02:00
} )
2023-05-04 14:07:15 +02:00
} , context . PackageAssignment ( ) , reqPackageAccess ( perm . AccessModeRead ) )
2022-03-31 19:31:53 +02:00
}
2023-01-20 12:42:33 +01:00
m . Group ( "/projects" , func ( ) {
2023-03-10 16:18:20 +01:00
m . Group ( "" , func ( ) {
m . Get ( "" , org . Projects )
m . Get ( "/{id}" , org . ViewProject )
2023-07-29 16:13:24 +02:00
} , reqUnitAccess ( unit . TypeProjects , perm . AccessModeRead , true ) )
2023-01-20 12:42:33 +01:00
m . Group ( "" , func ( ) { //nolint:dupl
2023-05-31 08:50:18 +02:00
m . Get ( "/new" , org . RenderNewProject )
2023-01-20 12:42:33 +01:00
m . Post ( "/new" , web . Bind ( forms . CreateProjectForm { } ) , org . NewProjectPost )
m . Group ( "/{id}" , func ( ) {
2024-05-27 10:59:54 +02:00
m . Post ( "" , web . Bind ( forms . EditProjectColumnForm { } ) , org . AddColumnToProjectPost )
2024-05-08 15:44:57 +02:00
m . Post ( "/move" , project . MoveColumns )
2023-01-20 12:42:33 +01:00
m . Post ( "/delete" , org . DeleteProject )
2023-05-31 08:50:18 +02:00
m . Get ( "/edit" , org . RenderEditProject )
2023-01-20 12:42:33 +01:00
m . Post ( "/edit" , web . Bind ( forms . CreateProjectForm { } ) , org . EditProjectPost )
m . Post ( "/{action:open|close}" , org . ChangeProjectStatus )
2024-05-27 10:59:54 +02:00
m . Group ( "/{columnID}" , func ( ) {
m . Put ( "" , web . Bind ( forms . EditProjectColumnForm { } ) , org . EditProjectColumn )
m . Delete ( "" , org . DeleteProjectColumn )
m . Post ( "/default" , org . SetDefaultProjectColumn )
2023-01-20 12:42:33 +01:00
m . Post ( "/move" , org . MoveIssues )
} )
} )
2023-07-29 16:13:24 +02:00
} , reqSignIn , reqUnitAccess ( unit . TypeProjects , perm . AccessModeWrite , true ) , func ( ctx * context . Context ) {
2023-03-10 16:18:20 +01:00
if ctx . ContextUser . IsIndividual ( ) && ctx . ContextUser . ID != ctx . Doer . ID {
2023-01-20 12:42:33 +01:00
ctx . NotFound ( "NewProject" , nil )
return
}
} )
2023-12-12 06:01:17 +01:00
} , reqUnitAccess ( unit . TypeProjects , perm . AccessModeRead , true ) , individualPermsChecker )
2023-01-20 12:42:33 +01:00
2023-03-10 16:18:20 +01:00
m . Group ( "" , func ( ) {
m . Get ( "/code" , user . CodeSearch )
2023-12-12 06:01:17 +01:00
} , reqUnitAccess ( unit . TypeCode , perm . AccessModeRead , false ) , individualPermsChecker )
2024-02-27 08:12:22 +01:00
} , ignSignIn , context . UserAssignmentWeb ( ) , context . OrgAssignment ( ) ) // for "/{username}/-" (packages, projects, code)
2022-03-30 10:42:47 +02:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Group ( "/settings" , func ( ) {
2022-06-12 07:43:27 +02:00
m . Group ( "" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Combo ( "" ) . Get ( repo_setting . Settings ) .
Post ( web . Bind ( forms . RepoSettingForm { } ) , repo_setting . SettingsPost )
} , repo_setting . SettingsCtxData )
2024-01-23 10:46:34 +01:00
m . Combo ( "/units" ) . Get ( repo_setting . Units ) .
Post ( web . Bind ( forms . RepoUnitSettingForm { } ) , repo_setting . UnitsPost )
2023-07-02 02:59:32 +02:00
m . Post ( "/avatar" , web . Bind ( forms . AvatarForm { } ) , repo_setting . SettingsAvatar )
m . Post ( "/avatar/delete" , repo_setting . SettingsDeleteAvatar )
2019-05-30 04:22:26 +02:00
2017-04-25 09:24:51 +02:00
m . Group ( "/collaboration" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Combo ( "" ) . Get ( repo_setting . Collaboration ) . Post ( repo_setting . CollaborationPost )
m . Post ( "/access_mode" , repo_setting . ChangeCollaborationAccessMode )
m . Post ( "/delete" , repo_setting . DeleteCollaboration )
2019-09-23 22:08:03 +02:00
m . Group ( "/team" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Post ( "" , repo_setting . AddTeamPost )
m . Post ( "/delete" , repo_setting . DeleteTeam )
2019-09-23 22:08:03 +02:00
} )
2017-04-25 09:24:51 +02:00
} )
2021-06-25 16:28:55 +02:00
2017-04-25 09:24:51 +02:00
m . Group ( "/branches" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Post ( "/" , repo_setting . SetDefaultBranchPost )
2023-01-16 09:00:22 +01:00
} , repo . MustBeNotEmpty )
m . Group ( "/branches" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Get ( "/" , repo_setting . ProtectedBranchRules )
m . Combo ( "/edit" ) . Get ( repo_setting . SettingsProtectedBranch ) .
Post ( web . Bind ( forms . ProtectBranchForm { } ) , context . RepoMustNotBeArchived ( ) , repo_setting . SettingsProtectedBranchPost )
m . Post ( "/{id}/delete" , repo_setting . DeleteProtectedBranchRulePost )
2019-01-18 01:01:04 +01:00
} , repo . MustBeNotEmpty )
2023-01-16 09:00:22 +01:00
2023-07-02 02:59:32 +02:00
m . Post ( "/rename_branch" , web . Bind ( forms . RenameBranchForm { } ) , context . RepoMustNotBeArchived ( ) , repo_setting . RenameBranchPost )
2017-04-25 09:24:51 +02:00
2021-06-25 16:28:55 +02:00
m . Group ( "/tags" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Get ( "" , repo_setting . ProtectedTags )
m . Post ( "" , web . Bind ( forms . ProtectTagForm { } ) , context . RepoMustNotBeArchived ( ) , repo_setting . NewProtectedTagPost )
m . Post ( "/delete" , context . RepoMustNotBeArchived ( ) , repo_setting . DeleteProtectedTagPost )
m . Get ( "/{id}" , repo_setting . EditProtectedTag )
m . Post ( "/{id}" , web . Bind ( forms . ProtectTagForm { } ) , context . RepoMustNotBeArchived ( ) , repo_setting . EditProtectedTagPost )
2021-06-25 16:28:55 +02:00
} )
2021-02-11 18:34:34 +01:00
m . Group ( "/hooks/git" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Get ( "" , repo_setting . GitHooks )
m . Combo ( "/{name}" ) . Get ( repo_setting . GitHooksEdit ) .
Post ( repo_setting . GitHooksEditPost )
2021-02-11 18:34:34 +01:00
} , context . GitHookService ( ) )
2017-04-25 09:24:51 +02:00
m . Group ( "/hooks" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "" , repo_setting . WebhookList )
m . Post ( "/delete" , repo_setting . WebhookDelete )
m . Get ( "/{type}/new" , repo_setting . WebhookNew )
2024-03-21 14:15:56 +01:00
m . Post ( "/{type}/new" , repo_setting . WebhookCreate )
2022-01-05 22:00:20 +01:00
m . Group ( "/{id}" , func ( ) {
2024-03-21 14:43:43 +01:00
m . Get ( "" , repo_setting . WebhookEdit )
2024-03-21 14:33:59 +01:00
m . Post ( "" , repo_setting . WebhookUpdate )
2024-03-21 14:43:43 +01:00
m . Post ( "/test" , repo_setting . WebhookTest )
m . Post ( "/replay/{uuid}" , repo_setting . WebhookReplay )
2022-01-05 22:00:20 +01:00
} )
2023-04-28 02:08:47 +02:00
} , webhooksEnabled )
2017-04-25 09:24:51 +02:00
m . Group ( "/keys" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Combo ( "" ) . Get ( repo_setting . DeployKeys ) .
Post ( web . Bind ( forms . AddKeyForm { } ) , repo_setting . DeployKeysPost )
m . Post ( "/delete" , repo_setting . DeleteDeployKey )
2023-02-01 13:53:04 +01:00
} )
2019-10-28 19:31:55 +01:00
m . Group ( "/lfs" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Get ( "/" , repo_setting . LFSFiles )
m . Get ( "/show/{oid}" , repo_setting . LFSFileGet )
m . Post ( "/delete/{oid}" , repo_setting . LFSDelete )
m . Get ( "/pointers" , repo_setting . LFSPointerFiles )
m . Post ( "/pointers/associate" , repo_setting . LFSAutoAssociate )
m . Get ( "/find" , repo_setting . LFSFileFind )
2019-12-12 14:18:07 +01:00
m . Group ( "/locks" , func ( ) {
2023-07-02 02:59:32 +02:00
m . Get ( "/" , repo_setting . LFSLocks )
m . Post ( "/" , repo_setting . LFSLockFile )
m . Post ( "/{lid}/unlock" , repo_setting . LFSUnlock )
2019-12-12 14:18:07 +01:00
} )
2019-10-28 19:31:55 +01:00
} )
2023-04-28 02:08:47 +02:00
m . Group ( "/actions" , func ( ) {
m . Get ( "" , repo_setting . RedirectToDefaultSetting )
addSettingsRunnersRoutes ( )
addSettingsSecretsRoutes ( )
2023-12-25 08:28:59 +01:00
addSettingsVariablesRoutes ( )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
} , actions . MustEnableActions )
2023-08-04 04:21:32 +02:00
// the follow handler must be under "settings", otherwise this incomplete repo can't be accessed
m . Group ( "/migrate" , func ( ) {
m . Post ( "/retry" , repo . MigrateRetryPost )
m . Post ( "/cancel" , repo . MigrateCancelPost )
} )
2023-04-28 02:08:47 +02:00
} , ctxDataSet ( "PageIsRepoSettings" , true , "LFSStartServer" , setting . LFS . StartServer ) )
2021-04-10 02:26:08 +02:00
} , reqSignIn , context . RepoAssignment , context . UnitTypes ( ) , reqRepoAdmin , context . RepoRef ( ) )
2017-04-25 09:24:51 +02:00
2024-02-25 22:45:57 +01:00
m . Group ( "/{username}/{reponame}/action" , func ( ) {
m . Post ( "/watch" , repo . ActionWatch ( true ) )
m . Post ( "/unwatch" , repo . ActionWatch ( false ) )
m . Post ( "/accept_transfer" , repo . ActionTransfer ( true ) )
m . Post ( "/reject_transfer" , repo . ActionTransfer ( false ) )
2024-02-26 09:22:51 +01:00
if ! setting . Repository . DisableStars {
m . Post ( "/star" , repo . ActionStar ( true ) )
m . Post ( "/unstar" , repo . ActionStar ( false ) )
}
2024-02-25 22:45:57 +01:00
} , reqSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2017-05-18 16:54:24 +02:00
2023-05-04 14:07:15 +02:00
// Grouping for those endpoints not requiring authentication (but should respect ignSignIn)
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2020-05-03 11:07:04 +02:00
m . Group ( "/milestone" , func ( ) {
2021-01-26 16:36:53 +01:00
m . Get ( "/{id}" , repo . MilestoneIssuesAndPulls )
2020-05-03 11:07:04 +02:00
} , reqRepoIssuesOrPullsReader , context . RepoRef ( ) )
2022-06-09 13:15:08 +02:00
m . Get ( "/find/*" , repo . FindFiles )
m . Group ( "/tree-list" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . TreeList )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . TreeList )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . TreeList )
} )
2021-12-17 23:20:27 +01:00
m . Get ( "/compare" , repo . MustBeNotEmpty , reqRepoCodeReader , repo . SetEditorconfigIfExists , ignSignIn , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . CompareDiff )
2020-05-05 00:44:30 +02:00
m . Combo ( "/compare/*" , repo . MustBeNotEmpty , reqRepoCodeReader , repo . SetEditorconfigIfExists ) .
2023-05-04 14:07:15 +02:00
Get ( repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . CompareDiff ) .
2022-12-12 09:09:26 +01:00
Post ( reqSignIn , context . RepoMustNotBeArchived ( ) , reqRepoPullsReader , repo . MustAllowPulls , web . Bind ( forms . CreateIssueForm { } ) , repo . SetWhitespaceBehavior , repo . CompareAndPullRequestPost )
2022-06-04 22:10:54 +02:00
m . Group ( "/{type:issues|pulls}" , func ( ) {
m . Group ( "/{index}" , func ( ) {
m . Get ( "/info" , repo . GetIssueInfo )
Add a "summary card" to issues & PRs for consumption by OpenGraph clients (#6053)
## Overview
Hi all, I'm a first-time contributor to Forgejo. I was looking for something interesting to contribute and the first thing that caught my attention was https://codeberg.org/forgejo/forgejo/issues/6043, a request for an enhancement to include "issue previews" when publishing links to social media platforms. As a bit of background, the way these platforms work is that they search for meta tags in the posted link's content, and if they find a meta `og:image` (along with other meta tags) they'll pull the image to include in the social media post. Forgejo currently provides an `og:image` tag but it just renders the repository or repository-owner's avatar.
This PR will render `og:image` for an issue or PR into a link to `{...}/summary-card`, which is a dynamically generated image that contains a summary of the issue.
## Design Notes
### Rendering / Rasterization
The tricky part of solving this problem is rendering an image that combines some text, some images, and some layout elements. To address this, I've created a `card` module which allows for a handful of operations:
- Create a new rendered image (a "Card")
- Add a margin to a card
- Split the card, horizontally or vertically, into two pieces with a proportional layout (eg. 70%/30%, as desired), each of which are "Cards" that render into the same root image
- Render text into a card, with line-wrapping and text-alignment capabilities
- Render an image onto a card
- Fetches an external image as safely as possible (for server-side fetch of Gravatar, etc.)
The card module can be reused to create `og:image` summary cards for any object in the future, although obviously it's capabilities are limited. The current implementation is on issues/PRs.
I considered a few alternative approaches before taking this approach, and here's why I rejected those options:
- Provide the summary card as an SVG object which could be rendered much more easily with a template file -- however, support for SVG isn't defined as positive for OpenGraph, and a quick look through some existing implementations suggest that it is not widely supported, if at all
- Rendering as HTML/CSS, or SVG, and then using an external tool to convert into a PNG (or other static) image -- this would be much nicer and easier to implement, but would require tying in some very heavy-weight dependencies
- Rendering using a more sophisticated graphics library, eg. cairo -- also would be nicer and easier to implement, but again a heavy dependency for a small functionality
As a result of the limited capabilities of the new card module, summary cards don't have icons on them (which would require SVG rasterization) or pretty status badges with colors and rounded rects. In the future if better drawing capabilities were added, the graphics could be improved, but it doesn't seem too important.
### External Avatars
In order to rasterize a user's avatar onto the summary card, it might have to be retrieved by the server from the external source (eg. Gravatar). A `fetchExternalImage` routine attempts to do this in the safest way possible to protect the server from any possible security exposure from this; (a) verifying that the content-types are acceptable, (b) ensuring that the file-size and image-size are within the safe bounds that are used for custom avatars, (c) using a very-short timeout to avoid stalling the server if an external dependency is offline.
### Caching
Summary cards are cached after rendered. This has the downside of causing updates to statuses, avatars, titles, etc. being stale on the summary card for the cache TTL. However, during testing I found that some social media engines like Mastodon will cause the summary card to be accessed a significant number of times after being referenced by a post, causing a mini-tornado of requests. The cache compensates for this to avoid server load in this situation.
### Scope
I'm considering out-of-scope:
- Summary cards on other objects (eg. repos, users) can be left for future implementation
## Checklist
The [contributor guide](https://forgejo.org/docs/next/contributor/) contains information that will be helpful to first time contributors. There also are a few [conditions for merging Pull Requests in Forgejo repositories](https://codeberg.org/forgejo/governance/src/branch/main/PullRequestsAgreement.md). You are also welcome to join the [Forgejo development chatroom](https://matrix.to/#/#forgejo-development:matrix.org).
### Tests
- I added test coverage for Go changes...
- [x] in their respective `*_test.go` for unit tests.
- [x] in the `tests/integration` directory if it involves interactions with a live Forgejo server.
- ~~I added test coverage for JavaScript changes...~~ n/a, no JS changes
- [x] ~~in `web_src/js/*.test.js` if it can be unit tested.~~
- [x] ~~in `tests/e2e/*.test.e2e.js` if it requires interactions with a live Forgejo server (see also the [developer guide for JavaScript testing](https://codeberg.org/forgejo/forgejo/src/branch/forgejo/tests/e2e/README.md#end-to-end-tests)).~~
- Manual testing
- [x] Access & attach screenshots of both an issue and a pull-request's summary card; see below
- [x] Ensure reasonable (non-crash) behavior of rendering text with glyphs outside the font -- correctly rendered as replacement unicode chars
- [x] Using a public test instance, verify that og:image behavior looks good on platforms like Mastodon and BlueSky
- [x] Bluesky: ✅
- [x] Mastodon: ✅ (Note that the summary card will be requested many times as the post is federated; either each server, or each client, will fetch it itself)
- [x] OpenGraph test site (https://www.opengraph.xyz/): ✅
- [x] Discord: Looks OK ✅; needs "twitter:card" to be set to "summary_large_image" to display the large-scale image, but (a) that's probably annoying to use, (b) probably wrong because it doesn't match Twitter Card's spec for a "photographic image", and (c) don't want to encourage/continue use of vendor-specific tag
- [x] Verify cases with user avatar missing (or autogen), and repo avatar missing (falls back to repo owner avatar)
Pull request summary card:

Issue summary card:

(images to the right are the custom repo avatar, w/ fallback to the repo owner avatar)
### Documentation
- [ ] I created a pull request [to the documentation](https://codeberg.org/forgejo/docs) to explain to Forgejo users how to use this change.
- [x] I did not document these changes and I do not expect someone else to do it.
- OpenGraph capabilities are expected to work in the background without user awareness, and so there is no need for documentation to explain the capabilities for users.
### Release notes
- [ ] I do not want this change to show in the release notes.
- [x] I want the title to show in the release notes with a link to this pull request.
- [ ] I want the content of the `release-notes/<pull request number>.md` to be be used for the release notes instead of the title.
Reviewed-on: https://codeberg.org/forgejo/forgejo/pulls/6053
Reviewed-by: Gusted <gusted@noreply.codeberg.org>
Co-authored-by: Mathieu Fenniak <mathieu@fenniak.net>
Co-committed-by: Mathieu Fenniak <mathieu@fenniak.net>
2024-11-29 16:02:03 +01:00
m . Get ( "/summary-card" , repo . GetSummaryCard )
2022-06-04 22:10:54 +02:00
} )
} )
2023-05-04 14:07:15 +02:00
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) ) // for "/{username}/{reponame}" which doesn't require authentication
2020-05-03 11:07:04 +02:00
// Grouping for those endpoints that do require authentication
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2024-02-25 11:58:23 +01:00
if ! setting . Repository . DisableForks {
m . Combo ( "/fork" , reqRepoCodeReader ) . Get ( repo . Fork ) .
Post ( web . Bind ( forms . CreateRepoForm { } ) , repo . ForkPost )
}
2017-04-25 09:24:51 +02:00
m . Group ( "/issues" , func ( ) {
2020-09-11 16:48:39 +02:00
m . Group ( "/new" , func ( ) {
m . Combo ( "" ) . Get ( context . RepoRef ( ) , repo . NewIssue ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . CreateIssueForm { } ) , repo . NewIssuePost )
2020-09-11 16:48:39 +02:00
m . Get ( "/choose" , context . RepoRef ( ) , repo . NewIssueChooseTemplate )
} )
2022-04-07 20:59:56 +02:00
m . Get ( "/search" , repo . ListIssues )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) , reqRepoIssueReader )
2021-02-18 15:47:23 +01:00
// FIXME: should use different URLs but mostly same logic for comments of issue and pull request.
2017-10-16 09:55:43 +02:00
// So they can apply their own enable/disable logic on routers.
2021-12-16 20:01:14 +01:00
m . Group ( "/{type:issues|pulls}" , func ( ) {
2021-01-26 16:36:53 +01:00
m . Group ( "/{index}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Post ( "/title" , repo . UpdateIssueTitle )
m . Post ( "/content" , repo . UpdateIssueContent )
2022-12-12 09:09:26 +01:00
m . Post ( "/deadline" , web . Bind ( structs . EditDeadlineOption { } ) , repo . UpdateIssueDeadline )
2017-04-25 09:24:51 +02:00
m . Post ( "/watch" , repo . IssueWatch )
2020-09-08 18:29:51 +02:00
m . Post ( "/ref" , repo . UpdateIssueRef )
2023-05-25 15:17:19 +02:00
m . Post ( "/pin" , reqRepoAdmin , repo . IssuePinOrUnpin )
2022-05-07 20:28:10 +02:00
m . Post ( "/viewed-files" , repo . UpdateViewedFiles )
2018-07-17 23:23:58 +02:00
m . Group ( "/dependency" , func ( ) {
m . Post ( "/add" , repo . AddDependency )
m . Post ( "/delete" , repo . RemoveDependency )
} )
2022-12-12 09:09:26 +01:00
m . Combo ( "/comments" ) . Post ( repo . MustAllowUserComment , web . Bind ( forms . CreateCommentForm { } ) , repo . NewComment )
2017-09-12 08:48:13 +02:00
m . Group ( "/times" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Post ( "/add" , web . Bind ( forms . AddTimeManuallyForm { } ) , repo . AddTimeManually )
2021-02-19 11:52:11 +01:00
m . Post ( "/{timeid}/delete" , repo . DeleteTime )
2017-09-12 08:48:13 +02:00
m . Group ( "/stopwatch" , func ( ) {
m . Post ( "/toggle" , repo . IssueStopwatch )
m . Post ( "/cancel" , repo . CancelStopwatch )
} )
} )
2022-12-12 09:09:26 +01:00
m . Post ( "/reactions/{action}" , web . Bind ( forms . ReactionForm { } ) , repo . ChangeIssueReaction )
2022-12-12 16:02:51 +01:00
m . Post ( "/lock" , reqRepoIssuesOrPullsWriter , web . Bind ( forms . IssueLockForm { } ) , repo . LockIssue )
m . Post ( "/unlock" , reqRepoIssuesOrPullsWriter , repo . UnlockIssue )
2022-03-09 01:38:11 +01:00
m . Post ( "/delete" , reqRepoAdmin , repo . DeleteIssue )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) )
2021-01-26 16:36:53 +01:00
m . Group ( "/{index}" , func ( ) {
2020-10-05 07:49:33 +02:00
m . Get ( "/attachments" , repo . GetIssueAttachments )
2021-01-26 16:36:53 +01:00
m . Get ( "/attachments/{uuid}" , repo . GetAttachment )
2020-10-05 07:49:33 +02:00
} )
2021-10-11 00:40:03 +02:00
m . Group ( "/{index}" , func ( ) {
m . Post ( "/content-history/soft-delete" , repo . SoftDeleteContentHistory )
} )
2017-04-25 09:24:51 +02:00
2018-11-28 12:26:14 +01:00
m . Post ( "/labels" , reqRepoIssuesOrPullsWriter , repo . UpdateIssueLabel )
m . Post ( "/milestone" , reqRepoIssuesOrPullsWriter , repo . UpdateIssueMilestone )
2022-06-30 17:55:08 +02:00
m . Post ( "/projects" , reqRepoIssuesOrPullsWriter , reqRepoProjectsReader , repo . UpdateIssueProject )
2018-11-28 12:26:14 +01:00
m . Post ( "/assignee" , reqRepoIssuesOrPullsWriter , repo . UpdateIssueAssignee )
2020-04-06 18:33:34 +02:00
m . Post ( "/request_review" , reqRepoIssuesOrPullsReader , repo . UpdatePullReviewRequest )
2022-12-12 09:09:26 +01:00
m . Post ( "/dismiss_review" , reqRepoAdmin , web . Bind ( forms . DismissReviewForm { } ) , repo . DismissReview )
2018-11-28 12:26:14 +01:00
m . Post ( "/status" , reqRepoIssuesOrPullsWriter , repo . UpdateIssueStatus )
2023-06-19 09:46:50 +02:00
m . Post ( "/delete" , reqRepoAdmin , repo . BatchDeleteIssues )
2023-06-21 18:08:12 +02:00
m . Post ( "/resolve_conversation" , reqRepoIssuesOrPullsReader , repo . SetShowOutdatedComments , repo . UpdateResolveConversation )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
m . Post ( "/attachments" , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeAssetsAttachmentsIssues , context . QuotaTargetRepo ) , repo . UploadIssueAttachment )
2020-10-05 07:49:33 +02:00
m . Post ( "/attachments/remove" , repo . DeleteAttachment )
2023-05-30 17:26:51 +02:00
m . Delete ( "/unpin/{index}" , reqRepoAdmin , repo . IssueUnpin )
m . Post ( "/move_pin" , reqRepoAdmin , repo . IssuePinMove )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) )
2021-01-26 16:36:53 +01:00
m . Group ( "/comments/{id}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Post ( "" , repo . UpdateCommentContent )
m . Post ( "/delete" , repo . DeleteComment )
2022-12-12 09:09:26 +01:00
m . Post ( "/reactions/{action}" , web . Bind ( forms . ReactionForm { } ) , repo . ChangeCommentReaction )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) )
2021-01-26 16:36:53 +01:00
m . Group ( "/comments/{id}" , func ( ) {
2020-10-05 07:49:33 +02:00
m . Get ( "/attachments" , repo . GetCommentAttachments )
} )
2023-03-24 07:12:23 +01:00
m . Post ( "/markup" , web . Bind ( structs . MarkupOption { } ) , misc . Markup )
2017-04-25 09:24:51 +02:00
m . Group ( "/labels" , func ( ) {
2022-12-12 09:09:26 +01:00
m . Post ( "/new" , web . Bind ( forms . CreateLabelForm { } ) , repo . NewLabel )
m . Post ( "/edit" , web . Bind ( forms . CreateLabelForm { } ) , repo . UpdateLabel )
2017-04-25 09:24:51 +02:00
m . Post ( "/delete" , repo . DeleteLabel )
2022-12-12 09:09:26 +01:00
m . Post ( "/initialize" , web . Bind ( forms . InitializeLabelsForm { } ) , repo . InitializeLabels )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) , reqRepoIssuesOrPullsWriter , context . RepoRef ( ) )
2017-04-25 09:24:51 +02:00
m . Group ( "/milestones" , func ( ) {
m . Combo ( "/new" ) . Get ( repo . NewMilestone ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . CreateMilestoneForm { } ) , repo . NewMilestonePost )
2021-01-26 16:36:53 +01:00
m . Get ( "/{id}/edit" , repo . EditMilestone )
2022-12-12 09:09:26 +01:00
m . Post ( "/{id}/edit" , web . Bind ( forms . CreateMilestoneForm { } ) , repo . EditMilestonePost )
2021-01-26 16:36:53 +01:00
m . Post ( "/{id}/{action}" , repo . ChangeMilestoneStatus )
2017-04-25 09:24:51 +02:00
m . Post ( "/delete" , repo . DeleteMilestone )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) , reqRepoIssuesOrPullsWriter , context . RepoRef ( ) )
2019-12-16 07:20:25 +01:00
m . Group ( "/pull" , func ( ) {
2021-01-26 16:36:53 +01:00
m . Post ( "/{index}/target_branch" , repo . UpdatePullRequestTarget )
2019-12-16 07:20:25 +01:00
} , context . RepoMustNotBeArchived ( ) )
2017-04-25 09:24:51 +02:00
m . Group ( "" , func ( ) {
m . Group ( "" , func ( ) {
2017-10-30 03:04:25 +01:00
m . Combo ( "/_edit/*" ) . Get ( repo . EditFile ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . EditRepoFileForm { } ) , repo . EditFilePost )
2017-10-30 03:04:25 +01:00
m . Combo ( "/_new/*" ) . Get ( repo . NewFile ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . EditRepoFileForm { } ) , repo . NewFilePost )
m . Post ( "/_preview/*" , web . Bind ( forms . EditPreviewDiffForm { } ) , repo . DiffPreviewPost )
2017-10-30 03:04:25 +01:00
m . Combo ( "/_delete/*" ) . Get ( repo . DeleteFile ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . DeleteRepoFileForm { } ) , repo . DeleteFilePost )
2017-10-30 03:04:25 +01:00
m . Combo ( "/_upload/*" , repo . MustBeAbleToUpload ) .
Get ( repo . UploadFile ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . UploadRepoFileForm { } ) , repo . UploadFilePost )
2022-02-09 21:28:55 +01:00
m . Combo ( "/_diffpatch/*" ) . Get ( repo . NewDiffPatch ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . EditRepoFileForm { } ) , repo . NewDiffPatchPost )
2023-11-14 19:24:20 +01:00
m . Combo ( "/_cherrypick/{sha:([a-f0-9]{4,64})}/*" ) . Get ( repo . CherryPick ) .
2022-12-12 09:09:26 +01:00
Post ( web . Bind ( forms . CherryPickForm { } ) , repo . CherryPickPost )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
} , repo . MustBeEditable , repo . CommonEditorData , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeReposAll , context . QuotaTargetRepo ) )
2017-10-30 03:04:25 +01:00
m . Group ( "" , func ( ) {
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
m . Post ( "/upload-file" , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeReposAll , context . QuotaTargetRepo ) , repo . UploadFileToServer )
2022-12-12 09:09:26 +01:00
m . Post ( "/upload-remove" , web . Bind ( forms . RemoveUploadFileForm { } ) , repo . RemoveUploadFileFromServer )
2022-04-28 17:45:33 +02:00
} , repo . MustBeEditable , repo . MustBeAbleToUpload )
2023-04-19 15:40:42 +02:00
} , context . RepoRef ( ) , canEnableEditor , context . RepoMustNotBeArchived ( ) )
2017-10-15 21:59:24 +02:00
m . Group ( "/branches" , func ( ) {
2021-01-26 16:36:53 +01:00
m . Group ( "/_new" , func ( ) {
2017-10-30 03:04:25 +01:00
m . Post ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . CreateBranch )
m . Post ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . CreateBranch )
m . Post ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . CreateBranch )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
} , web . Bind ( forms . NewBranchForm { } ) , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeReposAll , context . QuotaTargetRepo ) )
2017-10-26 02:49:16 +02:00
m . Post ( "/delete" , repo . DeleteBranchPost )
m . Post ( "/restore" , repo . RestoreBranchPost )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) , reqRepoCodeWriter , repo . MustBeNotEmpty )
2021-04-10 02:26:08 +02:00
} , reqSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2017-05-18 16:54:24 +02:00
2023-04-25 18:29:00 +02:00
// Tags
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2022-12-21 22:06:26 +01:00
m . Group ( "/tags" , func ( ) {
m . Get ( "" , repo . TagsList )
2023-07-21 13:20:04 +02:00
m . Get ( "/list" , repo . GetTagList )
2022-12-21 22:06:26 +01:00
m . Get ( ".rss" , feedEnabled , repo . TagsListFeedRSS )
m . Get ( ".atom" , feedEnabled , repo . TagsListFeedAtom )
2023-04-28 02:08:47 +02:00
} , ctxDataSet ( "EnableFeed" , setting . Other . EnableFeed ) ,
repo . MustBeNotEmpty , reqRepoCodeReader , context . RepoRefByType ( context . RepoRefTag , true ) )
2023-04-25 18:29:00 +02:00
m . Post ( "/tags/delete" , repo . DeleteTag , reqSignIn ,
repo . MustBeNotEmpty , context . RepoMustNotBeArchived ( ) , reqRepoCodeWriter , context . RepoRef ( ) )
2023-04-29 06:40:55 +02:00
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2023-04-25 18:29:00 +02:00
// Releases
m . Group ( "/{username}/{reponame}" , func ( ) {
2017-05-18 16:54:24 +02:00
m . Group ( "/releases" , func ( ) {
2020-04-18 16:47:15 +02:00
m . Get ( "/" , repo . Releases )
2020-09-17 20:24:23 +02:00
m . Get ( "/tag/*" , repo . SingleRelease )
2020-04-18 16:47:15 +02:00
m . Get ( "/latest" , repo . LatestRelease )
2022-12-21 22:06:26 +01:00
m . Get ( ".rss" , feedEnabled , repo . ReleasesFeedRSS )
m . Get ( ".atom" , feedEnabled , repo . ReleasesFeedAtom )
2023-04-28 02:08:47 +02:00
} , ctxDataSet ( "EnableFeed" , setting . Other . EnableFeed ) ,
2023-10-01 12:41:52 +02:00
repo . MustBeNotEmpty , context . RepoRefByType ( context . RepoRefTag , true ) )
m . Get ( "/releases/attachments/{uuid}" , repo . MustBeNotEmpty , repo . GetAttachment )
m . Get ( "/releases/download/{vTag}/{fileName}" , repo . MustBeNotEmpty , repo . RedirectDownload )
2017-06-18 05:38:24 +02:00
m . Group ( "/releases" , func ( ) {
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
m . Combo ( "/new" , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeReposAll , context . QuotaTargetRepo ) ) .
Get ( repo . NewRelease ) .
Post ( web . Bind ( forms . NewReleaseForm { } ) , repo . NewReleasePost )
2017-05-18 16:54:24 +02:00
m . Post ( "/delete" , repo . DeleteRelease )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
m . Post ( "/attachments" , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeAssetsAttachmentsReleases , context . QuotaTargetRepo ) , repo . UploadReleaseAttachment )
2020-10-05 07:49:33 +02:00
m . Post ( "/attachments/remove" , repo . DeleteAttachment )
2019-01-23 19:58:38 +01:00
} , reqSignIn , repo . MustBeNotEmpty , context . RepoMustNotBeArchived ( ) , reqRepoReleaseWriter , context . RepoRef ( ) )
2017-05-18 16:54:24 +02:00
m . Group ( "/releases" , func ( ) {
m . Get ( "/edit/*" , repo . EditRelease )
2022-12-12 09:09:26 +01:00
m . Post ( "/edit/*" , web . Bind ( forms . EditReleaseForm { } ) , repo . EditReleasePost )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
} , reqSignIn , repo . MustBeNotEmpty , context . RepoMustNotBeArchived ( ) , reqRepoReleaseWriter , repo . CommitInfoCache , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeReposAll , context . QuotaTargetRepo ) )
2021-04-10 02:26:08 +02:00
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) , reqRepoReleaseReader )
2017-04-25 09:24:51 +02:00
2021-07-23 20:08:04 +02:00
// to maintain compatibility with old attachments
m . Group ( "/{username}/{reponame}" , func ( ) {
m . Get ( "/attachments/{uuid}" , repo . GetAttachment )
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2018-06-21 11:09:46 +02:00
m . Post ( "/topics" , repo . TopicsPost )
2021-04-10 02:26:08 +02:00
} , context . RepoAssignment , context . RepoMustNotBeArchived ( ) , reqRepoAdmin )
2018-04-11 04:51:44 +02:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Group ( "" , func ( ) {
2023-07-20 14:41:28 +02:00
m . Get ( "/issues/posters" , repo . IssuePosters ) // it can't use {type:issues|pulls} because other routes like "/pulls/{index}" has higher priority
m . Get ( "/{type:issues|pulls}" , repo . Issues )
2021-01-26 16:36:53 +01:00
m . Get ( "/{type:issues|pulls}/{index}" , repo . ViewIssue )
2021-10-11 00:40:03 +02:00
m . Group ( "/{type:issues|pulls}/{index}/content-history" , func ( ) {
m . Get ( "/overview" , repo . GetContentHistoryOverview )
m . Get ( "/list" , repo . GetContentHistoryList )
m . Get ( "/detail" , repo . GetContentHistoryDetail )
} )
2021-01-26 16:36:53 +01:00
m . Get ( "/labels" , reqRepoIssuesOrPullsReader , repo . RetrieveLabels , repo . Labels )
2018-11-28 12:26:14 +01:00
m . Get ( "/milestones" , reqRepoIssuesOrPullsReader , repo . Milestones )
2017-06-03 07:56:36 +02:00
} , context . RepoRef ( ) )
2017-04-25 09:24:51 +02:00
2022-03-31 19:31:53 +02:00
if setting . Packages . Enabled {
m . Get ( "/packages" , repo . Packages )
}
2022-03-30 10:42:47 +02:00
[GITEA] Add support for shields.io-based badges
Adds a new `/{username}/{repo}/badges` family of routes, which redirect
to various shields.io badges. The goal is to not reimplement badge
generation, and delegate it to shields.io (or a similar service), which
are already used by many. This way, we get all the goodies that come
with it: different styles, colors, logos, you name it.
So these routes are just thin wrappers around shields.io that make it
easier to display the information we want. The URL is configurable via
`app.ini`, and is templatable, allowing to use alternative badge
generator services with slightly different URL patterns.
Additionally, for compatibility with GitHub, there's an
`/{username}/{repo}/actions/workflows/{workflow_file}/badge.svg` route
that works much the same way as on GitHub. Change the hostname in the
URL, and done.
Fixes gitea#5633, gitea#23688, and also fixes #126.
Work sponsored by Codeberg e.V.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit fcd0f61212d8febd4bdfc27e61a4e13cbdd16d49)
(cherry picked from commit 20d14f784490a880c51ca0f0a6a5988a01887635)
(cherry picked from commit 4359741431bb39de4cf24de8b0cfb513f5233f55)
(cherry picked from commit 35cff45eb86177e750cd22e82a201880a5efe045)
(cherry picked from commit 2fc0d0b8a302d24177a00ab48b42ce083b52e506)
2024-01-01 13:38:49 +01:00
if setting . Badges . Enabled {
m . Group ( "/badges" , func ( ) {
m . Get ( "/workflows/{workflow_name}/badge.svg" , badges . GetWorkflowBadge )
m . Group ( "/issues" , func ( ) {
m . Get ( ".svg" , badges . GetTotalIssuesBadge )
m . Get ( "/open.svg" , badges . GetOpenIssuesBadge )
m . Get ( "/closed.svg" , badges . GetClosedIssuesBadge )
} )
m . Group ( "/pulls" , func ( ) {
m . Get ( ".svg" , badges . GetTotalPullsBadge )
m . Get ( "/open.svg" , badges . GetOpenPullsBadge )
m . Get ( "/closed.svg" , badges . GetClosedPullsBadge )
} )
2024-02-26 09:22:51 +01:00
if ! setting . Repository . DisableStars {
m . Get ( "/stars.svg" , badges . GetStarsBadge )
}
[GITEA] Add support for shields.io-based badges
Adds a new `/{username}/{repo}/badges` family of routes, which redirect
to various shields.io badges. The goal is to not reimplement badge
generation, and delegate it to shields.io (or a similar service), which
are already used by many. This way, we get all the goodies that come
with it: different styles, colors, logos, you name it.
So these routes are just thin wrappers around shields.io that make it
easier to display the information we want. The URL is configurable via
`app.ini`, and is templatable, allowing to use alternative badge
generator services with slightly different URL patterns.
Additionally, for compatibility with GitHub, there's an
`/{username}/{repo}/actions/workflows/{workflow_file}/badge.svg` route
that works much the same way as on GitHub. Change the hostname in the
URL, and done.
Fixes gitea#5633, gitea#23688, and also fixes #126.
Work sponsored by Codeberg e.V.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit fcd0f61212d8febd4bdfc27e61a4e13cbdd16d49)
(cherry picked from commit 20d14f784490a880c51ca0f0a6a5988a01887635)
(cherry picked from commit 4359741431bb39de4cf24de8b0cfb513f5233f55)
(cherry picked from commit 35cff45eb86177e750cd22e82a201880a5efe045)
(cherry picked from commit 2fc0d0b8a302d24177a00ab48b42ce083b52e506)
2024-01-01 13:38:49 +01:00
m . Get ( "/release.svg" , badges . GetLatestReleaseBadge )
} )
}
2020-08-17 05:07:38 +02:00
m . Group ( "/projects" , func ( ) {
m . Get ( "" , repo . Projects )
2021-01-26 16:36:53 +01:00
m . Get ( "/{id}" , repo . ViewProject )
2023-01-20 12:42:33 +01:00
m . Group ( "" , func ( ) { //nolint:dupl
2023-05-31 08:50:18 +02:00
m . Get ( "/new" , repo . RenderNewProject )
2022-12-12 09:09:26 +01:00
m . Post ( "/new" , web . Bind ( forms . CreateProjectForm { } ) , repo . NewProjectPost )
2021-01-26 16:36:53 +01:00
m . Group ( "/{id}" , func ( ) {
2024-05-27 10:59:54 +02:00
m . Post ( "" , web . Bind ( forms . EditProjectColumnForm { } ) , repo . AddColumnToProjectPost )
2024-05-08 15:44:57 +02:00
m . Post ( "/move" , project . MoveColumns )
2020-08-22 08:58:59 +02:00
m . Post ( "/delete" , repo . DeleteProject )
2023-05-31 08:50:18 +02:00
m . Get ( "/edit" , repo . RenderEditProject )
2022-12-12 09:09:26 +01:00
m . Post ( "/edit" , web . Bind ( forms . CreateProjectForm { } ) , repo . EditProjectPost )
2021-01-26 16:36:53 +01:00
m . Post ( "/{action:open|close}" , repo . ChangeProjectStatus )
2020-08-22 08:58:59 +02:00
2024-05-27 10:59:54 +02:00
m . Group ( "/{columnID}" , func ( ) {
m . Put ( "" , web . Bind ( forms . EditProjectColumnForm { } ) , repo . EditProjectColumn )
m . Delete ( "" , repo . DeleteProjectColumn )
m . Post ( "/default" , repo . SetDefaultProjectColumn )
2020-08-22 08:58:59 +02:00
2021-12-08 07:57:18 +01:00
m . Post ( "/move" , repo . MoveIssues )
2020-08-22 08:58:59 +02:00
} )
2020-08-17 05:07:38 +02:00
} )
2020-08-22 08:58:59 +02:00
} , reqRepoProjectsWriter , context . RepoMustNotBeArchived ( ) )
2020-08-17 05:07:38 +02:00
} , reqRepoProjectsReader , repo . MustEnableProjects )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
m . Group ( "/actions" , func ( ) {
m . Get ( "" , actions . List )
2023-08-14 17:14:30 +02:00
m . Post ( "/disable" , reqRepoAdmin , actions . DisableWorkflowFile )
m . Post ( "/enable" , reqRepoAdmin , actions . EnableWorkflowFile )
2024-06-28 07:17:11 +02:00
m . Post ( "/manual" , reqRepoAdmin , actions . ManualRunWorkflow )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
2023-12-08 13:41:48 +01:00
m . Group ( "/runs" , func ( ) {
m . Get ( "/latest" , actions . ViewLatest )
m . Group ( "/{run}" , func ( ) {
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
m . Combo ( "" ) .
Get ( actions . View ) .
Post ( web . Bind ( actions . ViewRequest { } ) , actions . ViewPost )
2023-12-08 13:41:48 +01:00
m . Group ( "/jobs/{job}" , func ( ) {
m . Combo ( "" ) .
Get ( actions . View ) .
Post ( web . Bind ( actions . ViewRequest { } ) , actions . ViewPost )
m . Post ( "/rerun" , reqRepoActionsWriter , actions . Rerun )
m . Get ( "/logs" , actions . Logs )
} )
m . Post ( "/cancel" , reqRepoActionsWriter , actions . Cancel )
m . Post ( "/approve" , reqRepoActionsWriter , actions . Approve )
2024-03-12 11:53:53 +01:00
m . Get ( "/artifacts" , actions . ArtifactsView )
2023-12-08 13:41:48 +01:00
m . Get ( "/artifacts/{artifact_name}" , actions . ArtifactsDownloadView )
2024-02-25 10:52:11 +01:00
m . Delete ( "/artifacts/{artifact_name}" , reqRepoActionsWriter , actions . ArtifactsDeleteView )
2023-08-22 04:30:02 +02:00
m . Post ( "/rerun" , reqRepoActionsWriter , actions . Rerun )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
} )
} )
[GITEA] Add support for shields.io-based badges
Adds a new `/{username}/{repo}/badges` family of routes, which redirect
to various shields.io badges. The goal is to not reimplement badge
generation, and delegate it to shields.io (or a similar service), which
are already used by many. This way, we get all the goodies that come
with it: different styles, colors, logos, you name it.
So these routes are just thin wrappers around shields.io that make it
easier to display the information we want. The URL is configurable via
`app.ini`, and is templatable, allowing to use alternative badge
generator services with slightly different URL patterns.
Additionally, for compatibility with GitHub, there's an
`/{username}/{repo}/actions/workflows/{workflow_file}/badge.svg` route
that works much the same way as on GitHub. Change the hostname in the
URL, and done.
Fixes gitea#5633, gitea#23688, and also fixes #126.
Work sponsored by Codeberg e.V.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit fcd0f61212d8febd4bdfc27e61a4e13cbdd16d49)
(cherry picked from commit 20d14f784490a880c51ca0f0a6a5988a01887635)
(cherry picked from commit 4359741431bb39de4cf24de8b0cfb513f5233f55)
(cherry picked from commit 35cff45eb86177e750cd22e82a201880a5efe045)
(cherry picked from commit 2fc0d0b8a302d24177a00ab48b42ce083b52e506)
2024-01-01 13:38:49 +01:00
2024-02-06 00:53:08 +01:00
m . Group ( "/workflows/{workflow_name}" , func ( ) {
m . Get ( "/badge.svg" , badges . GetWorkflowBadge )
m . Get ( "/runs/latest" , actions . ViewLatestWorkflowRun )
} )
Implement actions (#21937)
Close #13539.
Co-authored by: @lunny @appleboy @fuxiaohei and others.
Related projects:
- https://gitea.com/gitea/actions-proto-def
- https://gitea.com/gitea/actions-proto-go
- https://gitea.com/gitea/act
- https://gitea.com/gitea/act_runner
### Summary
The target of this PR is to bring a basic implementation of "Actions",
an internal CI/CD system of Gitea. That means even though it has been
merged, the state of the feature is **EXPERIMENTAL**, and please note
that:
- It is disabled by default;
- It shouldn't be used in a production environment currently;
- It shouldn't be used in a public Gitea instance currently;
- Breaking changes may be made before it's stable.
**Please comment on #13539 if you have any different product design
ideas**, all decisions reached there will be adopted here. But in this
PR, we don't talk about **naming, feature-creep or alternatives**.
### ⚠️ Breaking
`gitea-actions` will become a reserved user name. If a user with the
name already exists in the database, it is recommended to rename it.
### Some important reviews
- What is `DEFAULT_ACTIONS_URL` in `app.ini` for?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1055954954
- Why the api for runners is not under the normal `/api/v1` prefix?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061173592
- Why DBFS?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1061301178
- Why ignore events triggered by `gitea-actions` bot?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1063254103
- Why there's no permission control for actions?
- https://github.com/go-gitea/gitea/pull/21937#discussion_r1090229868
### What it looks like
<details>
#### Manage runners
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205870657-c72f590e-2e08-4cd4-be7f-2e0abb299bbf.png">
#### List runs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872794-50fde990-2b45-48c1-a178-908e4ec5b627.png">
#### View logs
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205872501-9b7b9000-9542-4991-8f55-18ccdada77c3.png">
</details>
### How to try it
<details>
#### 1. Start Gitea
Clone this branch and [install from
source](https://docs.gitea.io/en-us/install-from-source).
Add additional configurations in `app.ini` to enable Actions:
```ini
[actions]
ENABLED = true
```
Start it.
If all is well, you'll see the management page of runners:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205877365-8e30a780-9b10-4154-b3e8-ee6c3cb35a59.png">
#### 2. Start runner
Clone the [act_runner](https://gitea.com/gitea/act_runner), and follow
the
[README](https://gitea.com/gitea/act_runner/src/branch/main/README.md)
to start it.
If all is well, you'll see a new runner has been added:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205878000-216f5937-e696-470d-b66c-8473987d91c3.png">
#### 3. Enable actions for a repo
Create a new repo or open an existing one, check the `Actions` checkbox
in settings and submit.
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879705-53e09208-73c0-4b3e-a123-2dcf9aba4b9c.png">
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205879383-23f3d08f-1a85-41dd-a8b3-54e2ee6453e8.png">
If all is well, you'll see a new tab "Actions":
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205881648-a8072d8c-5803-4d76-b8a8-9b2fb49516c1.png">
#### 4. Upload workflow files
Upload some workflow files to `.gitea/workflows/xxx.yaml`, you can
follow the [quickstart](https://docs.github.com/en/actions/quickstart)
of GitHub Actions. Yes, Gitea Actions is compatible with GitHub Actions
in most cases, you can use the same demo:
```yaml
name: GitHub Actions Demo
run-name: ${{ github.actor }} is testing out GitHub Actions 🚀
on: [push]
jobs:
Explore-GitHub-Actions:
runs-on: ubuntu-latest
steps:
- run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
- run: echo "🐧 This job is now running on a ${{ runner.os }} server hosted by GitHub!"
- run: echo "🔎 The name of your branch is ${{ github.ref }} and your repository is ${{ github.repository }}."
- name: Check out repository code
uses: actions/checkout@v3
- run: echo "💡 The ${{ github.repository }} repository has been cloned to the runner."
- run: echo "🖥️ The workflow is now ready to test your code on the runner."
- name: List files in the repository
run: |
ls ${{ github.workspace }}
- run: echo "🍏 This job's status is ${{ job.status }}."
```
If all is well, you'll see a new run in `Actions` tab:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884473-79a874bc-171b-4aaf-acd5-0241a45c3b53.png">
#### 5. Check the logs of jobs
Click a run and you'll see the logs:
<img width="1792" alt="image"
src="https://user-images.githubusercontent.com/9418365/205884800-994b0374-67f7-48ff-be9a-4c53f3141547.png">
#### 6. Go on
You can try more examples in [the
documents](https://docs.github.com/en/actions/using-workflows/workflow-syntax-for-github-actions)
of GitHub Actions, then you might find a lot of bugs.
Come on, PRs are welcome.
</details>
See also: [Feature Preview: Gitea
Actions](https://blog.gitea.io/2022/12/feature-preview-gitea-actions/)
---------
Co-authored-by: a1012112796 <1012112796@qq.com>
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: ChristopherHX <christopher.homberger@web.de>
Co-authored-by: John Olheiser <john.olheiser@gmail.com>
2023-01-31 02:45:19 +01:00
} , reqRepoActionsReader , actions . MustEnableActions )
2017-04-25 09:24:51 +02:00
m . Group ( "/wiki" , func ( ) {
2021-11-16 19:18:25 +01:00
m . Combo ( "/" ) .
Get ( repo . Wiki ) .
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
Post ( context . RepoMustNotBeArchived ( ) , reqSignIn , reqRepoWikiWriter , web . Bind ( forms . NewWikiForm { } ) , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeWiki , context . QuotaTargetRepo ) , repo . WikiPost )
2021-11-16 19:18:25 +01:00
m . Combo ( "/*" ) .
Get ( repo . Wiki ) .
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
Post ( context . RepoMustNotBeArchived ( ) , reqSignIn , reqRepoWikiWriter , web . Bind ( forms . NewWikiForm { } ) , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeWiki , context . QuotaTargetRepo ) , repo . WikiPost )
2023-11-14 19:24:20 +01:00
m . Get ( "/commit/{sha:[a-f0-9]{4,64}}" , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . Diff )
m . Get ( "/commit/{sha:[a-f0-9]{4,64}}.{ext:patch|diff}" , repo . RawDiff )
2021-11-16 19:18:25 +01:00
} , repo . MustEnableWiki , func ( ctx * context . Context ) {
2020-05-16 18:38:40 +02:00
ctx . Data [ "PageIsWiki" ] = true
2022-03-29 05:21:30 +02:00
ctx . Data [ "CloneButtonOriginLink" ] = ctx . Repo . Repository . WikiCloneLink ( )
2020-05-16 18:38:40 +02:00
} )
2017-04-25 09:24:51 +02:00
m . Group ( "/wiki" , func ( ) {
2024-05-20 14:23:27 +02:00
m . Get ( "/search" , repo . WikiSearchContent )
2017-04-25 09:24:51 +02:00
m . Get ( "/raw/*" , repo . WikiRaw )
2017-09-30 06:04:16 +02:00
} , repo . MustEnableWiki )
2017-04-25 09:24:51 +02:00
2017-10-15 01:17:39 +02:00
m . Group ( "/activity" , func ( ) {
m . Get ( "" , repo . Activity )
2021-01-26 16:36:53 +01:00
m . Get ( "/{period}" , repo . Activity )
2024-02-15 23:21:13 +01:00
m . Group ( "/contributors" , func ( ) {
m . Get ( "" , repo . Contributors )
m . Get ( "/data" , repo . ContributorsData )
2024-04-28 15:47:52 +02:00
} , repo . MustBeNotEmpty , context . RequireRepoReaderOr ( unit . TypeCode ) )
2024-02-24 00:41:24 +01:00
m . Group ( "/code-frequency" , func ( ) {
m . Get ( "" , repo . CodeFrequency )
m . Get ( "/data" , repo . CodeFrequencyData )
2024-04-28 15:47:52 +02:00
} , repo . MustBeNotEmpty , context . RequireRepoReaderOr ( unit . TypeCode ) )
2024-02-24 11:22:51 +01:00
m . Group ( "/recent-commits" , func ( ) {
m . Get ( "" , repo . RecentCommits )
m . Get ( "/data" , repo . RecentCommitsData )
2024-04-28 15:47:52 +02:00
} , repo . MustBeNotEmpty , context . RequireRepoReaderOr ( unit . TypeCode ) )
} , context . RepoRef ( ) , context . RequireRepoReaderOr ( unit . TypeCode , unit . TypePullRequests , unit . TypeIssues , unit . TypeReleases ) )
2017-10-15 01:17:39 +02:00
2019-05-04 14:39:03 +02:00
m . Group ( "/activity_author_data" , func ( ) {
m . Get ( "" , repo . ActivityAuthors )
2021-01-26 16:36:53 +01:00
m . Get ( "/{period}" , repo . ActivityAuthors )
2021-11-09 20:57:58 +01:00
} , context . RepoRef ( ) , repo . MustBeNotEmpty , context . RequireRepoReaderOr ( unit . TypeCode ) )
2019-05-04 14:39:03 +02:00
[RFC] Make archival asynchronous (#11296)
* Make archival asynchronous
The prime benefit being sought here is for large archives to not
clog up the rendering process and cause unsightly proxy timeouts.
As a secondary benefit, archive-in-progress is moved out of the
way into a /tmp file so that new archival requests for the same
commit will not get fulfilled based on an archive that isn't yet
finished.
This asynchronous system is fairly primitive; request comes in, we'll
spawn off a new goroutine to handle it, then we'll mark it as done.
Status requests will see if the file exists in the final location,
and report the archival as done when it exists.
Fixes #11265
* Archive links: drop initial delay to three-quarters of a second
Some, or perhaps even most, archives will not take all that long to archive.
The archive process starts as soon as the download button is initially
clicked, so in theory they could be done quite quickly. Drop the initial
delay down to three-quarters of a second to make it more responsive in the
common case of the archive being quickly created.
* archiver: restructure a little bit to facilitate testing
This introduces two sync.Cond pointers to the archiver package. If they're
non-nil when we go to process a request, we'll wait until signalled (at all)
to proceed. The tests will then create the sync.Cond so that it can signal
at-will and sanity-check the state of the queue at different phases.
The author believes that nil-checking these two sync.Cond pointers on every
archive processing will introduce minimal overhead with no impact on
maintainability.
* gofmt nit: no space around binary + operator
* services: archiver: appease golangci-lint, lock queueMutex
Locking/unlocking the queueMutex is allowed, but not required, for
Cond.Signal() and Cond.Broadcast(). The magic at play here is just a little
too much for golangci-lint, as we take the address of queueMutex and this is
mostly used in archiver.go; the variable still gets flagged as unused.
* archiver: tests: fix several timing nits
Once we've signaled a cond var, it may take some small amount of time for
the goroutines released to hit the spot we're wanting them to be at. Give
them an appropriate amount of time.
* archiver: tests: no underscore in var name, ungh
* archiver: tests: Test* is run in a separate context than TestMain
We must setup the mutex/cond variables at the beginning of any test that's
going to use it, or else these will be nil when the test is actually ran.
* archiver: tests: hopefully final tweak
Things got shuffled around such that we carefully build up and release
requests from the queue, so we can validate the state of the queue at each
step. Fix some assertions that no longer hold true as fallout.
* repo: Download: restore some semblance of previous behavior
When archival was made async, the GET endpoint was only useful if a previous
POST had initiated the download. This commit restores the previous behavior,
to an extent; we'll now submit the archive request there and return a
"202 Accepted" to indicate that it's processing if we didn't manage to
complete the request within ~2 seconds of submission.
This lets a client directly GET the archive, and gives them some indication
that they may attempt to GET it again at a later time.
* archiver: tests: simplify a bit further
We don't need to risk failure and use time.ParseDuration to get 2 *
time.Second.
else if isn't really necessary if the conditions are simple enough and lead
to the same result.
* archiver: tests: resolve potential source of flakiness
Increase all timeouts to 10 seconds; these aren't hard-coded sleeps, so
there's no guarantee we'll actually take that long. If we need longer to
not have a false-positive, then so be it.
While here, various assert.{Not,}Equal arguments are flipped around so that
the wording in error output reflects reality, where the expected argument is
second and actual third.
* archiver: setup infrastructure for notifying consumers of completion
This API will *not* allow consumers to subscribe to specific requests being
completed, just *any* request being completed. The caller is responsible for
determining if their request is satisfied and waiting again if needed.
* repo: archive: make GET endpoint synchronous again
If the request isn't complete, this endpoint will now submit the request and
wait for completion using the new API. This may still be susceptible to
timeouts for larger repos, but other endpoints now exist that the web
interface will use to negotiate its way through larger archive processes.
* archiver: tests: amend test to include WaitForCompletion()
This is a trivial one, so go ahead and include it.
* archiver: tests: fix test by calling NewContext()
The mutex is otherwise uninitialized, so we need to ensure that we're
actually initializing it if we plan to test it.
* archiver: tests: integrate new WaitForCompletion a little better
We can use this to wait for archives to come in, rather than spinning and
hoping with a timeout.
* archiver: tests: combine numQueued declaration with next-instruction assignment
* routers: repo: reap unused archiving flag from DownloadStatus()
This had some planned usage before, indicating whether this request
initiated the archival process or not. After several rounds of refactoring,
this use was deemed not necessary for much of anything and got boiled down
to !complete in all cases.
* services: archiver: restructure to use a channel
We now offer two forms of waiting for a request:
- WaitForCompletion: wait for completion with no timeout
- TimedWaitForCompletion: wait for completion with timeout
In both cases, we wait for the given request's cchan to close; in the latter
case, we do so with the caller-provided timeout. This completely removes the
need for busy-wait loops in Download/InitiateDownload, as it's fairly clean
to wait on a channel with timeout.
* services: archiver: use defer to unlock now that we can
This previously carried the lock into the goroutine, but an intermediate
step just added the request to archiveInProgress outside of the new
goroutine and removed the need for the goroutine to start out with it.
* Revert "archiver: tests: combine numQueued declaration with next-instruction assignment"
This reverts commit bcc52140238e16680f2e05e448e9be51372afdf5.
Revert "archiver: tests: integrate new WaitForCompletion a little better"
This reverts commit 9fc8bedb5667d24d3a3c7843dc28a229efffb1e6.
Revert "archiver: tests: fix test by calling NewContext()"
This reverts commit 709c35685eaaf261ebbb7d3420e3376a4ee8e7f2.
Revert "archiver: tests: amend test to include WaitForCompletion()"
This reverts commit 75261f56bc05d1fa8ff7e81dcbc0ccd93fdc9d50.
* archiver: tests: first attempt at WaitForCompletion() tests
* archiver: tests: slight improvement, less busy-loop
Just wait for the requests to complete in order, instead of busy-waiting
with a timeout. This is slightly less fragile.
While here, reverse the arguments of a nearby assert.Equal() so that
expected/actual are correct in any test output.
* archiver: address lint nits
* services: archiver: only close the channel once
* services: archiver: use a struct{} for the wait channel
This makes it obvious that the channel is only being used as a signal,
rather than anything useful being piped through it.
* archiver: tests: fix expectations
Move the close of the channel into doArchive() itself; notably, before these
goroutines move on to waiting on the Release cond.
The tests are adjusted to reflect that we can't WaitForCompletion() after
they've already completed, as WaitForCompletion() doesn't indicate that
they've been released from the queue yet.
* archiver: tests: set cchan to nil for comparison
* archiver: move ctx.Error's back into the route handlers
We shouldn't be setting this in a service, we should just be validating the
request that we were handed.
* services: archiver: use regex to match a hash
This makes sure we don't try and use refName as a hash when it's clearly not
one, e.g. heads/pull/foo.
* routers: repo: remove the weird /archive/status endpoint
We don't need to do this anymore, we can just continue POSTing to the
archive/* endpoint until we're told the download's complete. This avoids a
potential naming conflict, where a ref could start with "status/"
* archiver: tests: bump reasonable timeout to 15s
* archiver: tests: actually release timedReq
* archiver: tests: run through inFlight instead of manually checking
While we're here, add a test for manually re-processing an archive that's
already been complete. Re-open the channel and mark it incomplete, so that
doArchive can just mark it complete again.
* initArchiveLinks: prevent default behavior from clicking
* archiver: alias gitea's context, golang context import pending
* archiver: simplify logic, just reconstruct slices
While the previous logic was perhaps slightly more efficient, the
new variant's readability is much improved.
* archiver: don't block shutdown on waiting for archive
The technique established launches a goroutine to do the wait,
which will close a wait channel upon termination. For the timeout
case, we also send back a value indicating whether the timeout was
hit or not.
The timeouts are expected to be relatively small, but still a multi-
second delay to shutdown due to this could be unfortunate.
* archiver: simplify shutdown logic
We can just grab the shutdown channel from the graceful manager instead of
constructing a channel to halt the caller and/or pass a result back.
* Style issues
* Fix mis-merge
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: Lauris BH <lauris@nix.lv>
2020-11-07 21:27:28 +01:00
m . Group ( "/archive" , func ( ) {
2021-06-23 23:12:38 +02:00
m . Get ( "/*" , repo . Download )
[RFC] Make archival asynchronous (#11296)
* Make archival asynchronous
The prime benefit being sought here is for large archives to not
clog up the rendering process and cause unsightly proxy timeouts.
As a secondary benefit, archive-in-progress is moved out of the
way into a /tmp file so that new archival requests for the same
commit will not get fulfilled based on an archive that isn't yet
finished.
This asynchronous system is fairly primitive; request comes in, we'll
spawn off a new goroutine to handle it, then we'll mark it as done.
Status requests will see if the file exists in the final location,
and report the archival as done when it exists.
Fixes #11265
* Archive links: drop initial delay to three-quarters of a second
Some, or perhaps even most, archives will not take all that long to archive.
The archive process starts as soon as the download button is initially
clicked, so in theory they could be done quite quickly. Drop the initial
delay down to three-quarters of a second to make it more responsive in the
common case of the archive being quickly created.
* archiver: restructure a little bit to facilitate testing
This introduces two sync.Cond pointers to the archiver package. If they're
non-nil when we go to process a request, we'll wait until signalled (at all)
to proceed. The tests will then create the sync.Cond so that it can signal
at-will and sanity-check the state of the queue at different phases.
The author believes that nil-checking these two sync.Cond pointers on every
archive processing will introduce minimal overhead with no impact on
maintainability.
* gofmt nit: no space around binary + operator
* services: archiver: appease golangci-lint, lock queueMutex
Locking/unlocking the queueMutex is allowed, but not required, for
Cond.Signal() and Cond.Broadcast(). The magic at play here is just a little
too much for golangci-lint, as we take the address of queueMutex and this is
mostly used in archiver.go; the variable still gets flagged as unused.
* archiver: tests: fix several timing nits
Once we've signaled a cond var, it may take some small amount of time for
the goroutines released to hit the spot we're wanting them to be at. Give
them an appropriate amount of time.
* archiver: tests: no underscore in var name, ungh
* archiver: tests: Test* is run in a separate context than TestMain
We must setup the mutex/cond variables at the beginning of any test that's
going to use it, or else these will be nil when the test is actually ran.
* archiver: tests: hopefully final tweak
Things got shuffled around such that we carefully build up and release
requests from the queue, so we can validate the state of the queue at each
step. Fix some assertions that no longer hold true as fallout.
* repo: Download: restore some semblance of previous behavior
When archival was made async, the GET endpoint was only useful if a previous
POST had initiated the download. This commit restores the previous behavior,
to an extent; we'll now submit the archive request there and return a
"202 Accepted" to indicate that it's processing if we didn't manage to
complete the request within ~2 seconds of submission.
This lets a client directly GET the archive, and gives them some indication
that they may attempt to GET it again at a later time.
* archiver: tests: simplify a bit further
We don't need to risk failure and use time.ParseDuration to get 2 *
time.Second.
else if isn't really necessary if the conditions are simple enough and lead
to the same result.
* archiver: tests: resolve potential source of flakiness
Increase all timeouts to 10 seconds; these aren't hard-coded sleeps, so
there's no guarantee we'll actually take that long. If we need longer to
not have a false-positive, then so be it.
While here, various assert.{Not,}Equal arguments are flipped around so that
the wording in error output reflects reality, where the expected argument is
second and actual third.
* archiver: setup infrastructure for notifying consumers of completion
This API will *not* allow consumers to subscribe to specific requests being
completed, just *any* request being completed. The caller is responsible for
determining if their request is satisfied and waiting again if needed.
* repo: archive: make GET endpoint synchronous again
If the request isn't complete, this endpoint will now submit the request and
wait for completion using the new API. This may still be susceptible to
timeouts for larger repos, but other endpoints now exist that the web
interface will use to negotiate its way through larger archive processes.
* archiver: tests: amend test to include WaitForCompletion()
This is a trivial one, so go ahead and include it.
* archiver: tests: fix test by calling NewContext()
The mutex is otherwise uninitialized, so we need to ensure that we're
actually initializing it if we plan to test it.
* archiver: tests: integrate new WaitForCompletion a little better
We can use this to wait for archives to come in, rather than spinning and
hoping with a timeout.
* archiver: tests: combine numQueued declaration with next-instruction assignment
* routers: repo: reap unused archiving flag from DownloadStatus()
This had some planned usage before, indicating whether this request
initiated the archival process or not. After several rounds of refactoring,
this use was deemed not necessary for much of anything and got boiled down
to !complete in all cases.
* services: archiver: restructure to use a channel
We now offer two forms of waiting for a request:
- WaitForCompletion: wait for completion with no timeout
- TimedWaitForCompletion: wait for completion with timeout
In both cases, we wait for the given request's cchan to close; in the latter
case, we do so with the caller-provided timeout. This completely removes the
need for busy-wait loops in Download/InitiateDownload, as it's fairly clean
to wait on a channel with timeout.
* services: archiver: use defer to unlock now that we can
This previously carried the lock into the goroutine, but an intermediate
step just added the request to archiveInProgress outside of the new
goroutine and removed the need for the goroutine to start out with it.
* Revert "archiver: tests: combine numQueued declaration with next-instruction assignment"
This reverts commit bcc52140238e16680f2e05e448e9be51372afdf5.
Revert "archiver: tests: integrate new WaitForCompletion a little better"
This reverts commit 9fc8bedb5667d24d3a3c7843dc28a229efffb1e6.
Revert "archiver: tests: fix test by calling NewContext()"
This reverts commit 709c35685eaaf261ebbb7d3420e3376a4ee8e7f2.
Revert "archiver: tests: amend test to include WaitForCompletion()"
This reverts commit 75261f56bc05d1fa8ff7e81dcbc0ccd93fdc9d50.
* archiver: tests: first attempt at WaitForCompletion() tests
* archiver: tests: slight improvement, less busy-loop
Just wait for the requests to complete in order, instead of busy-waiting
with a timeout. This is slightly less fragile.
While here, reverse the arguments of a nearby assert.Equal() so that
expected/actual are correct in any test output.
* archiver: address lint nits
* services: archiver: only close the channel once
* services: archiver: use a struct{} for the wait channel
This makes it obvious that the channel is only being used as a signal,
rather than anything useful being piped through it.
* archiver: tests: fix expectations
Move the close of the channel into doArchive() itself; notably, before these
goroutines move on to waiting on the Release cond.
The tests are adjusted to reflect that we can't WaitForCompletion() after
they've already completed, as WaitForCompletion() doesn't indicate that
they've been released from the queue yet.
* archiver: tests: set cchan to nil for comparison
* archiver: move ctx.Error's back into the route handlers
We shouldn't be setting this in a service, we should just be validating the
request that we were handed.
* services: archiver: use regex to match a hash
This makes sure we don't try and use refName as a hash when it's clearly not
one, e.g. heads/pull/foo.
* routers: repo: remove the weird /archive/status endpoint
We don't need to do this anymore, we can just continue POSTing to the
archive/* endpoint until we're told the download's complete. This avoids a
potential naming conflict, where a ref could start with "status/"
* archiver: tests: bump reasonable timeout to 15s
* archiver: tests: actually release timedReq
* archiver: tests: run through inFlight instead of manually checking
While we're here, add a test for manually re-processing an archive that's
already been complete. Re-open the channel and mark it incomplete, so that
doArchive can just mark it complete again.
* initArchiveLinks: prevent default behavior from clicking
* archiver: alias gitea's context, golang context import pending
* archiver: simplify logic, just reconstruct slices
While the previous logic was perhaps slightly more efficient, the
new variant's readability is much improved.
* archiver: don't block shutdown on waiting for archive
The technique established launches a goroutine to do the wait,
which will close a wait channel upon termination. For the timeout
case, we also send back a value indicating whether the timeout was
hit or not.
The timeouts are expected to be relatively small, but still a multi-
second delay to shutdown due to this could be unfortunate.
* archiver: simplify shutdown logic
We can just grab the shutdown channel from the graceful manager instead of
constructing a channel to halt the caller and/or pass a result back.
* Style issues
* Fix mis-merge
Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com>
Co-authored-by: Lauris BH <lauris@nix.lv>
2020-11-07 21:27:28 +01:00
m . Post ( "/*" , repo . InitiateDownload )
2022-07-31 18:57:02 +02:00
} , repo . MustBeNotEmpty , dlSourceEnabled , reqRepoCodeReader )
2017-04-25 09:24:51 +02:00
2017-10-26 02:49:16 +02:00
m . Group ( "/branches" , func ( ) {
2023-07-22 13:47:06 +02:00
m . Get ( "/list" , repo . GetBranchesList )
2017-10-26 02:49:16 +02:00
m . Get ( "" , repo . Branches )
2019-01-18 01:01:04 +01:00
} , repo . MustBeNotEmpty , context . RepoRef ( ) , reqRepoCodeReader )
2017-10-26 02:49:16 +02:00
2019-11-15 03:52:59 +01:00
m . Group ( "/blob_excerpt" , func ( ) {
2021-01-26 16:36:53 +01:00
m . Get ( "/{sha}" , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . ExcerptBlob )
2023-07-07 07:31:56 +02:00
} , func ( ctx * context . Context ) gocontext . CancelFunc {
2022-02-05 19:26:12 +01:00
if ctx . FormBool ( "wiki" ) {
ctx . Data [ "PageIsWiki" ] = true
repo . MustEnableWiki ( ctx )
2023-07-07 07:31:56 +02:00
return nil
2022-02-05 19:26:12 +01:00
}
reqRepoCodeReader ( ctx )
if ctx . Written ( ) {
2023-07-07 07:31:56 +02:00
return nil
2022-02-05 19:26:12 +01:00
}
2023-07-07 07:31:56 +02:00
cancel := context . RepoRef ( ) ( ctx )
2022-02-05 19:26:12 +01:00
if ctx . Written ( ) {
2023-07-07 07:31:56 +02:00
return cancel
2022-02-05 19:26:12 +01:00
}
repo . MustBeNotEmpty ( ctx )
2022-06-20 12:02:49 +02:00
return cancel
2022-02-05 19:26:12 +01:00
} )
2019-11-15 03:52:59 +01:00
2023-07-20 14:41:28 +02:00
m . Get ( "/pulls/posters" , repo . PullPosters )
2021-01-26 16:36:53 +01:00
m . Group ( "/pulls/{index}" , func ( ) {
2023-07-03 03:00:28 +02:00
m . Get ( "" , repo . SetWhitespaceBehavior , repo . GetPullDiffStats , repo . ViewIssue )
2018-01-05 11:56:52 +01:00
m . Get ( ".diff" , repo . DownloadPullDiff )
2018-01-07 14:10:20 +01:00
m . Get ( ".patch" , repo . DownloadPullPatch )
2023-07-28 21:18:12 +02:00
m . Group ( "/commits" , func ( ) {
m . Get ( "" , context . RepoRef ( ) , repo . SetWhitespaceBehavior , repo . GetPullDiffStats , repo . ViewPullCommits )
m . Get ( "/list" , context . RepoRef ( ) , repo . GetPullCommits )
2023-11-14 19:24:20 +01:00
m . Get ( "/{sha:[a-f0-9]{4,40}}" , context . RepoRef ( ) , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . SetShowOutdatedComments , repo . ViewPullFilesForSingleCommit )
2023-07-28 21:18:12 +02:00
} )
feat(quota): Quota enforcement
The previous commit laid out the foundation of the quota engine, this
one builds on top of it, and implements the actual enforcement.
Enforcement happens at the route decoration level, whenever possible. In
case of the API, when over quota, a 413 error is returned, with an
appropriate JSON payload. In case of web routes, a 413 HTML page is
rendered with similar information.
This implementation is for a **soft quota**: quota usage is checked
before an operation is to be performed, and the operation is *only*
denied if the user is already over quota. This makes it possible to go
over quota, but has the significant advantage of being practically
implementable within the current Forgejo architecture.
The goal of enforcement is to deny actions that can make the user go
over quota, and allow the rest. As such, deleting things should - in
almost all cases - be possible. A prime exemption is deleting files via
the web ui: that creates a new commit, which in turn increases repo
size, thus, is denied if the user is over quota.
Limitations
-----------
Because we generally work at a route decorator level, and rarely
look *into* the operation itself, `size:repos:public` and
`size:repos:private` are not enforced at this level, the engine enforces
against `size:repos:all`. This will be improved in the future.
AGit does not play very well with this system, because AGit PRs count
toward the repo they're opened against, while in the GitHub-style fork +
pull model, it counts against the fork. This too, can be improved in the
future.
There's very little done on the UI side to guard against going over
quota. What this patch implements, is enforcement, not prevention. The
UI will still let you *try* operations that *will* result in a denial.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
2024-07-06 10:30:16 +02:00
m . Post ( "/merge" , context . RepoMustNotBeArchived ( ) , web . Bind ( forms . MergePullRequestForm { } ) , context . EnforceQuotaWeb ( quota_model . LimitSubjectSizeGitAll , context . QuotaTargetRepo ) , repo . MergePullRequest )
2022-06-11 16:44:20 +02:00
m . Post ( "/cancel_auto_merge" , context . RepoMustNotBeArchived ( ) , repo . CancelAutoMergePullRequest )
2020-01-17 07:03:40 +01:00
m . Post ( "/update" , repo . UpdatePullRequest )
2022-12-12 09:09:26 +01:00
m . Post ( "/set_allow_maintainer_edit" , web . Bind ( forms . UpdateAllowEditsForm { } ) , repo . SetAllowEdits )
2019-01-23 19:58:38 +01:00
m . Post ( "/cleanup" , context . RepoMustNotBeArchived ( ) , context . RepoRef ( ) , repo . CleanUpPullRequest )
2018-08-06 06:43:22 +02:00
m . Group ( "/files" , func ( ) {
2023-07-28 21:18:12 +02:00
m . Get ( "" , context . RepoRef ( ) , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . SetShowOutdatedComments , repo . ViewPullFilesForAllCommitsOfPr )
2023-11-14 19:24:20 +01:00
m . Get ( "/{sha:[a-f0-9]{4,40}}" , context . RepoRef ( ) , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . SetShowOutdatedComments , repo . ViewPullFilesStartingFromCommit )
m . Get ( "/{shaFrom:[a-f0-9]{4,40}}..{shaTo:[a-f0-9]{4,40}}" , context . RepoRef ( ) , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . SetShowOutdatedComments , repo . ViewPullFilesForRange )
2018-08-06 06:43:22 +02:00
m . Group ( "/reviews" , func ( ) {
2021-01-08 22:49:55 +01:00
m . Get ( "/new_comment" , repo . RenderNewCodeCommentForm )
2023-06-21 18:08:12 +02:00
m . Post ( "/comments" , web . Bind ( forms . CodeCommentForm { } ) , repo . SetShowOutdatedComments , repo . CreateCodeComment )
2022-12-12 09:09:26 +01:00
m . Post ( "/submit" , web . Bind ( forms . SubmitReviewForm { } ) , repo . SubmitReview )
2019-01-23 19:58:38 +01:00
} , context . RepoMustNotBeArchived ( ) )
2018-08-06 06:43:22 +02:00
} )
2017-09-30 06:04:16 +02:00
} , repo . MustAllowPulls )
2017-04-25 09:24:51 +02:00
2019-02-12 16:09:43 +01:00
m . Group ( "/media" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . SingleDownloadOrLFS )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . SingleDownloadOrLFS )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . SingleDownloadOrLFS )
2021-01-26 16:36:53 +01:00
m . Get ( "/blob/{sha}" , context . RepoRefByType ( context . RepoRefBlob ) , repo . DownloadByIDOrLFS )
2019-02-12 16:09:43 +01:00
// "/*" route is deprecated, and kept for backward compatibility
m . Get ( "/*" , context . RepoRefByType ( context . RepoRefLegacy ) , repo . SingleDownloadOrLFS )
} , repo . MustBeNotEmpty , reqRepoCodeReader )
2017-10-30 03:04:25 +01:00
m . Group ( "/raw" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . SingleDownload )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . SingleDownload )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . SingleDownload )
2021-01-26 16:36:53 +01:00
m . Get ( "/blob/{sha}" , context . RepoRefByType ( context . RepoRefBlob ) , repo . DownloadByID )
2017-10-30 03:04:25 +01:00
// "/*" route is deprecated, and kept for backward compatibility
m . Get ( "/*" , context . RepoRefByType ( context . RepoRefLegacy ) , repo . SingleDownload )
2019-01-18 01:01:04 +01:00
} , repo . MustBeNotEmpty , reqRepoCodeReader )
2017-10-30 03:04:25 +01:00
2022-06-16 05:33:23 +02:00
m . Group ( "/render" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . RenderFile )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . RenderFile )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . RenderFile )
m . Get ( "/blob/{sha}" , context . RepoRefByType ( context . RepoRefBlob ) , repo . RenderFile )
} , repo . MustBeNotEmpty , reqRepoCodeReader )
2017-10-30 03:04:25 +01:00
m . Group ( "/commits" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . RefCommits )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . RefCommits )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . RefCommits )
// "/*" route is deprecated, and kept for backward compatibility
m . Get ( "/*" , context . RepoRefByType ( context . RepoRefLegacy ) , repo . RefCommits )
2019-01-18 01:01:04 +01:00
} , repo . MustBeNotEmpty , reqRepoCodeReader )
2017-10-30 03:04:25 +01:00
2019-04-20 04:47:00 +02:00
m . Group ( "/blame" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . RefBlame )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . RefBlame )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . RefBlame )
} , repo . MustBeNotEmpty , reqRepoCodeReader )
2017-04-25 09:24:51 +02:00
m . Group ( "" , func ( ) {
m . Get ( "/graph" , repo . Graph )
2023-11-14 19:24:20 +01:00
m . Get ( "/commit/{sha:([a-f0-9]{4,64})$}" , repo . SetEditorconfigIfExists , repo . SetDiffViewStyle , repo . SetWhitespaceBehavior , repo . Diff )
m . Get ( "/commit/{sha:([a-f0-9]{4,64})$}/load-branches-and-tags" , repo . LoadBranchesAndTags )
2024-11-18 23:56:17 +01:00
m . Group ( "/commit/{sha:([a-f0-9]{4,64})$}/notes" , func ( ) {
m . Post ( "" , web . Bind ( forms . CommitNotesForm { } ) , repo . SetCommitNotes )
m . Post ( "/remove" , repo . RemoveCommitNotes )
} , reqSignIn , reqRepoCodeWriter )
2023-11-14 19:24:20 +01:00
m . Get ( "/cherry-pick/{sha:([a-f0-9]{4,64})$}" , repo . SetEditorconfigIfExists , repo . CherryPick )
2019-01-18 01:01:04 +01:00
} , repo . MustBeNotEmpty , context . RepoRef ( ) , reqRepoCodeReader )
2017-07-27 11:23:38 +02:00
2024-11-02 17:41:34 +01:00
m . Group ( "" , func ( ) {
m . Get ( "/rss/branch/*" , feed . RenderBranchFeed ( "rss" ) )
m . Get ( "/atom/branch/*" , feed . RenderBranchFeed ( "atom" ) )
} , repo . MustBeNotEmpty , context . RepoRefByType ( context . RepoRefBranch ) , reqRepoCodeReader , feedEnabled )
2023-04-25 16:08:29 +02:00
2017-10-30 03:04:25 +01:00
m . Group ( "/src" , func ( ) {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . Home )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . Home )
m . Get ( "/commit/*" , context . RepoRefByType ( context . RepoRefCommit ) , repo . Home )
// "/*" route is deprecated, and kept for backward compatibility
m . Get ( "/*" , context . RepoRefByType ( context . RepoRefLegacy ) , repo . Home )
} , repo . SetEditorconfigIfExists )
2024-02-25 11:58:23 +01:00
if ! setting . Repository . DisableForks {
m . Group ( "" , func ( ) {
m . Get ( "/forks" , repo . Forks )
} , context . RepoRef ( ) , reqRepoCodeReader )
}
2023-11-14 19:24:20 +01:00
m . Get ( "/commit/{sha:([a-f0-9]{4,64})}.{ext:patch|diff}" , repo . MustBeNotEmpty , reqRepoCodeReader , repo . RawDiff )
2021-04-10 02:26:08 +02:00
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2021-10-08 15:08:22 +02:00
m . Post ( "/{username}/{reponame}/lastcommit/*" , ignSignInAndCsrf , context . RepoAssignment , context . UnitTypes ( ) , context . RepoRefByType ( context . RepoRefCommit ) , reqRepoCodeReader , repo . LastCommit )
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}/{reponame}" , func ( ) {
2024-02-26 09:22:51 +01:00
if ! setting . Repository . DisableStars {
2024-05-14 17:41:03 +02:00
m . Get ( "/stars" , context . RepoRef ( ) , repo . Stars )
2024-02-26 09:22:51 +01:00
}
2024-05-14 17:41:03 +02:00
m . Get ( "/watchers" , context . RepoRef ( ) , repo . Watchers )
m . Group ( "/search" , func ( ) {
m . Get ( "" , context . RepoRef ( ) , repo . Search )
if ! setting . Indexer . RepoIndexerEnabled {
m . Get ( "/branch/*" , context . RepoRefByType ( context . RepoRefBranch ) , repo . Search )
m . Get ( "/tag/*" , context . RepoRefByType ( context . RepoRefTag ) , repo . Search )
}
} , reqRepoCodeReader )
} , ignSignIn , context . RepoAssignment , context . UnitTypes ( ) )
2017-04-25 09:24:51 +02:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{username}" , func ( ) {
m . Group ( "/{reponame}" , func ( ) {
2017-04-25 09:24:51 +02:00
m . Get ( "" , repo . SetEditorconfigIfExists , repo . Home )
2021-05-09 23:50:06 +02:00
} , ignSignIn , context . RepoAssignment , context . RepoRef ( ) , context . UnitTypes ( ) )
2017-04-25 09:24:51 +02:00
2021-01-26 16:36:53 +01:00
m . Group ( "/{reponame}" , func ( ) {
m . Group ( "/info/lfs" , func ( ) {
2021-06-06 01:59:27 +02:00
m . Post ( "/objects/batch" , lfs . CheckAcceptMediaType , lfs . BatchHandler )
m . Put ( "/objects/{oid}/{size}" , lfs . UploadHandler )
m . Get ( "/objects/{oid}/{filename}" , lfs . DownloadHandler )
m . Get ( "/objects/{oid}" , lfs . DownloadHandler )
m . Post ( "/verify" , lfs . CheckAcceptMediaType , lfs . VerifyHandler )
2017-11-28 21:58:37 +01:00
m . Group ( "/locks" , func ( ) {
m . Get ( "/" , lfs . GetListLockHandler )
m . Post ( "/" , lfs . PostLockHandler )
m . Post ( "/verify" , lfs . VerifyLockHandler )
2021-01-26 16:36:53 +01:00
m . Post ( "/{lid}/unlock" , lfs . UnLockHandler )
2021-06-06 01:59:27 +02:00
} , lfs . CheckAcceptMediaType )
2017-04-25 09:24:51 +02:00
m . Any ( "/*" , func ( ctx * context . Context ) {
2018-01-10 22:34:17 +01:00
ctx . NotFound ( "" , nil )
2017-04-25 09:24:51 +02:00
} )
2021-06-06 01:59:27 +02:00
} , ignSignInAndCsrf , lfsServerEnabled )
2021-01-26 16:36:53 +01:00
2023-11-02 15:14:33 +01:00
gitHTTPRouters ( m )
2017-04-25 09:24:51 +02:00
} )
} )
[FEAT] Repository flags
This implements "repository flags", a way for instance administrators to
assign custom flags to repositories. The idea is that custom templates
can look at these flags, and display banners based on them, Forgejo does
not provide anything built on top of it, just the foundation. The
feature is optional, and disabled by default. To enable it, set
`[repository].ENABLE_FLAGS = true`.
On the UI side, instance administrators will see a new "Manage flags"
tab on repositories, and a list of enabled tags (if any) on the
repository home page. The "Manage flags" page allows them to remove
existing flags, or add any new ones that are listed in
`[repository].SETTABLE_FLAGS`.
The model does not enforce that only the `SETTABLE_FLAGS` are present.
If the setting is changed, old flags may remain present in the database,
and anything that uses them, will still work. The repository flag
management page will allow an instance administrator to remove them, but
not set them, once removed.
Signed-off-by: Gergely Nagy <forgejo@gergo.csillger.hu>
(cherry picked from commit ba735ce2228f8dd7ca105e94b9baa1be058ebe37)
(cherry picked from commit f09f6e029b4fb2714b86cd32dc19255078ecc0ee)
(cherry picked from commit 2f8b0414892f6099f519bda63a9e0fbc8ba6cfc7)
(cherry picked from commit d3186ee5f41fac896c7d2341402fcd39dd250bf1)
2024-01-04 14:28:19 +01:00
if setting . Repository . EnableFlags {
m . Group ( "/{username}/{reponame}/flags" , func ( ) {
m . Get ( "" , repo_flags . Manage )
m . Post ( "" , repo_flags . ManagePost )
} , adminReq , context . RepoAssignment , context . UnitTypes ( ) )
}
2017-04-25 09:24:51 +02:00
// ***** END: Repository *****
m . Group ( "/notifications" , func ( ) {
m . Get ( "" , user . Notifications )
2022-09-29 21:09:14 +02:00
m . Get ( "/subscriptions" , user . NotificationSubscriptions )
m . Get ( "/watching" , user . NotificationWatching )
2017-04-25 09:24:51 +02:00
m . Post ( "/status" , user . NotificationStatusPost )
2017-12-07 06:52:57 +01:00
m . Post ( "/purge" , user . NotificationPurgePost )
2022-04-07 20:59:56 +02:00
m . Get ( "/new" , user . NewAvailable )
2017-04-25 09:24:51 +02:00
} , reqSignIn )
2018-07-28 02:19:01 +02:00
if setting . API . EnableSwagger {
2021-06-09 01:33:54 +02:00
m . Get ( "/swagger.v1.json" , SwaggerV1Json )
2019-08-26 13:33:06 +02:00
}
2023-04-03 12:06:57 +02:00
if ! setting . IsProd {
m . Any ( "/devtest" , devtest . List )
2023-06-14 10:01:37 +02:00
m . Any ( "/devtest/fetch-action-test" , devtest . FetchActionTest )
2023-04-03 12:06:57 +02:00
m . Any ( "/devtest/{sub}" , devtest . Tmpl )
}
2021-12-22 11:39:28 +01:00
m . NotFound ( func ( w http . ResponseWriter , req * http . Request ) {
2023-05-23 03:29:15 +02:00
ctx := context . GetWebContext ( req )
2021-12-22 11:39:28 +01:00
ctx . NotFound ( "" , nil )
} )
2017-04-25 09:24:51 +02:00
}